Platform Single Sign-On on macOS devices
Overview
Platform Single Sign-On (Platform SSO) enables developers to create SSO extensions that integrate with the macOS login window, allowing users to synchronize their local account credentials with an identity provider (IdP). This ensures that the local and cloud passwords remain aligned automatically. Additionally, users can conveniently unlock their Mac using Touch ID or an Apple Watch. The Platform Single Sign-on configuration is part of the Extensible Single Sign-On Profile on macOS devices, which is highlighted in the Streamline User Authentication with Extensible Single Sign-On. In this guide, we build on the configuration and experience from the Extensible Single-On configuration and will extend it with the Platform SSO option for Microsoft Entra ID and the password authentication method. Get in touch with your Identity Provider and request their options, requirements, and documentation about their Platform SSO support.
Requirements and Preparation
Requirements
Platform SSO requires the following:
- Silverback 24.0 Update 3
- macOS 13 or later
- Support from the IdP for the Platform SSO authentication protocol
- One of two supported authentication methods:
- Password authentication: With this method, a user authenticates with a local password or an IdP password.
- Authentication with a Secure Enclave–backed key: With this method, a user who logs in to their Mac can use a Secure Enclave–backed key to authenticate with the IdP without a password. The Secure Enclave key is set up with the IdP during the user registration process.
Preparation
- Before you start, review Streamline User Authentication with Extensible Single Sign-On
- Ensure you have finished the following preparation steps:
- Contacted your Identity Provider and/or reviewed their documentation
- Added and deployed the application to your macOS device
- Created a Tag with the required Extensible Single Sign-On profile
Enable and Configure Platform SSO
At the start of this chapter, we assume that you have already configured an existing Extensible Single Sign-On profile and are familiar with its behaviour. In the course of this article, we will extend this profile to include the Platform SSO configuration. If you are already using this profile productively, we recommend that you first create a new tag and copy the existing values from the old tag before proceeding. Once everything is configured and working as required, you can update your production tag.
Enable Platform SSO in your Extensible Single Sign-On Profile
- Navigate to your Silverback Management Console
- Select Tags and locate your Tag with the Extensible Single Sign-On profile
- Press the Edit button
- Select Profile and ensure that your are in the macOS tab
- Select Extensible Single Sign-On and press the Edit button
- Locate on the bottom the Platform SSO section and enable the checkbox
- You will see now all available Platform SSO configuration options that you can configure based on your requirements and availability
- Now, you can add your specific Platform SSO configuration accordingly and press Save
Minimum Configuration for Microsoft Entra ID
Next to the Required Configuration for Microsoft Enterprise SSO, we will need the following configuration values for the purpose of the password authentication method:
- Authentication method: Password
- Account Name: preferred_username
- Full name: name
- Registration token:
{{DEVICEREGISTRATION}}
Overall Platform SSO Settings
Depending on the Identity Provider's capabilities or additional requirements beyond the highlighted password authentication method, you may need to configure additional settings, which are highlighted below:
| Setting | Options | Description |
|---|---|---|
| Authentication method |
|
The Platform SSO authentication method to use with the extension. Requires that the SSO Extension also support the method. |
| Registration token |
e.g. {{DEVICEREGISTRATION}}
|
The token this device uses for registration with Platform SSO. Available in macOS 13 and later. |
| FileVault policy |
|
The policy to apply when using Platform SSO at FileVault unlock on Apple Silicon Macs. Applies when the Authentication method is set to Password. Available in macOS 15 and later. |
| Login policy |
|
The policy to apply when using Platform SSO at the login window. Applies when the Authentication method is set to Password. Available in macOS 15 and later. |
| Unlock policy |
|
The policy to apply when using Platform SSO at screensaver unlock. Applies when the Authentication method is set to Password. Available in macOS 15 and later. |
| Login frequency | e.g. 64800 | The duration, in seconds, until the system requires a full login instead of a refresh. The default value is 64,800 (18 hours). The minimum value is 3600 (1 hour). |
| Account display name | e.g. Imagoverum Corporate Account | The display name for the account in notifications and authentication requests. |
| Use shared device keys |
|
If enabled, the system uses the same signing and encryption keys for all users. |
| Enable create user at login |
|
Enables creating new users at the login window with an Authentication method of either Password or Smart |
| Enable authorization |
|
Enables using identity provider accounts at authorization prompts. Requires that Use shared device keys is enabled. The system assigns groups using Administrator |
| User authorization mode |
|
The permission to apply to an account each time the user authenticates.
