Intro to SDDM
FireScope Secure Discovery and Dependency Mapping (SDDM)
FireScope’s Secure Discovery & Dependency Mapping (SDDM) product uses an automated approach to asset discovery and dependency mapping across your enterprise providing increased visibility and control over your IT resources, including;
- Automates discovery and mapping of IT services and dependencies
- Improves and simplifies CMDB and Service Asset and Configuration Management (SACM) tools integration, natively and via the FireScope REST API’s.
- Identifies system changes in real-time using a persistent and passive network listening techniques
- Boosts CMDB accuracy
- Provides application dependency discovery, minus the effort
SDDM listens to and collects network traffic to understand relationships and dependencies between physical and virtual devices; enabling IT to support the business by:
- Building dependency maps of all digital devices, applications, IT and business services.
- Federating CMDBs via our REST API and keeping the baseline accurate for ITSM platforms, while accelerating deployment activities and return on investment.
- Promoting a RISK Management approach to Change Management identifying upstream and downstream dependencies of configuration items (CI’s).
- Leveraging SDDM persistent techniques to alert you to risks from unexpected and unauthorized changes in your environment.
FireScope’s SDDM is a powerful platform that is simple to deploy, easy to use, useful in a wide range of IT activities, provides quick time to value and improves visibility and day to day management of your IT infrastructure.

Figure 1 – An illustration of visibility provided through SDDM dependency mapping
FireScope SDDM Business Value
FireScope provides critical information to help you manage and maintain your applications and digital assets; improving visibility, availability and regulatory compliance. This includes the ability to group your digital assets into Business Services that can be baselined and monitored, showing all existing dependencies and noting any new activity or devices that would impact each of your Business Services.
- Audit/Regulatory: SOX, NY-DFS, and HIPAA all require up to date views of critical and unauthorized devices and their relationships.
- Service Portfolio: Analyze the ongoing value of IT to the business identifying mission-critical business relationships.
- Business Continuity Management: Data is key when planning business continuity and the IT to business service relationships are at the top of that list.
- Time to Value: SDDM is designed to be easy to install and configure, flexible and extensible. You can be up and running quickly and easily add additional CI’s and dependencies over time.
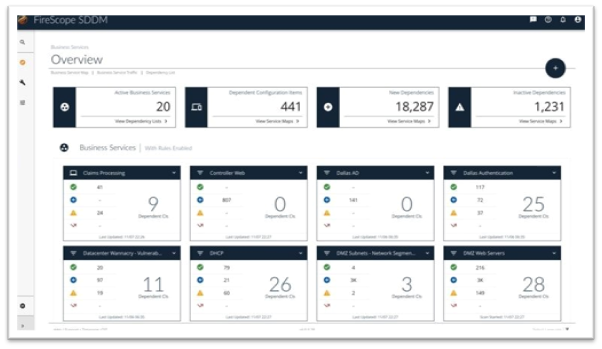
Figure 2 – SDDM allows you to group dependencies by business service and create baselines of these business services against which you can easily monitor changes in your environment.
FireScope SDDM for IT Value
- ITIL® Change Management: SDDM identifies the impacts of changes on dependent CIs, changes that are unauthorized and status needed for change transition
- ITIL® Configuration Management: Once discovered you now have your baseline and related CIs to integrate into your CMS/CMDB
- ITIL® Service Level Management: Using the SDDM maps you can now logically visualize IT dependences to decide SLOs/OLAs
- ITIL® Service Catalogue: Same data from the above can show you all the current state relationships needed to build a service portfolio
- ITIL® Availability Management: Data can be used to identify single points of failure on a business service.
- NIST: Supports Configuration Management controls.
- SecOPs: SDDM maps can be used by Security teams to validate firewall rules are working correctly, trouble-shooting suspicious activities, investigating rogue devices and application micro-segmentation projects.
- Application Support: Gain an end-to-end understanding of applications and business services – even those that are hybrid cloud or span multiple data centers.
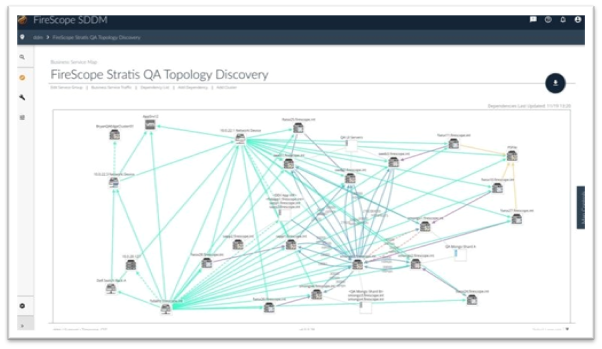
Figure 3 – An example of Topology Discovery using SDDM
Flexible, Scalable Architecture
- Built on a 3-tier architecture and employing new Clustered Edge technology to scale to support the largest and most complex environments.
- Flexible deployment options with hybrid SaaS hosted in Amazon Web Services (AWS) Cloud.
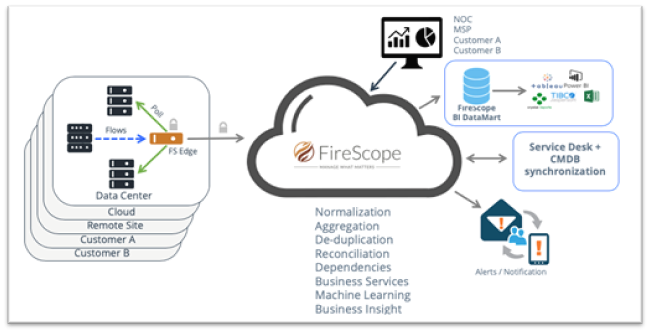
Figure 4 – A sample SDDM Installation
Considerations
Give some considerations such as system requirements or "gotchas" for this setting or control or programming syntax.