Connect Microsoft Azure Active Directory with MyWorkspace
Summary
MyWorkspace is able to connect different directories to each other. Imagine the user Maria Miller is using a corporate Google account to access all groupware applications, e.g. word processing, presentations or electronic mails. On the other side the company is using the Azure Management Console with a configured Azure Active Directory to prevent the usage of private Microsoft Accounts.
This document describes how to connect an existing Azure Active Directory with MyWorkspace to connect the different identity sources to each other to allow every user just using the primary corporate account, e.g. a corporate Google account to log into applications managed with Azure Active Directory. The benefit for the IT is that only one directory needs to be managed, MyWorkspace takes care for the rest of it.
Goal
After completing this tutorial you will be able to connect one or more Microsoft Azure Active Directories with Matrix42 MyWorkspace which allows every user in your organization to log into Azure Active Directory managed applications via your primary corporate account, e.g. Google Enterprise Apps or just a local Active Directory. As a prerequisite this tutorial expects that you are owning an Azure Active Directory which is connected to a custom domain, e.g. your company domain:
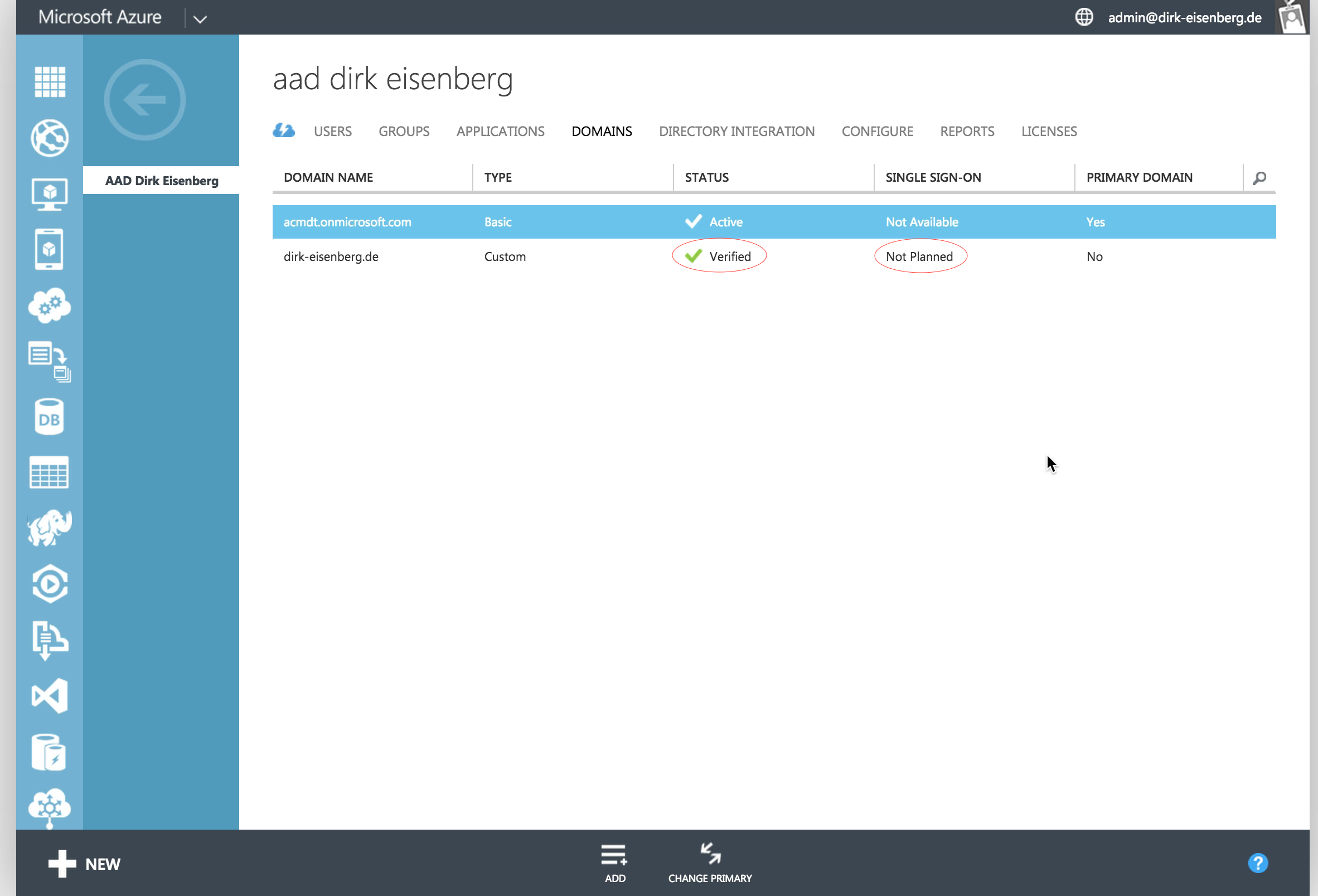
Please visit the Azure Management portal to verify this prerequisite and ensure that especially the domain is correctly verified and not marked as primary domain.
