Windows 10/11 Diagnostics and Logs
Windows 10/11 Diagnostics and Logs
Windows 10 and Windows 11 devices allowing several methods to collect diagnostics and logs locally or remotely. Collecting logs locally is intended for first and second level (remote) support scenarios and can be used e.g. to review the configuration service provider API and which configurations has been applied on your managed devices. Help Desk employees can guide users to collect these reports or perform the report creations with users together in a remote session. The second option is using the remote Diagnostic Archive functionality which is used to trigger devices to gather troubleshooting data into a zip archive file and upload that archive to an Azure Blob storage. This option is designed for ad-hoc troubleshooting scenarios, such as an administrator investigating an app installation failure using a collection of event log events, registry values, and app or operating system log files. In this case, administrators can initiate the process remotely with Silverback.
Options
Collect Logs locally
Collecting logs locally is intended for first and second level (remote) support scenarios and can be used e.g. to review the configuration service provider API and which configurations has been applied on your managed devices. Help Desk employees can guide users to collect these reports or perform the report creations with users together in a remote session.
Download and Export Report
- Start with your managed Windows 10/11 device
- Open Settings
- Navigate to Accounts
- Select Access work or school
- Click your work or school account
- Click Info
- Scroll down and press Create Report
- A window opens that shows the path to the log files
- Click Export
- Open File Explorer and navigate to c:\Users\Public\Documents\MDMDiagnostics to review the report
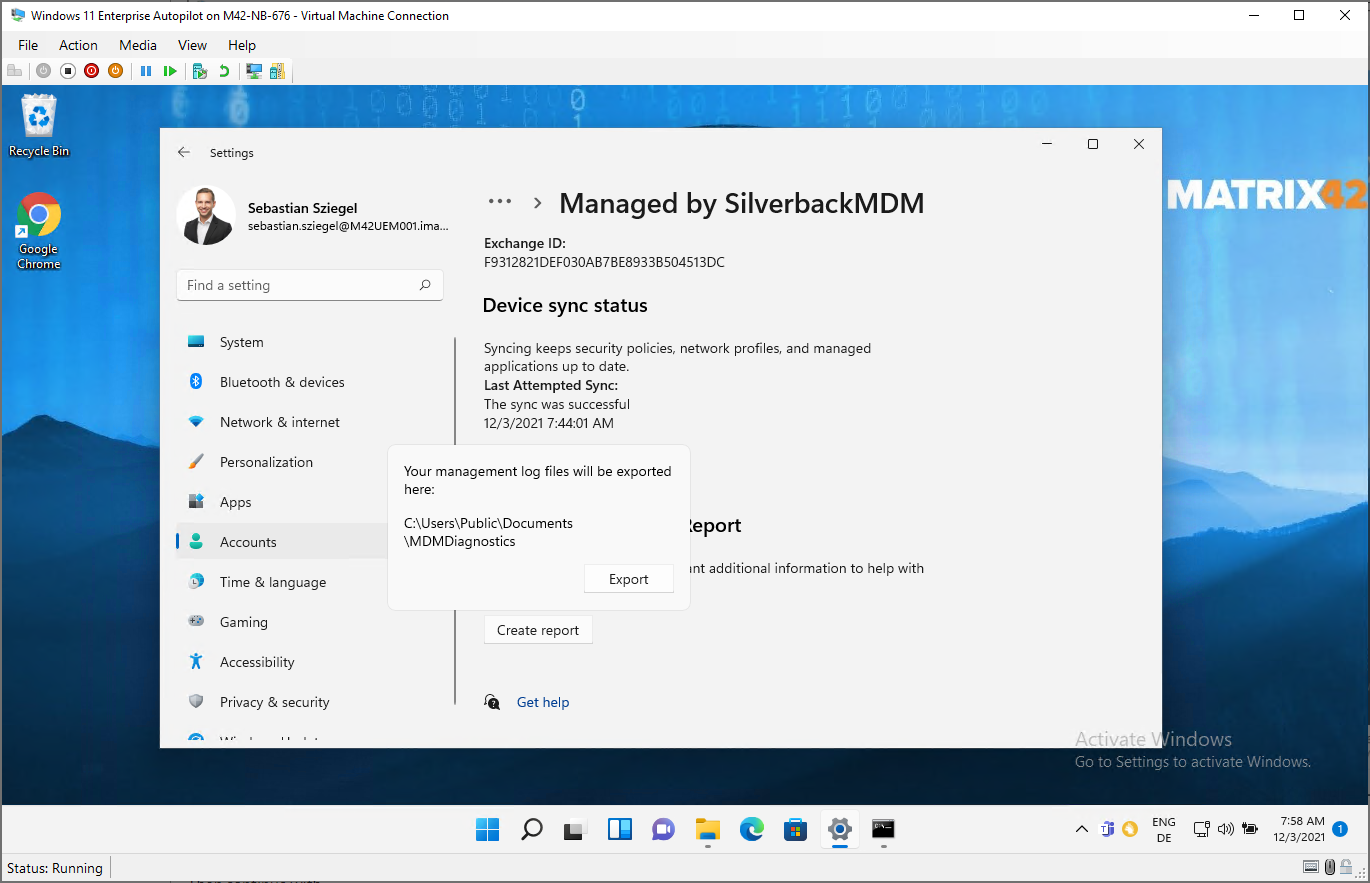
Review Report
- Double-click the MDMDiagReport.html
- After opening you can review logs from different sections: Device, Connection, Managed and Unmanaged Policies etc.