|
| New user authorization mode |
|
The permission to apply to newly created accounts at login.
|
| Account name | e.g. preferred_username | Handles the Token to User Mapping for Account Name and represents the claim name to use for the user’s account name. |
| Full name | e.g. name | Handles the Token to User Mapping for Account Name and represents the claim name to use for the user’s full name. |
| Non platform SSO accounts | e.g. admin | The list of local accounts that aren’t subject to the File |
| Administrator groups | At the time of implementation and the creation of this article, no further information could be found as an example of this configuration due to the lack of support from the available identity providers. This might change in future. | The list of groups to use for administrator access. The system requests membership during authentication. |
| Additional groups | The list of created groups that don’t have administrator access. | |
| Authorization groups | The pairing of Authorization Rights to group names. The system updates the Authorization Right to use the group when used. |
Assign the Tag
Depending on where you started from, your Tag with the updated profile is already assigned to the corresponding (test) devices or the Tag still needs to be assigned. If the Tag is already assigned to the test device, you can go to Definition and use the Push to Devices button. As always, you can then track the profile installation via the Pending Commands in the device overview of a device.

If the Tag is not yet assigned to a device, you have as usual multiple options to assign the Tag. You can either navigate back to Definition tab inside the Tag and press the Associated Devices button to Attach More Devices or you can navigate to the Devices tab and press the Tag button in the Actions column. After you verified the Profile with one or more test devices, you can also enable the Auto Population for the Tag. For additional information, please refer to Tags Guide Part I: Create and Deploy.
Review User Experience
Review Profile Installation
- On your macOS device, open System Settings
- Select General and Device Management
- Locate the Silverback Extensible Single Sign-On Profile
- Perform a double-click and scroll down to the Platform SSO section
- From here you can see your applied settings
Registration Process
Once the Enterprise Portal application has been successfully deployed and installed on the device, and the Extensible Single Sign-On profile has been applied to the device, the user experience will be as follows:
- A notification will appear in the Notification Area
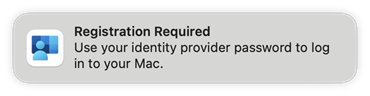
The notification should pop up every 15 minutes after the configuration installation. You can log out and back into the user to trigger a popup. In addition, you can go to System Settings > Users & Groups > Click Edit next to Network account server > Click Register next to Mac SSO Extension under Platform Single Sign-on. The notification will most likely not be displayed when the screen is being recorded or during screen monitoring.
- By opening the Notification or pressing the Register button, the Platform Single Sign-On Registration screen is shown:
- Pressing Continue will prompt the user to enter their current macOS password
- After entering the current password and pressing Unlock, the user is taken to the Microsoft Entra ID login page
- The user now logs in with their organization account and completes Multi-Factor Authentication (MFA) if required
- As a final step, the user will see a new Please sign in to your Microsoft Entra account pop-up
- Here, the Microsoft Entra ID username is already pre-populated and the user can complete the process by entering the corresponding Entra ID password and clicking Sign In
- The Registration Complete pop-up indicates that the registration is successful
Review new Account settings
- Open System Settings
- Navigate to Users & Groups
- Locate the current User Account and press the Information button
- Below the basic information, you should see now a new Platform Single Sign-on section
- Here users can either Repair the Registration or Authenticate again in case for Troubleshooting
- Press OK or Cancel

Logout and Login with IdP Credentials
- Press the Apple menu icon on the top left
- Select Log Out
- If you don’t want app windows that are open to reopen when you log back in, deselect “Reopen windows when logging back in”.
- Press Log Out
- Now login instead of the previously used macOS password with the password from Microsoft Entra ID
Assistance and Additional Notes
- To prevent conflicts with password restrictions, avoid deploying a Passcode profile alongside Platform Single Sign-On. Instead, manage all password configurations centrally in Entra as the single source of truth.
- Take a look into the Keychain (by using the Spotlight Search), take a search by "CompanyPortal" and "Refreshtoken" and review the results. You may need to remember the location in case of issues.
- Review the overview of useful external links and assistance on the topic of Platform SSO: