Release Notes Silverback 21.0 Update 3
About This Release
Matrix42 Silverback 21.0 Update 3 provides new and improved features that have been implemented. During the development of this version, we have been focusing on valued feedback from our customers and partners to provide an ideal feature selection.
Important Announcements
Azure Active Directory Graph
When you added your MDM and MAM Application into your Azure Active Directory for Windows Autopilot and Azure Active Directory Join, you granted the application in the past API Permissions based on the Azure Active Directory Graph API. As this Azure AD Graph API offers access to only Azure AD services and is deprecated by Microsoft and will be retired June 30, 2022, we performed already with this Silverback 21.0 Update 3 version, a migration to the Microsoft Graph API as it is more secure and resilient than Azure Active Directory Graph Graph. After updating to Silverback 21.0 Update 3, you need to replace the granted Directory.Read.All permission from Azure Active Directory Graph with the following permission from Microsoft Graph API:
- Device.ReadWrite.All
- User.Read.All
LDAP Administrative Filter
Within this release, we removed the dependency between the LDAP Filter and administrative logins. The LDAP Administrator Filter will not be available anymore and based on the provided Active Directory Groups under Admin > User Management > Active Directory, a LDAP Filter for each specific group (MemberOf=GroupName) will be generated in the background to allow role-based logins with LDAP credentials. This ensures that administrative user accounts can be anywhere in the AD, but please keep in mind to not exclude these accounts from the Distinguished Name, which is the starting location for LDAP lookups. If administrative users will be in two or more groups, roles will win from top to bottom as ordered in the Active Directory section under User Management. We recommend having at least one local administrative user in Silverback before performing the update to this new version.
Changes for Provisioning Users
When using the Provisioning Users option with LDAP users or credentials, ensure that the authorizing user is part at any group configured in the Active Directory Tab under User Management. To provision local users, use for the authorization any account that is listed as a System User under User Management.
Windows 10 Mobile
Microsoft announced already in 2016 that Windows 10 Mobile, version 1709 will be the last release of Windows 10 Mobile and Microsoft ended the support on December 10, 2019. This deprecation applied to Windows 10 Mobile products and users will no longer be eligible to receive new security updates, non-security hotfixes, free assisted support options or online technical content updates. As of today, we want to announce that all Windows 10 Mobile related content will be removed with the upcoming version Silverback 22.0 and we will already remove all technical content about Windows 10 Mobile from the technical documentation, soon.
Virtual Private Network Profile for Samsung
Android device management has changed a lot since the release of Android Enterprise and as Google and Samsung is continuously deprecating features and functionalities for the so-called legacy management or non-Android Enterprise Management. As of today, we mark the Virtual Private Network configuration on Samsung devices for Cisco AnyConnect as deprecated. Customers are encouraged to migrate to Android Enterprise and use the Cisco AnyConnect application, configured with managed configuration. For certificate based authentication with Cisco AnyConnect, distribute certificates with the Certificate Profile. With Silverback 22.0, the Virtual Private Network profile for Samsung devices will be removed.
Overview
New Features
Android Enterprise
Windows 10/11
iOS, iPadOS, macOS
- New Factory Wipe Options (Preserve Data Plan, Skip Proximity Setup, Require Network Tethering)
- New Network Information (eSIM and Dual SIM)
- New Device Information
- Deploy Tags to Apple Silicon devices
- New Device Actions for macOS devices (Restart, Shutdown, Remote Desktop)
- Prevent Erase All Content and Settings
- Enforce major, minor, and non-software update delays
- Allow nonadministrative users to approve Kernel Extensions option
Exchange Protection
New Improvements
New Changes
New Features
Android Enterprise
Please find all new Android Enterprise related features in Silverback 21.0 Update 3 below.
Advanced QR-Code Provisioning
Advanced QR-Code provisioning method allows to enroll corporate-owned devices into the Android Enterprise Device Owner Mode by scanning a QR-Code during the initial device setup. Administrators or users can tap the Welcome screen six times in the same spot to launch the QR code setup wizard. The QR-Code contains Wi-Fi credentials and allows either to automatic provisioning the device or let the user start at the Self-Service Portal. By selecting automatic provisioning, each value entered as usage count reserves the same number of licenses. Please refer to Advanced QR-Code Provisioning for additional information.
