Enforced Blacklist Whitelist for Android and Samsung Knox
Overview
Silverback offers two ways to influence or track installed applications on Samsung Knox devices. The fist one, the Silverback blacklist is a method that does not interfere directly with the device and Silverback will perform here certain actions based only on the list of installed applications that devices send to the management system if an unwanted application is installed or detected on the device.
Another method is the Enforced Blacklist/Whitelist, where the management actively influences the device with a restriction and configures it in such a way that an array of unwanted or explicitly wanted applications become unusable/usable. Please note the following support matrix:
| Android | Samsung Knox | |
|---|---|---|
| Enforced Blacklist | Supported for Device Owner | Supported for Device Owner and on Personal Area when devices are equipped with a Work Profile. |
| Enforced Whitelist | Not supported | Supported for Device Owner and on Personal Area when devices are equipped with a Work Profile. |
Within this guide we want to demonstrate with a Samsung Device how to configure first the enforced blacklisting that allows you to remove blacklisted apps from your managed devices within your organization. The configuration process is equal to Android devices and with this policy, you can either remove apps which are downloaded by the user from the Google Play Store or from the Managed Play Store on Android Enterprise devices, but also deactivates apps which are already bundled and delivered on the device after power on the first time. The second part of this guide covers the enforced whitelisting method that will prevent users from installing non listed applications.
Please note that the blacklist behavior on Samsung Knox devices and Android devices is slightly different. While the behavior on Samsung Knox is more of a proactive prevention of app installation, etc., the behavior on Android is more of a reactive one, where the app is disabled by the Companion on the next sync after installation. Please also note that the Knox Service Plugin (and presumably other OEM configuration vendors) also provides functionality to configure allow or block lists for applications, and is also available as a means of choice.
While using Device Owner mode devices, this policy in general ensures to keep your organization policy aligned with non allowed applications on corporate devices when you are not preventing with the Allow Modify Accounts restriction to add personal Google Accounts or when you have enabled the Allow Access to All Apps in Google Play Store restriction. When assigning the enforced blacklist or whitelist to Samsung devices, ensure to exclude true personal devices as they should be always able to install and use applications in their personal area. Otherwise and according to the current architecture, the black- or whitelist will take affect on Samsung Knox devices in the personal area. In case you provide corporate owned Samsung Knox devices that are not enrolled as device owner to your users and equip them with a work profile, it might be useful that the policy will take affect in the personal area of the devices.
Take into account that when you are equipping devices with a work profile, it is ensured that only Managed Play applications can be installed in the work section if the Allow Access to All Apps in Google Play Store is not enabled. The same applies to devices enrolled with the device owner mode and if the Allow Modify Account restriction is disabled, users on device owner devices will not be able to add any Google Account, which prevents installing applications from Google Play and allows only to install applications made available in the Managed Play Store.
Enforced Blacklist/Whitelist Configuration
Before we start with enforced application blacklist, you can consider to review the Application Black- and Whitelisting guide to get a first an overview. To configure the enforced application blacklist for Android or Samsung Knox devices, please perform the following steps:
Create a Tag
- Open your Silverback Management Console
- Login as an Administrator
- Create a new Tag with enabled Policy Feature and Samsung Knox as device type
Configure Applications Blacklist
- Navigate to Policy
- Select Application Blacklist
- From here you can add your applications in the package name format
Get Package Names
- Navigate to the App Portal Tab
- Select Samsung Knox
- Press New Application
- Select the Search Icon
- Enter the application name in the search field, e.g., SmartThings
- Select the application
- Press Select
- Now you can note down the Bundle ID from the Name field
- For SmartThings the Bundle ID is com.samsung.android.oneconnect
- For Samsung Calendar the Bundle ID is com.samsung.android.calendar
Additionally, you can use third party applications like this Package Name Viewer app to find the package names as some applications might not be available in the search.
Add Package Names
- Navigate back to your previously used Tag
- In the blacklist section, enter now your first package name, e.g. com.samsung.android.oneconnect
- Press Add
- Enter now your second package name, e.g. com.samsung.android.calendar
- Repeat this for all desired packages
Enable Lockdown Policy
- Navigate now from the Application List to the Lockdown section
- Here you have several lockdown options that will be checked periodically against your corporate policies.
- Enable Enforce Application Blacklist
- Select Force
- Additionally, you can enable the Alert Administrator checkbox. In case a policy violation is detected, administrators with the enabled Receive Email Alerts option will get informed about policy violations.
- Press Save
- Confirm with OK
Assign Tag
After enabling the Lockdown Policy with the configured Application Blacklist, it is time to assign the Tag. As always, you have now three different options to assign the Tag to your devices:
- Navigate in the Tag to Definition and use the Associated Devices button to attach devices
- Navigate in the Tag to Definition and enable the Auto Population
- Navigate to Devices and use the assign Tag button and select the Tag and press save
Review Device
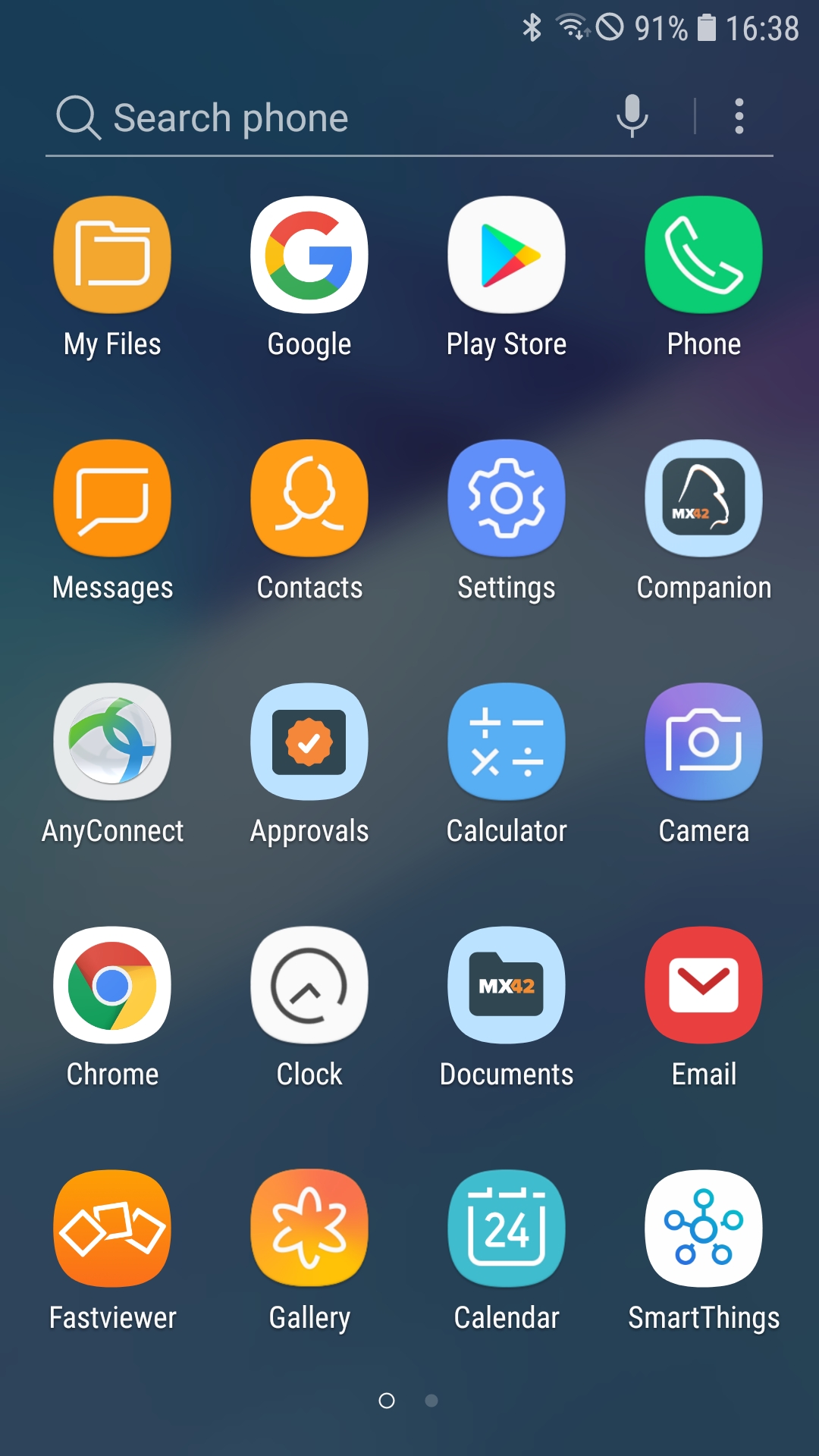
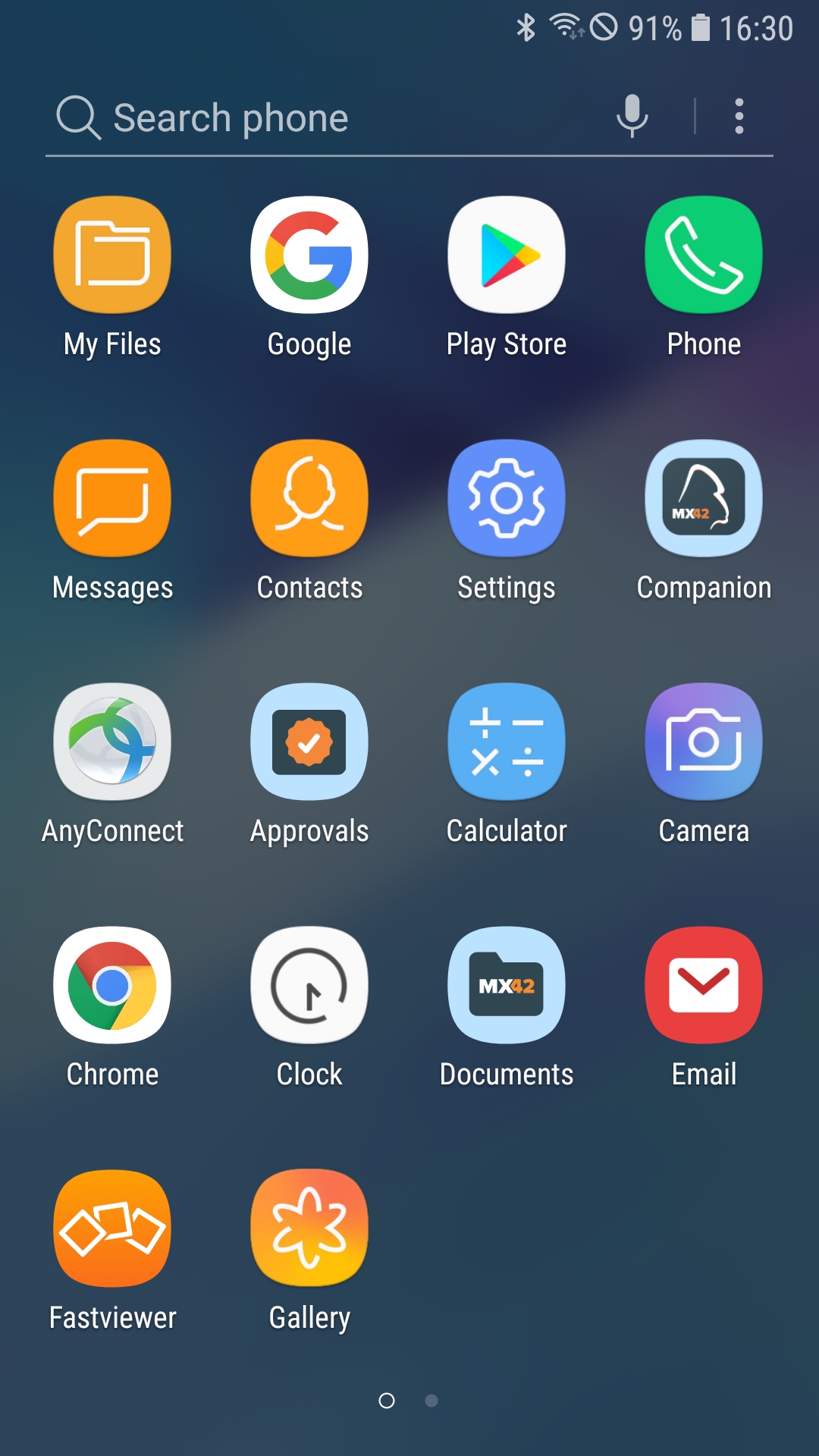