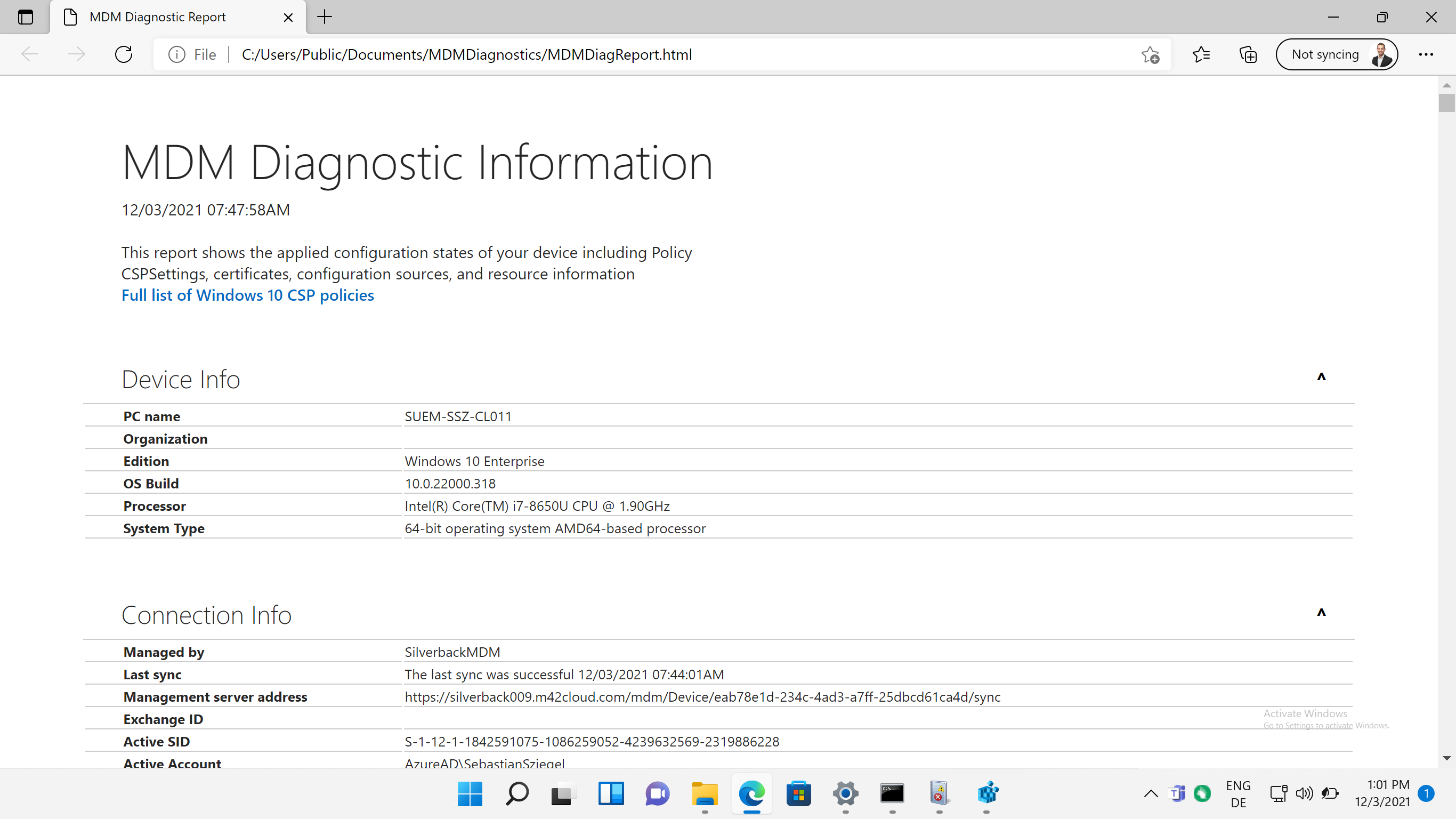
Use Command to collect logs
Another more extensive information logging can be executed into two different ways. On Windows 10 devices, you can run a command prompt to create a *.cab file that containts more information. On Windows 10 and 11 devices, you can run the following command and navigate afterwards to C:\Users\Public\Documents\MDMDiagnostics in File Explorer to review the report
mdmdiagnosticstool.exe -area DeviceEnrollment;DeviceProvisioning;Autopilot -cab c:\users\public\documents\MDMDiagReport.cab
Possible areas are listed in the Registry under HKLM\SOFTWARE\Microsoft\MdmDiagnostics\Area
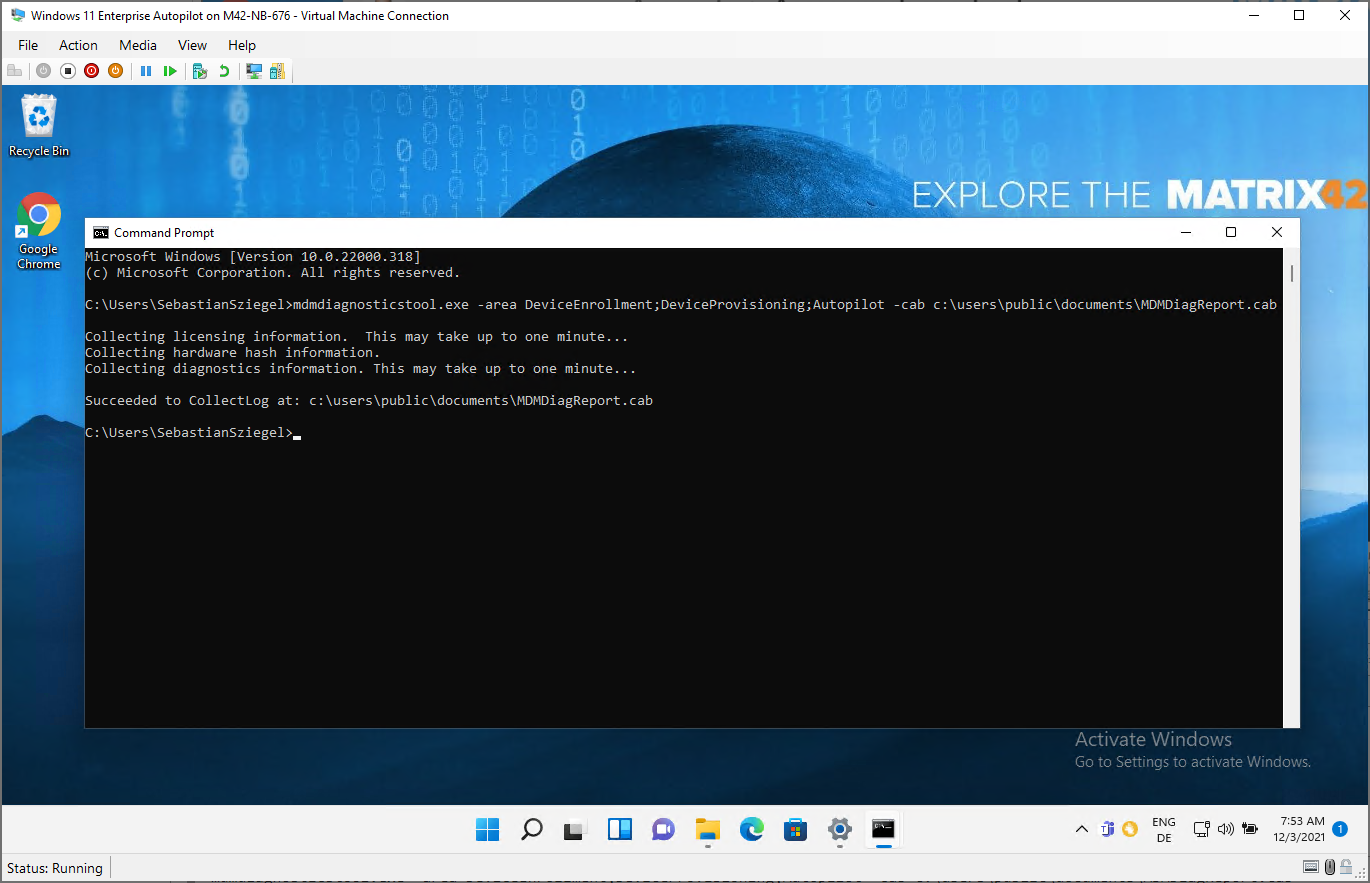
On Windows 11, you can also directly create the *.cab file. For that open Settings > Accounts > Access Work or School and press the Export button under Related settings. Navigate afterwards to C:\Users\Public\Documents\MDMDiagnostics in File Explorer to review the report