End-user credentials pass-through
With our new Companion version 21.0 Update 3, Administrators can use the End-user credential pass-through feature of Knox Mobile Enrollments for single or bulk enrollments for devices. A Knox Mobile Enrollment admin can associate both a username and password/secret with device(s) in the KME portal and our Matrix42 Companion is able to retrieve and handle the provided username and password from the cloud service to proceed with the enrollment, so your users won't get prompted for adding username and password manually during the enrollment. Please refer to Android Enterprise VI: Knox Mobile Enrollment and Bulk Enrollments with Samsung Knox Mobile Enrollment for additional information.
Windows 10/11
Please find all new Windows 10 and Windows 11 related features in Silverback 21.0 Update 3 below.
Device & Network Information Update
For Windows 10 and Windows 11 devices, we improved and extended the device and network information for your managed devices and now you can retrieve all information about network interfaces and cellular identities. Additionally, we removed non-applicable device information.
Device Information
- Added Version 21H2 for all build versions 19044 and newer
- Last PIN Reset Values, Radio Software Version, WiFi MAC, Screen Resolution and Processor Type has been removed
- Merged and renamed Hardware Version and Software Version to BIOS Version.
BIOS Version returns the registry key under HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\BIOS\BIOSVersion
- International Mobile Station Equipment Identity (IMEI) value is now shown properly
- Processor Architecture type displays now the friendly name of the architecture instead of digits
- Added RAM information in MB, which specifies the total available memory in MB on the device (may be less than total physical memory)
Network Information
- Network and device properties has been added with the following information:
- MAC address of the wireless network card. A MAC address is present for each network card on the device.
- IPv4 address of the network card associated with the MAC address.
- IPv6 address of the network card associated with the MAC address.
- Connected value that indicates whether the network card associated with the MAC address has an active network connection.
- Type of Network connection (WLAN, LAN or unknown)
- Node for queries on the SIM cards has been added with the following information:
- Subscriber Country build from the first three digits from International Mobile Subscriber Identity (IMSI)
- The International Mobile Subscriber Identity (IMSI) associated with the IMEI number.
- The Integrated Circuit Card ID (ICCID) of the SIM card associated with the specific IMEI number.
- Phone number associated with the specific IMEI number
- Current Network as the mobile service provider or mobile operator associated with the specific IMEI number.
- Roaming Status indicates whether the SIM card associated with the specific IMEI number is roaming.
Remote Desktop Configuration