After assigning the tag, you can open the Matrix42 Companion application on the device and perform a manual synchronization or press the Refresh button from the Device Overview to speed up the process. Once the Companion application has successfully synchronized, the blacklisted configured applications should disappear from the device, as shown below. In addition, you can open the Companion application, open the menu, and under Profiles you will see an entry for the Blocked Application List profile. You can check the assigned application list by pressing the three dots and Details.
| Calendar and SmartThings are usable | Calendar and SmartThings disappeared from the device. |
 |
 |
On Samsung Knox devices, if you try to install an application that is part of the blacklisted application list, you will be notified that a security policy is preventing the installation. On Android devices, users will be able to install the application until the next Companion performs a sync, after which the recently installed application will be disabled.
Configure Application Whitelist
After we configured and reviewed the Application Blacklist option, we want to use the same Tag and switch to the Application Whitelist option, which is available for Samsung Knox devices. For this, we need to add our applications to the tag and switch the Lockdown options from blacklist to whitelist.
Add whitelisted applications
- Switch back to your previously used tag
- Enable under definition the App Feature for this tag
- Navigate to Apps
- Select Assign More Apps
- Select now applications from the available app list
- Press Add Selected Apps
Switch Lockdown Policy
- Navigate to Policy
- Select Lockdown
- Now disable the Enforce Application Blacklist option
- And enable the Application Whitelist option
- Select Force, which is available for Samsung Knox devices
- Additionally, enable the Alert Administrator checkbox. In case a policy violation is detected, administrators with the enabled Receive Email Alerts option will get informed about policy violations.
- Press Save
- Confirm with OK
Refresh the device
- As the tag should be still applied to your device, you can either navigate to Definition and press Push to Devices or
- Perform a device refresh from the Devices Tab
Review the Device
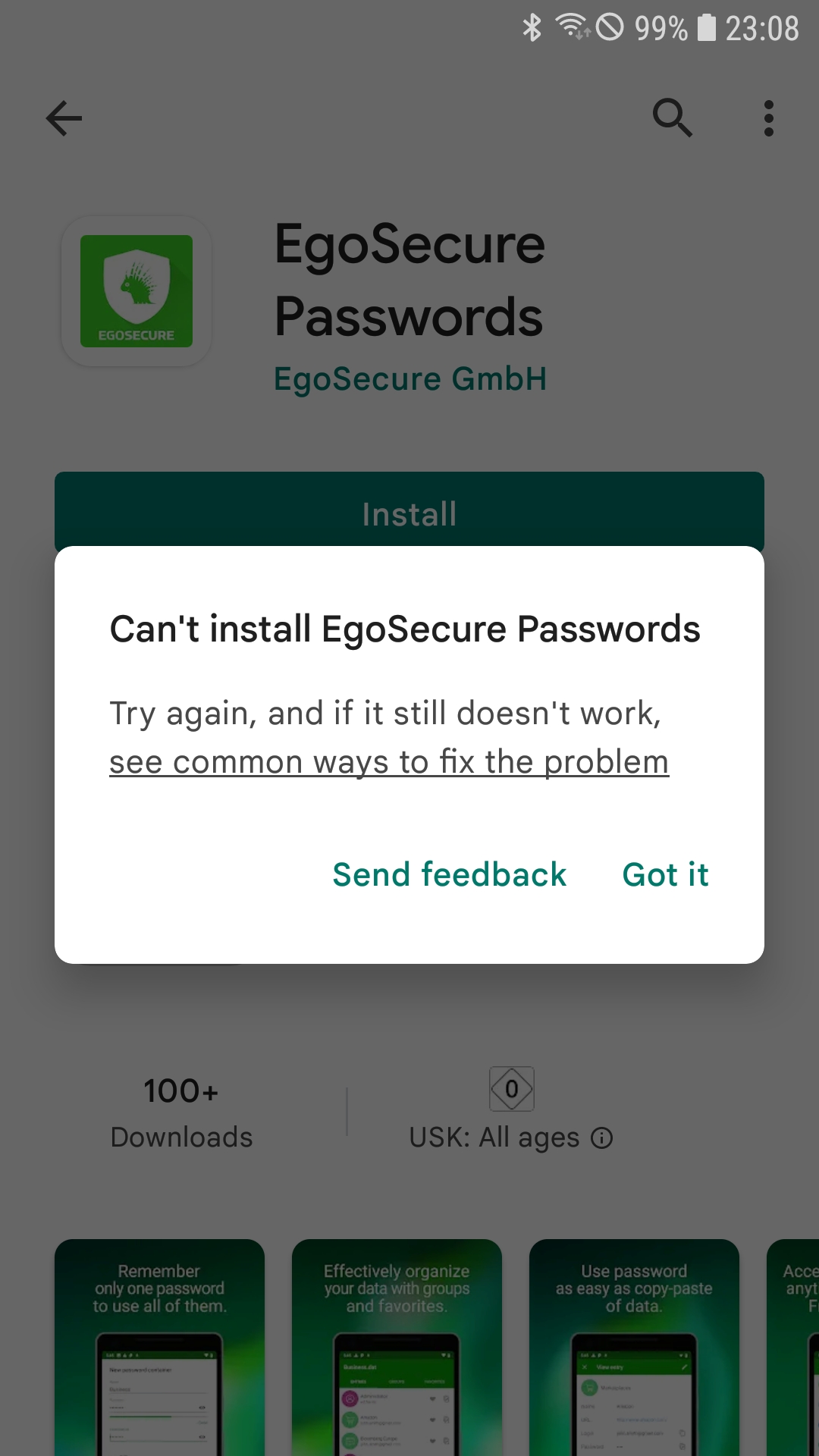
Contrary to what you probably now expected, not all apps that are in the banned list are now disabled or uninstalled on the device. Instead of deactivating existing applications on the device, the enforced whitelist feature is preventing the installation of applications and already installed won't be touched until they will be uninstalled from the user. To check the working state of the enforced whitelist, you can try now to install an application from Google or Managed Play that you have not added into the Tag. After downloading the application, the Play store will try to start the installation, but users will see a notification as shown in the following screenshots
| Whitelisted applications can be installed | Non whitelisted installation ran into this information popup |
 |
 |
Additional Information
- You can use the enforced Blacklist and Whitelist in a very powerful combination to ensure corporate compliance as the Blacklist will disable existing apps on devices and the Whitelist enforces the restriction to install only whitelisted apps only. If you want to run the Blacklist and Whitelist in parallel, you need to activate and use each feature in separated Tags.
- In case you have some duplicates in the whitelist violation list, it might be that you have either the application multiple times in your App Portal, e.g. as a different application type or that applications might have the same or similar parts of the name. E.g., if you have the Knox Deployment and the Knox Service Plugin application in your App Portal, this app will might be shown twice as it contains both times the part Knox. This behavior should be fixed in Silverback 23.0 Update 1 and should not occur in newer versions.