Understanding cab structure
- Please refer to the following article: Understanding cab structure (Microsoft)
- Review additionally the following article: Windows 10 MDM troubleshooting (Peter van der Woude, Microsoft MVP)
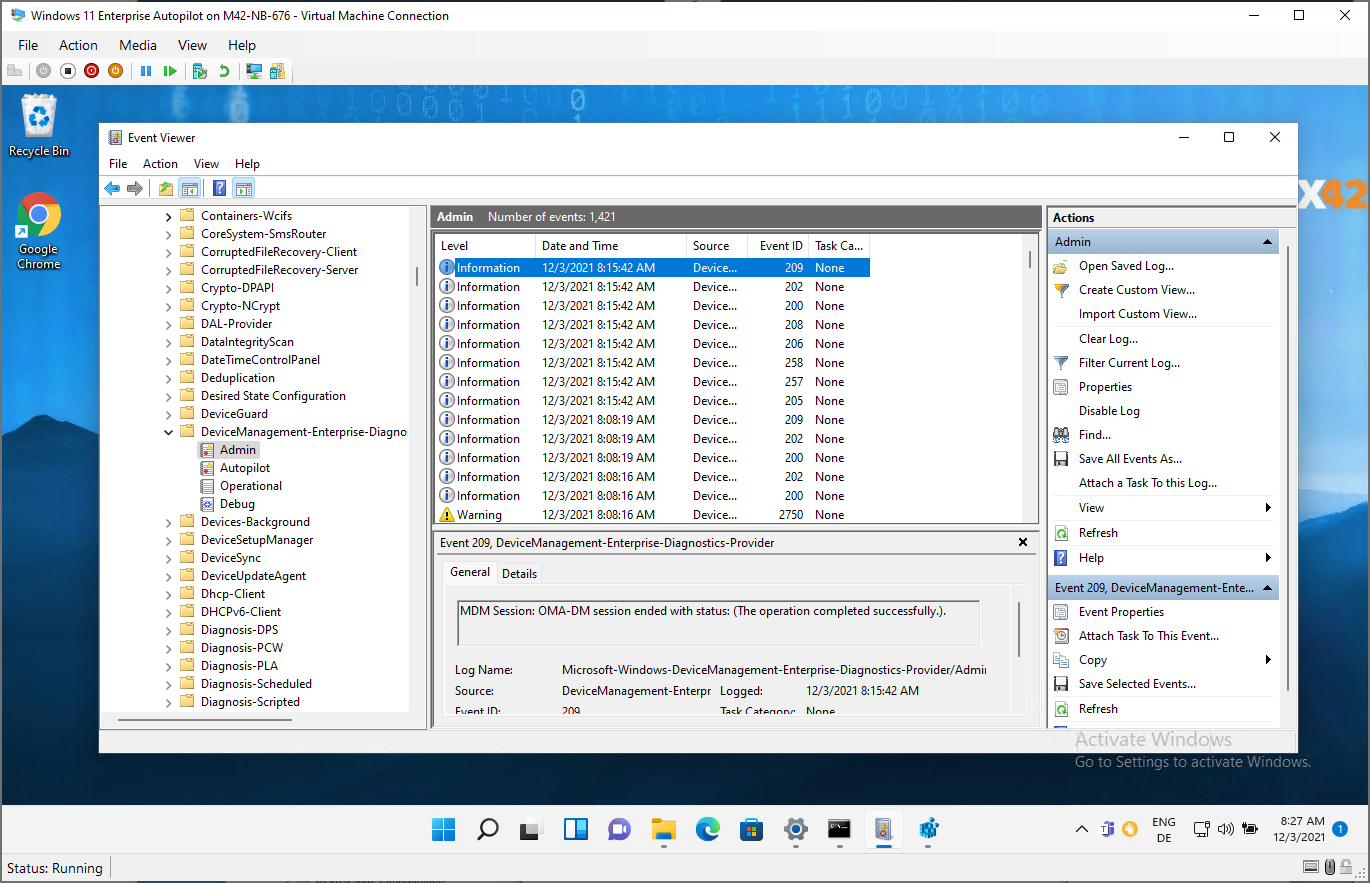
Review and Export Logs from Event Viewer
- Open Event Viewer
- Navigate to Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider
- Select Admin as this channel logs events by default
- Review and/or filter events by selecting Filter Current Log
- To export the logs, press Save All Events As, select a location and press save them
- To enable Debug Logs, select View and Enable Show Analytic and Debug Logs
- Select the Debug Node and press Enable Log and confirm with Yes
- To export the Debug Logs press again Save All Events As
Collect logs remotely
Remote Diagnostic Archive functionality which is used to trigger devices to gather troubleshooting data into a zip archive file and upload that archive to an Azure Blob storage. This option is designed for ad-hoc troubleshooting scenarios, such as an administrator investigating an app installation failure using a collection of event log events, registry values, and app or operating system log files. In this case, administrators can initiate the process remotely with Silverback.
Create a Storage Account
- Please refer to the official documentation: Create a storage account
- After successful creation of the storage account, proceed with Create a Container
Create a Container
- Open your storage account
- Select Containers
- Click + Container
- Enter as name e.g. mdmdiagnostics
- Select as Public Access Level private
- Press Create
- Wait until the until the container is successfully create
Generate Shared Access Token
- Select your newly created container
- Select Shared access tokens
- Enable the following permissions
- Read
- Write
- List
- Set Expiry to something into the future, e.g. to date in 24,36,48 month
- Press Generate SAS Token and URL
- Copy the Blob SAS URL to your Clipboard
Add Azure Blob to Silverback
- Open your Silverback Management Console
- Login as Administrator
- Navigate to Admin
- Select Azure Active Directory
- Switch to the Azure Blob Tab
- Click Enabled
- Paste your Blob SAS URL from your Clipboard
- Press Save
- Confirm with OK
- Click OK after the settings saved successfully information
Request Logs
- Navigate to Devices
- Locate your target device
- Open Device Information
- Select Actions
- Press Request Diagnostics
- Confirm with OK
Review Status
- Click again Actions and open Pending Commands
- Review the Command Status of the command type ExecuteDiagnosticArchiveRequest
- Most likely it will be Pending, which means the next time the device is communicating with the Server, the Logs will be generated
- If it is success, the device will start to generate and upload the logs to your Azure Blob.
Perform a device refresh to speed up the executing of the request
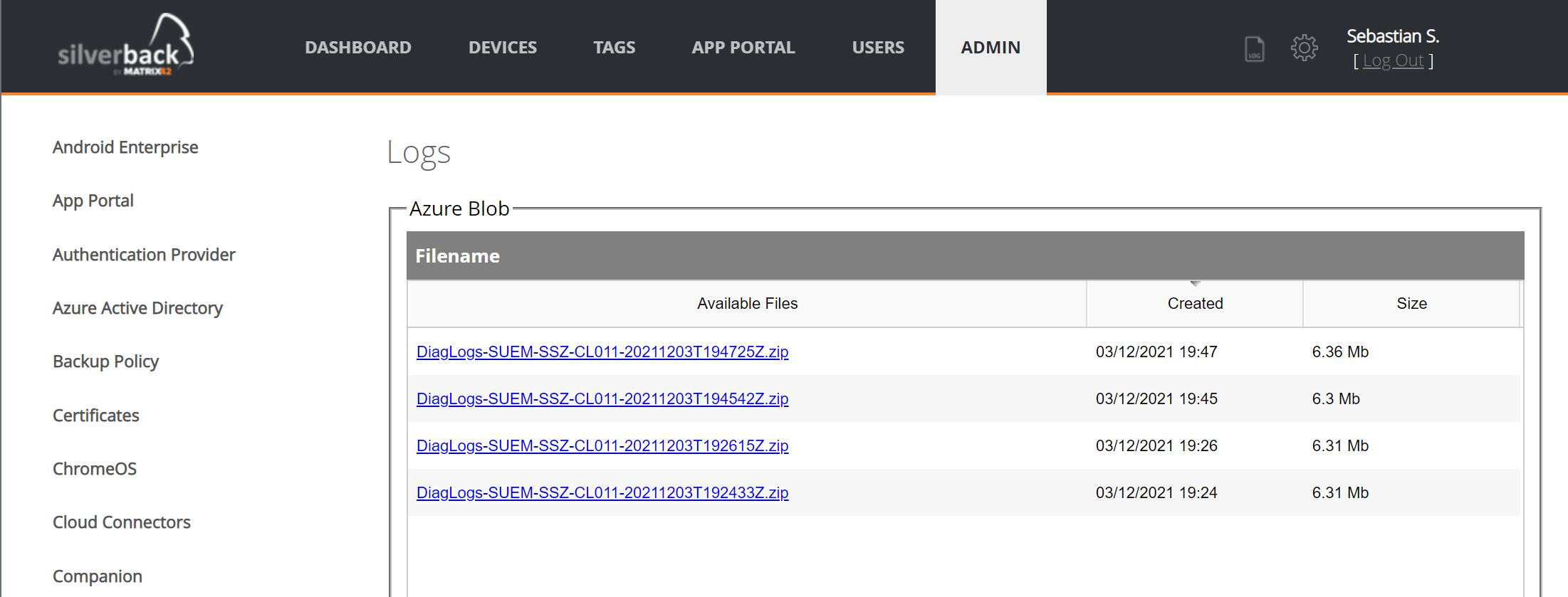
Download Logs
- Navigate to Admin
- Select Logs
- Locate the Vendor specific section
- Press View Logs next to Windows Diagnostics
- All generated Logs file will be listed here
- Select the archive that you want to download
Review Output
- Extract the *.zip archive
- Open in the root folder, the results.xml
- The running order reflects the folder structure of the downloaded archive
- Command HRESULT="-0" says that the command executed successfully
- Command HRESULT="-2147024895" says that the command has failed
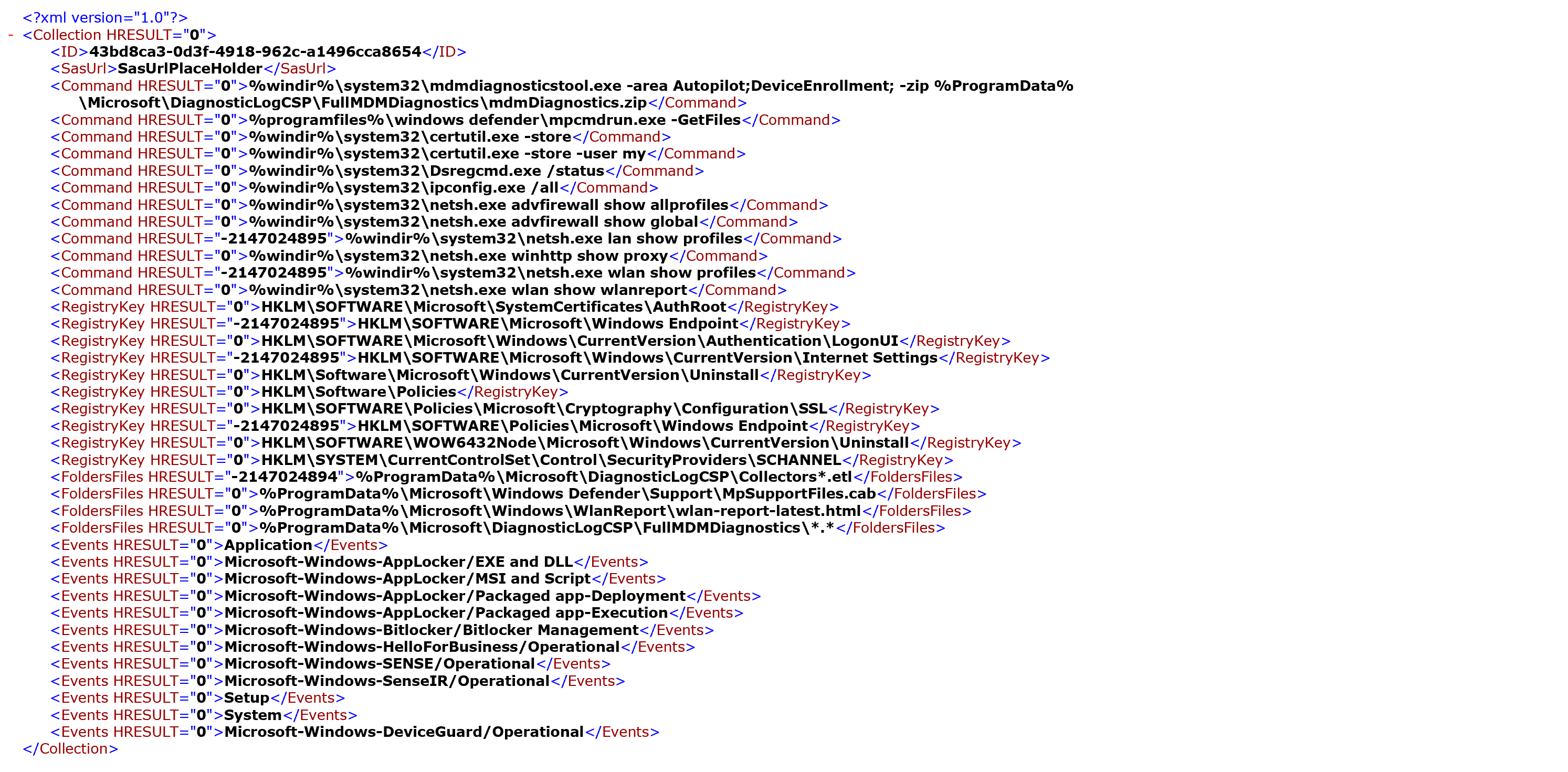
- Review the folder structure and review captured logs and output files.
| Content | Source |
|---|---|
|
%windir%\system32\mdmdiagnosticstool.exe -area Autopilot;DeviceEnrollment; -zip %ProgramData%\Microsoft\DiagnosticLogCSP\ FullMDMDiagnostics\mdmDiagnostics.zip %programfiles%\windows defender\mpcmdrun.exe -GetFiles %windir%\system32\certutil.exe -store %windir%\system32\certutil.exe -store -user my %windir%\system32\Dsregcmd.exe /status %windir%\system32\ipconfig.exe /all %windir%\system32\netsh.exe advfirewall show allprofiles %windir%\system32\netsh.exe advfirewall show global %windir%\system32\netsh.exe lan show profiles %windir%\system32\netsh.exe winhttp show proxy %windir%\system32\netsh.exe wlan show profiles %windir%\system32\netsh.exe wlan show wlanreport |
|
HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot HKLM\SOFTWARE\Microsoft\Windows Endpoint HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall HKLM\Software\Policies HKLM\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL HKLM\SOFTWARE\Policies\Microsoft\Windows Endpoint HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL |
|
%ProgramData%\Microsoft\DiagnosticLogCSP\Collectors*.etl %ProgramData%\Microsoft\Windows Defender\Support\MpSupportFiles.cab %ProgramData%\Microsoft\Windows\WlanReport\wlan-report-latest.html %ProgramData%\Microsoft\DiagnosticLogCSP\FullMDMDiagnostics\*.* |
|
Application Microsoft-Windows-AppLocker/EXE and DLL Microsoft-Windows-AppLocker/MSI and Script Microsoft-Windows-AppLocker/Packaged app-Deployment Microsoft-Windows-AppLocker/Packaged app-Execution Microsoft-Windows-Bitlocker/Bitlocker Management Microsoft-Windows-HelloForBusiness/Operational Microsoft-Windows-SENSE/Operational Microsoft-Windows-SenseIR/Operational Setup System Microsoft-Windows-DeviceGuard/Operational |