With Silverback 21.0 Update 3, you have now the capability to configure Remote Desktop devices for Windows 10 and Windows 11 devices. These options include first to allow or prevent remote access to computer by using Remote Desktop Services and prevent or allow mapping of clients drives in a Remote Desktop Services session. With passwords options, you can define if the option to save credentials will be applied for Remote Desktop connections and if password prompts will be forced upon connections. As additional security options you can specify whether a Remote Desktop Session Host server requires a secure RPC communication with all clients or if it allows unsecured communication. If you are using native RDP encryption as secure communication between client computers and RD Session Hosts, you can specify encryption levels for these connections. Please refer to Tags Guide Part IV: Windows 10/11 and Windows 10/11 Working with Firewall Rules and Remote Desktop for additional information.
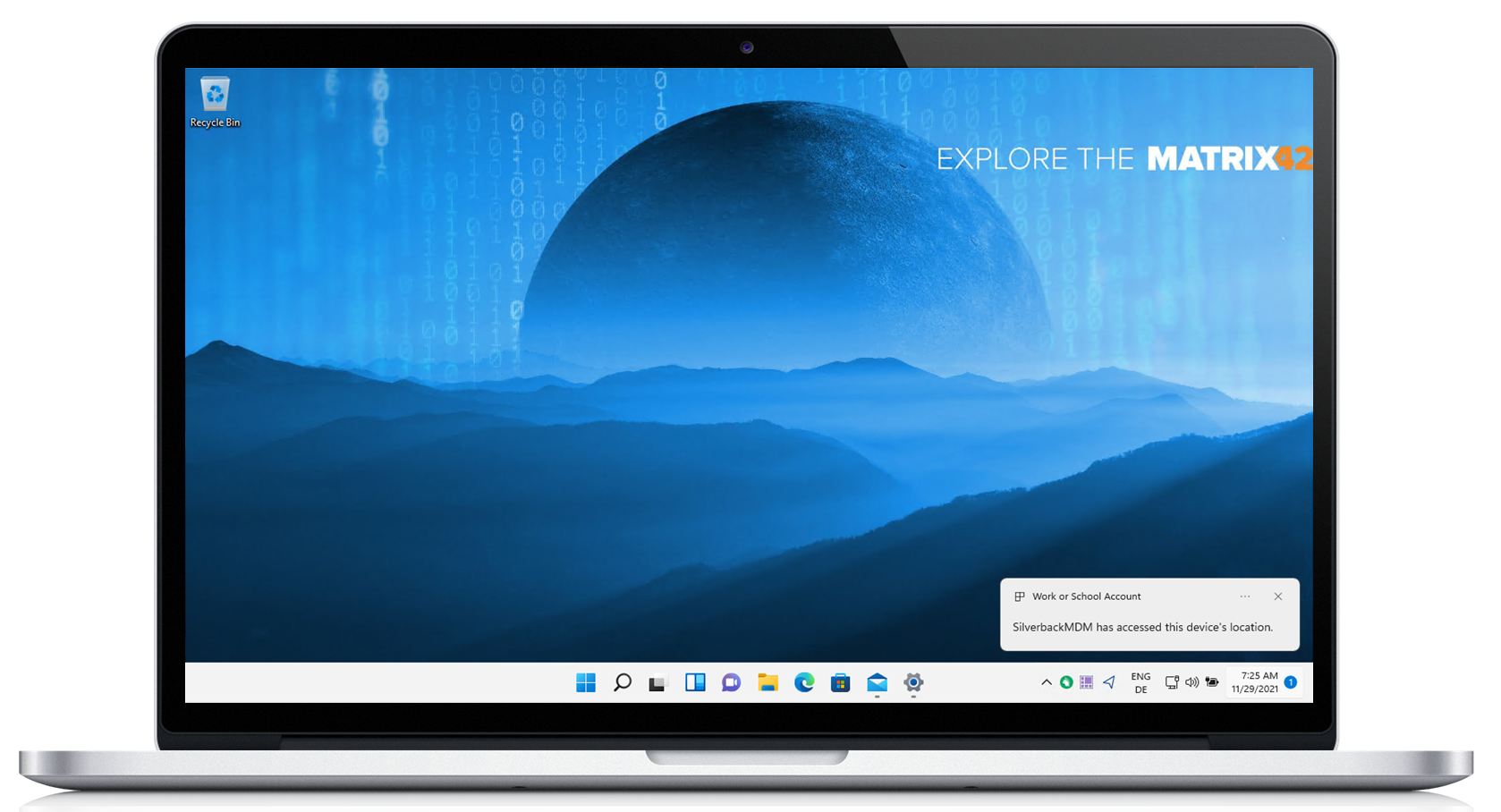
Device Location
Another new action in Silverback 21.0 Update 3 for corporate-owned Windows 10 and 11 devices is the Location action. By executing the remote find action, Silverback will request the device location and reports the current location in the device information of the devices in the location section. The captured and displayed information are the last known location, which will provide you a hyperlink to review the location on Google Maps. Besides that, the last captured at information is shown with the specific accuracy of the location. Please note that users get informed about the location tracking as shown in the screenshot below. If Administrators are executing this action, an Audit entry will be created in the Logs section. Additionally, you can now remotely configure if the Location Services on managed devices should be turned on or off, without letting users to overwrite this setting. This new Allow Location Service option is present in the Restrictions profile in the System category. When you remotely request the Location for one of your managed devices and either the Allow Location Service is forced off by the restriction profile or by the user itself, Silverback will turn for this specific action the location services on, request the location and turn the location off afterwards. This will ensure at any time when the device is reachable to gain the device location.
Location can only be retrieved for corporate-owned devices. For devices marked with a personal ownership, the Action is deactivated.
Request Diagnostics
Request Diagnostics is a new action that helps to remotely collect and download Windows devices logs without interrupting the user. The request diagnostics action is used to trigger devices to gather troubleshooting data into a zip archive and uploads that archive to an Azure Blob storage. With Silverback 21.0 Update 3, now you can add your Azure Blob shared access signature in the Azure Active Directory section under the Admin Tab. By enabling the Azure Blob, the Request Diagnostic action gets active and by executing, a diagnostic archive will be triggered and uploaded to your Azure Blob. To download generated archives, navigate to the Logs section in the Admin Tab and press View Logs in the Vendor specific Logs section for Windows Diagnostics. Please refer to Windows 10/11 Diagnostics and Logs for additional information.
By generating the archive, no personal information is collected.
iOS, iPadOS, macOS
Please find all new iOS, iPadOS, and macOS related features in Silverback 21.0 Update 3 below.
New Factory Wipe Options
With Silverback 21.0 Update 3, the following new Factory Wipe options are present and can be executed within the Management Console.