First Step: Ensure you have access to the Azure Active Directory as a Global Administrator
MyWorkspace requires that you have access with an administrative account to the Azure Active Directory. This needs to be verified in the first place by visiting the user manager in Microsoft Azure as described in the following video sequence:
Please remember the username and password of the selected administrative account because it's required in the next steps to perform the so called "Administratrive Consent Flow".
Second Step: Prepare MyWorkspace - Activate the Azure Active Directory Connector
MyWorkspace offers different connectors to integrate complex identity systems e.g. Azure Active Directory or Local Active Directory. For every Azure Active Directory which should be connected a single connector needs to be activated and configured.
Please visit the connectors section in the configuration area of MyWorkspace to add a new connector as shown in the video sequence bellow. During this process MyWorkspace starts an administrative consent flow which performs the following changes:
- The Azure Active Directory Administrator allows MyWorkspace to read & write users and groups with the identity of the account used during the consent flow. We recommend that you are creating a service account which is used by MyWorkspace only. This ensures that you can identify actions from MyWorkspace in your audit log correctly.
- MyWorkspace registers the MyWorkspace application in the Azure Active Directory which allows other users to interact with MyWorkspace indirectly during the login process as well.
After the successful consent flow the Azure Active Directory Connector is activated but nothing changed on the system at all. Federated security which allows users to login to the system via the MyWorkspace solution can and needs to be configured per domain level.
Third Step: Configure the AAD - Enable Federated Security
MyWorkspace displays the different domains of the connected Azure Active Directory as part of the connector details. If your domain is missing just visit the Azure Management Portal and add a new domain to the directory. As soon the domain is verified MyWorkspace will show this domain in the connectors settings immediately.
Enabling federated security means that after this step every Azure Active Directory user with an account matching to the selected domain, will be redirected to MyWorkspace and needs to pass the authorization before using the target application, e.g. the Azure Management Portal. This allows to connect any application supported by the Azure Active Directory with MyWorkspace.
