Backup Policy for iOS and iPadOS devices
Overview
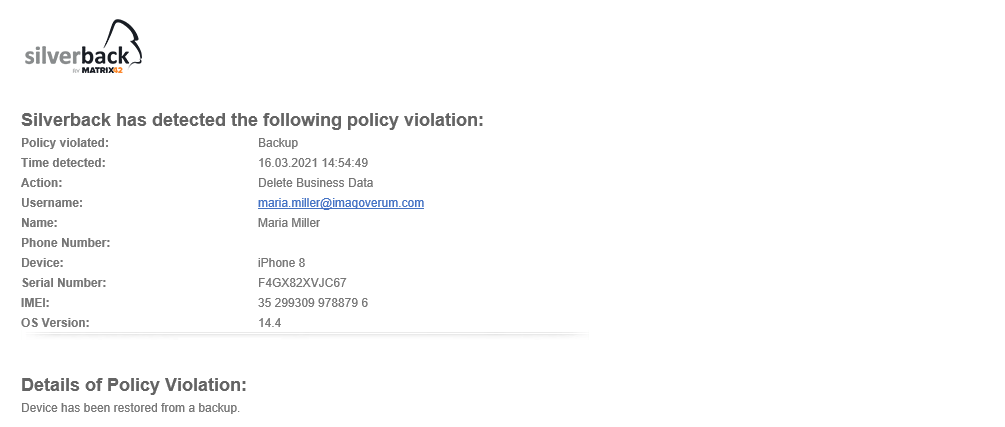
Administrators have the ability to allow or deny iOS or iPadOS devices to be restored from backup and maintain access to corporate information. By default, this setting is set to allowed, as Silverback will automatically prevent the most common security threat with restoring backups by default if your leaver process contains performing a Factory Wipe or Delete Business Data for the leaver’s device. If a leaver’s device is not under managed or blocked in Silverback and the former employee subsequently tries to restore a backup that was made during their time with you that contains the recent MDM profile, Silverback will automatically remove the profile when the device tries to communicate again with Silverback after the restore process and this will be additionally indicated by default with a Notification and a Log entry, as shown below.
If you want to prevent users from restoring backups while the device is in a managed or blocked state and you are not utilizing the Device Enrollment Program, you can disable the option under Admin > Backup. If the Allow Restore from Backup option is disabled and devices will be enrolled with the Device Enrollment Program, they will be removed by default in Silverback after the Setup Wizard is finished as the empirically detection of a restored backup hits the indicator when the second token update applies during the device enrollment for Device Enrollment Program devices.
Please keep also in mind that there are certain situations where a restore from backup is required or desired, such as major iOS upgrades or by receiving a new iPhone or iPad and the convenience for a phone migration. In case your organizations security policy explicitly denies performing and restoring backups, the second part of this knowledge base article contains a configuration for how to prevent users in general to generate iCloud backups and or connecting the device to a macOS device to perform a backup. In addition, we recommend in addition to review the Backup and Device Migration Principles for Apple Devices article for additional information about backups, especially when you are migration from a different solution to Silverback.
Configuration
The Allow Restore from Backup option is located under Admin > Backup Policy and can be enabled or disabled. When a device is restored from backup and this setting is disabled, Silverback will detect the restored backup and send a command to the device for deleting business data.