Preserve Data Plan
For the Factory Wipe device action, Administrators can now configure additional options. The Preserve Data Plan option is enabled by default and will preserve the data plan on an iPhone or iPad with eSIM functionality if one exists. This option is available for devices running on iOS 11 and later.
Skip Proximity Setup
In addition to the Preserve Data Plan option, we added the option Skip Proximity Setup, which is available for iOS and iPadOS devices running on iOS and iPadOS 14 and later. This option will disable the Proximity Setup (Quick Start) pane in the Setup Assistant after the factory wipe.
Require Network Tethering
Another option for the Factory Wipe execution is the Device must be network-tethered option. If devices are not network-tethered, the devices will ignore this command. Administrators can review if devices are currently Network Tethered within the device information, as this information is now present next to the following additional new device information.
New Factory Wipe Options are not support via API, Enterprise Service Bus or Data Providers.
New Network Information (eSIM and Dual SIM)
We extended the Device Overview for iOS and iPadOS devices with additional (e)SIM card information and now you can retrieve all information about all sim cards or data plans. These information are present of the Service Subscription device response from managed iOS and iPadOS devices and are available with iOS 12 and later. IMEIs, EID and MEID Identifiers are displayed under Network Information and SIM Card / Data Plan specific information are displayed as separated SIM Card / Data Plan for each available slot. In case older devices are still under management, the information is not present, and the network information is shown as prior to this Silverback version. Please take into account that iPads with two SIM cards (physical + esim) might only report the active used card to the management system and additionally, it might be that phone numbers for esim cards will not be reported. This might change for future iOS and iPadOS versions or newer devices.
eSIM and Dual SIM Information are not supported via API, Enterprise Service Bus or Data Providers.
Identifiers
- IMEI - International Mobile Equipment Identity
- EID - Embedded Identity Document
- MEID - Mobile Equipment Identifier
- ICCID - Integrated Circuit Card Identification Number
Voice and Data
- Roaming
- Data Preferred
- Voice Preferred
Additional Information
- Label
- Phone Number
- Slot
New Device Information
We added several new dictionaries to display more device information for iOS, iPadOS, macOS and tvOS devices. This information will be queried from every device and if devices does not return the information to the management server, the information will not be shown at all in the Device Information of the corresponding device. Please take this into account, if you might miss some of these information for a specific device within the device overview.
| Information | iOS /iPadOS | macOS | tvOS | Description |
|---|---|---|---|---|
| Time Zone | Yes | No | Yes | The key to get the current Internet Assigned Numbers Authority (IANA) time zone database name. This value is available in iOS 14 and later, and tvOS 14 and later. |
| Locator Service Enabled | Yes | No | No | Determines if a device locator service, such as Find My, is in an enabled state on the device. This value is available in iOS 7 and later. |
| Activation Lock Supported | No | Yes | No | Determines if the device supports Activation Lock. This value is available in macOS 10.9 and later. |
| Activation Lock Enabled | Yes | Yes | No | The key to determine if Activation Lock is in an enabled state on the device. This value is available in iOS 7 and later, and macOS 10.9 and later. |
| Diagnostic Submission Enabled | Yes | No | No | Determine if the diagnostic submission setting is in an enabled state on the device. This value is available in iOS 9.3 and later. |
| App Analytics Enabled | Yes | Yes | No | Determines if the device is sharing app analytics. This value is available in iOS 4 and later, and macOS 10.7 and later. |
| iCloud Backup Enabled | Yes | No | No | Determines if iCloud Backup is in an enabled state on the device. This value is available in iOS 7.1 and later. |
| Last iCloud Backup Date | Yes | No | No | Gets the date of the most recent iCloud backup. This value is available in iOS 8 and later. Most probably only iCloud backups after enrolling the device might be shown |
| Network Tethered | Yes | No | No | Determine if the device is network-tethered. This value is available in iOS 10.3 and later. |
| PIN Required For Device Lock | No | Yes | No | The key to determine if the Device Lock Command requires a PIN. This value is available in macOS 11 and later. |
| PIN Required For Erase Device | No | Yes | No | The key to determine if the Factory Wipe command requires a PIN. This value is available in macOS 11 and later. |
| System Integrity Protection Enabled | No | Yes | No | Determines if System Integrity Protection is in an enabled state on the device. This value is available in macOS 10.12 and later. |
Deploy Tags to Apple Silicon devices
To create more flexibility and granularity and to be ready for the future, you can now split Tag assignments between Apple Silicon and Non-Apple Silicon devices. As an example, it will ensure to distribute applications to your macOS devices, that have different binaries for Apple Silicon and Non-Apple Silicon devices. By enabling the Auto Population, select the Device Variable Key Apple Silicon and select as value either Yes or No. By selecting Yes, all Apple Silicon devices will automatically be assigned to this Tag.