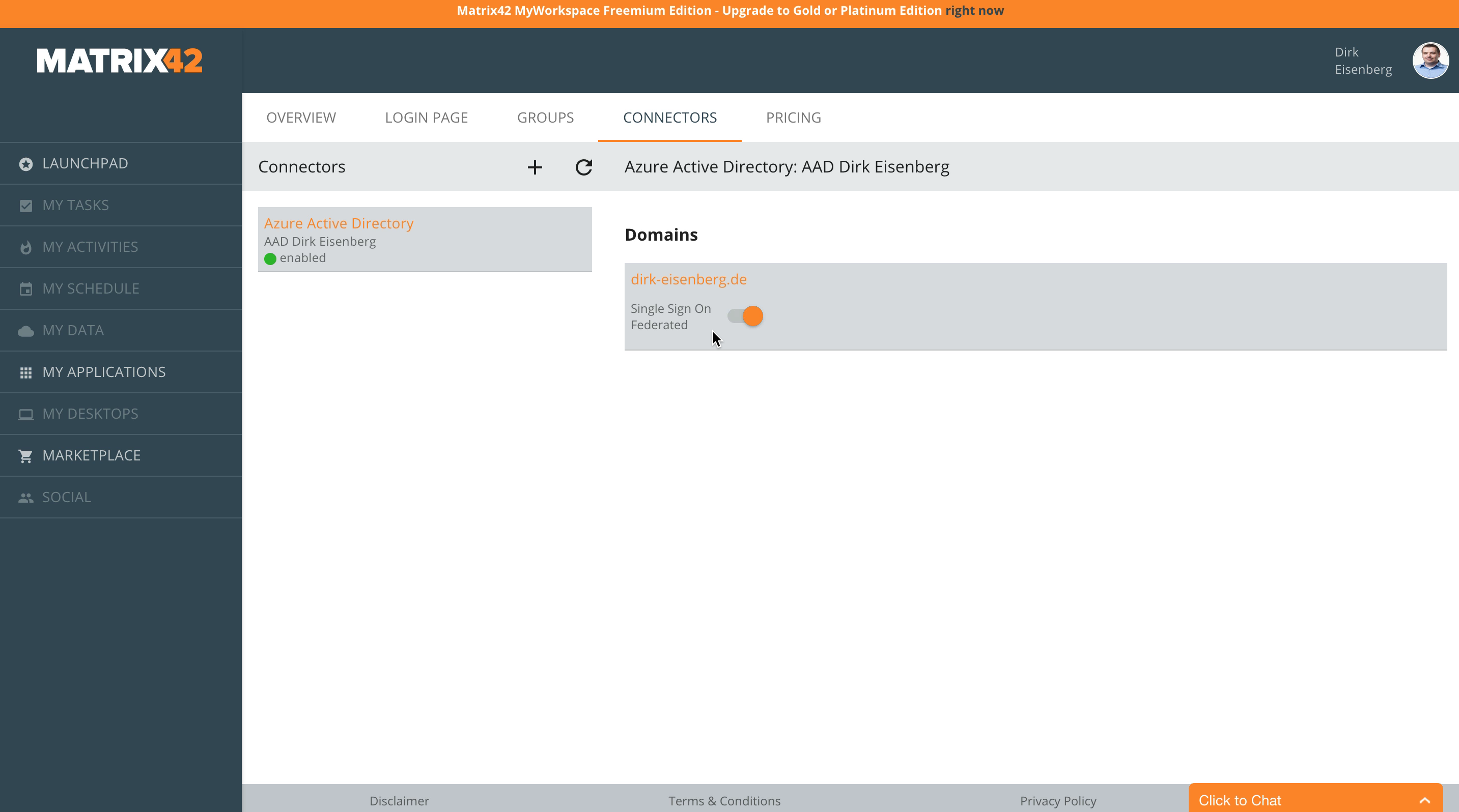
Moving the switch to enabled as showed above starts a short configuration process in the background and after that also the domain is marked as configured for single sign on in the Azure Management portal as well.
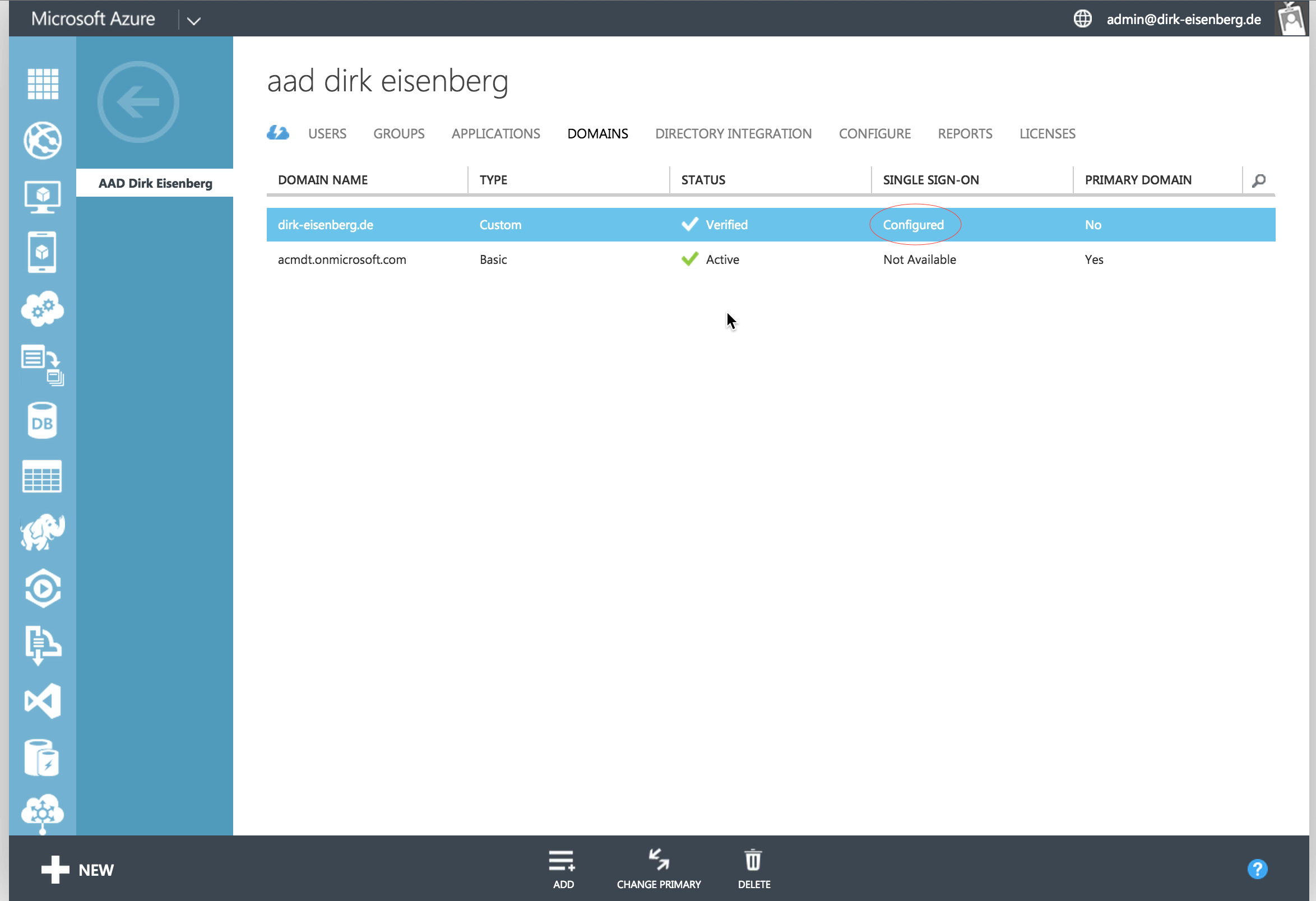
The following video demonstrates the now changed login behavior for Azure Active Directory users. Sometimes it takes up to 60 minutes until the change to federated security becomes active. Please check the "More Information" section for detailed information when this happens in your configuration.
More Information
Delayed Activation
When activating federated security it could take up to 60 minutes until the change becomes active in the Microsoft Azure infrastructure. This does not mean any service operation is interrupted. During this period of time it's possible for every user to pass authorization flows with the previously used username and password. As soon the infrastructure was able to apply the change the system switches automatically without any notice to the new MyWorkspace based authorization flow.
Dynamic Account creation
As soon a domain in Azure Active Directory is switched to federated security no accounts can be created for this domain in the Azure Management console. MyWorkspace takes care of this when the user passes the authorization flow. During this process the system also synchronizes all groups between MyWorkspace and Azure Active Directory so that application permissions can be set from the MyWorkspace management console via group memberships. Should you use an external IdP like Google Enterprise Apps or a Local Active Directory the groups from this external Idp are mapped into the Azure Active Directory automatically.
Restrictions for enabling Federated Security
Once single sign-on is enabled for a domain, all users from this domain can only login with MyWorkspace. This means all connected applications (e.g. Office 365 or Azure Management Portal) can only be used with your MyWorkspace account.
To ensure you can always manage your AAD, you can't enable single sign-on for the same domain you used to connect your AAD to MyWorkspace. If you want to enable single sign-on for this domain, please first change your management account to an account from another domain.