| Setting | Options | Description |
|---|---|---|
| Allow Restore from Backup | Enabled or Disabled |
Will prevent or allow that users can restore their Silverback device connection with a backup. |
Notification
When a restore from a backup has been detected, Administrators with enabled Receive Email Alerts option will receive the following E-Mail Notification:
Log Information
Additionally, the following message is shown in the Logs section
|
1313885 |
28 Nov 2018 06:45:06 AM |
SilverbackMDM.SilverBack.Common.MdmProtocols.Http401Exception: Restore from backup is not allowed, therefore Send 401 to remove mdm base profile. |
Prevent Backups
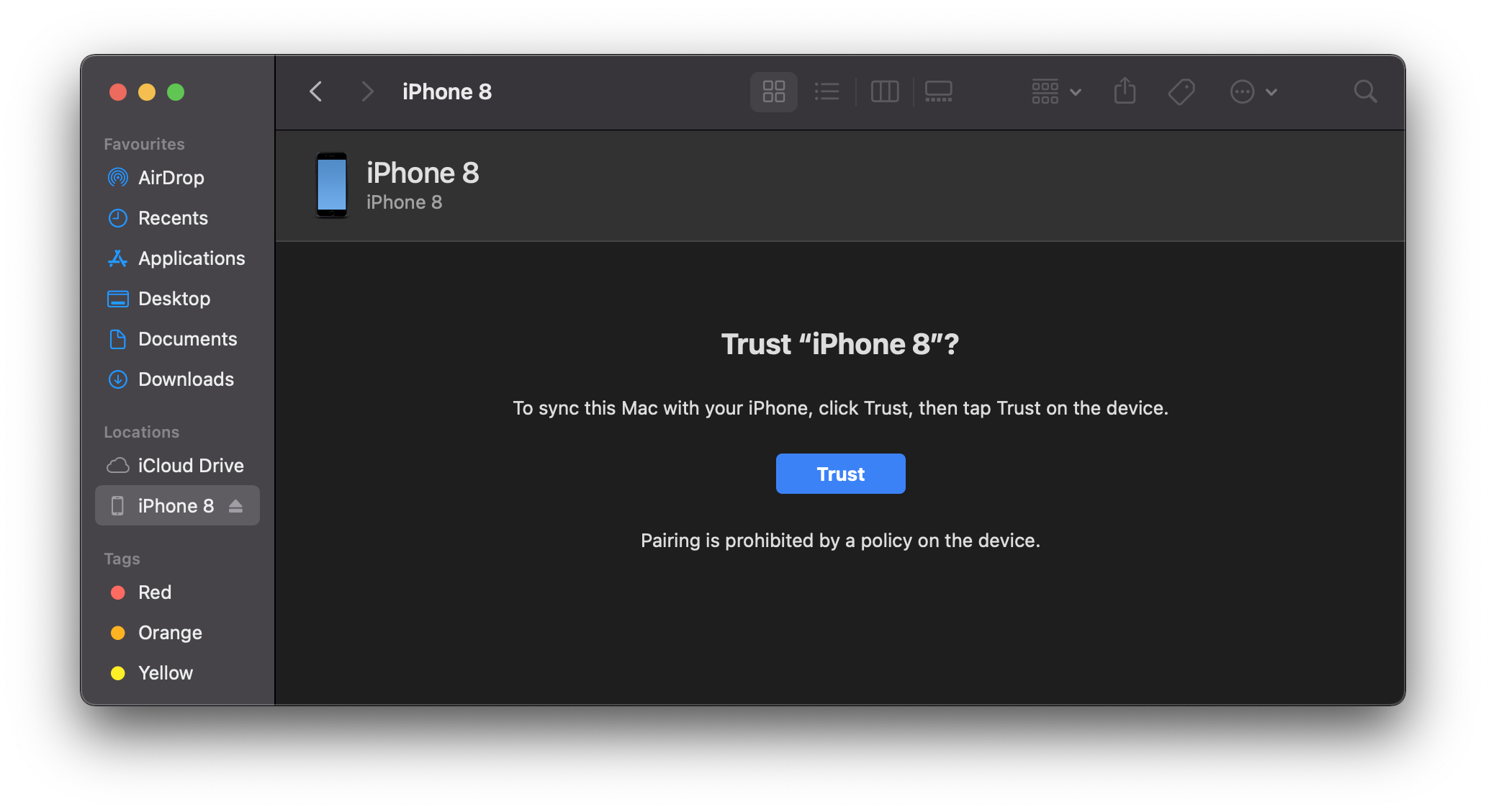
To prevent the backup creation on iOS and iPadOS devices, you can utilize the Allow iCloud Backup and Allow Host Pairing (supervised) restriction. By disabling the Allow iCloud Backup setting, the iCloud Backup option in iOS or iPadOS will be deactivated and made hidden. If you disable the Allow Host Pairing setting, the macOS device will show an information that paring is prohibited by a policy on the device after pressing the trust button. The following screenshots will display the behavior changes on managed devices with the configured restrictions.
| Allowed iCloud Backup | Disallowed iCloud Backup |
| Disallowed Host Pairing | |
 |
|
Host Pairing with Supervision Identities
If you disallowed the Host Pairing restriction for iOS and/or iPadOS devices and you are utilizing the Device Enrollment Program , you can export your Supervision Identity from the Apple Configurator and add the *.crt output as a supervising certificate to your General Settings within the Device Enrollment Program settings in your Silverback Management Console. This ensures that enrolled devices with the Device Enrollment Program can be paired with macOS devices that have the Supervision Identity (Certificate) in place.
- Open your Apple Configurator
- Click Apple Configurator in the upper navigation
- Select Preferences and navigate to Organizations
- Select your organization from the list and click the Gear button
- Choose Export Supervision Identity
- Select as Format Unencrypted DER and press save
Added supervising certificates are applied to all additional profiles by default.
It might happen that devices might show at the first try that Pairing is prohibited as shown in the screenshot above, but when you disconnect and connect the device again, it will work.