New Device Actions for macOS
With Silverback 21.0 Update 3, the following four new Device Actions are present for macOS devices and can be executed within the Management Console.
Shutdown & Restart
Administrator can send a reboot or shut down command to any device under management. This can be particularly useful for maintenance activities.
Enable & Disable Remote Desktop
Administrators can remotely enable or disable the Remote Management on macOS devices with the All Users access, the ability to receive remote events and the Observe, Control, and Show being Observed options.
New Device actions are not support via API, Enterprise Service Bus or Data Providers.
Prevent Erase All Content and Settings
With the release of macOS Monterey this year, Apple made it easier to restore macOS. In the System Preferences application, there is a new erase all contents and settings option, which is like the restore mechanism on iOS and iPadOS devices that makes it easier to return any macOS device to factory settings. To prevent users from executing this new erase all contents and settings options, you can disable the Allow Erase Content and Settings option in the Restriction Profile. By default, this option is allowed to users and the restriction is in the System Settings group.
Enforce major, minor, and non-software update delays
Beginning with macOS BigSur 11.3., Apple extended and separated the OS updates control in context of postponing operating systems up to 90 days. In previous macOS versions, the Defer Operating System Updates and Defer Non-Operating System Updates options were able to be defined for a value up to 90 days. With Silverback 21.0 Update 3 and for devices starting from macOS BigSur 11.3, we extended and added additional options that are targeting these OS versions. As a benefit, you have now different controls for major, minor and Non-Operating System Updates and you can enforce the deferral period for each option separately. Please refer to Tags Guide Part V: macOS for additional information. For migrations scenarios to the new options we recommend to create a new Tag with set Auto Population variable key to greater than OS Version >11.2.3, to let these options apply to applicable devices only. If two Tags will be applied to devices, the newer Tag will win as this is in addition useful if you want to decrease the deferral period for specific devices.
Allow nonadministrative users to approve Kernel Extensions option
With the Kernel Extensions you can configure or allow third-party kernel extensions that are defined inside the profile. We granted the options to configure Kernel Extensions in Silverback 20.0 Update 1 and with this release, we extend the options with the Allow nonadministrative users to approve Kernel Extensions option. If enabled, nonadministrative users can approve additional kernel extensions in the Security & Privacy preferences. This option is supported on macOS 11 and later and the default value is set to disabled.
Exchange Protection
In general, the Exchange Protection allows you to control who can access Exchange ActiveSync from Smartphones and Tablets. Silverback acts as the management platform providing control over Exchange ActiveSync access based on its policies. Silverback will either allow managed devices, or deny unmanaged devices, ensuring a base level of compliance. As the PowerShell Integration establishes a remote connection to Exchange and Exchange Online is deprecating Basic Authentication for multiple protocols prior to its removal in the second half of 2021, the Basic Authentication will be superseded by Modern Authentication.
Modern Authentication Method to Exchange Protection
With this release we added the option to use the Modern Authentication for the Exchange protection. In general, you will need to Register a new application in Azure AD and assign the Exchange Online API Permissions and Azure AD Roles to the application. After that you will need to generate a self signed certificate and attach the public key to the Azure AD application and attach the certificate (private Key) to your Silverback Server. To ensure that Silverback can connect to Exchange Online, you will need to install the PowerShell EXO V2 module to finalize the integration. Please refer to Exchange Protection Integration I: Exchange Online with Modern Authentication for additional information.
New Improvements
Please find all new Improvements in Silverback 21.0 Update 3 below.
Management Console
- Added a View OTP option for Pending Enrollments and QR-codes are now downloadable
- Device ID, Device Name, Username and Operating System are now shown in Confirmation pop-ups for several actions
- Pending Commands in Device Overview shows now which Profile will be installed with the InstallProfile command
- Improved several screens, translations and behaviours in the Management Console including improving several validations
- Added several Quick Links under Admin > Logs and added a grouping for available Log options
- Fixed the duplicated time information under Bulk Provision Users
- Added over 500 new device models
- Fixed missing Titles for Dashboard Exports
Enterprise Service Bus
- Added heartbeat answers to provide health status to the Unified User Experience
- Added customizable Instance Display Name which is by default the Silverback URL build from the STS URL
Android Enterprise
- Added field paths for Knox Service Plugin Application Feedback
- Aligned naming for Samsung Knox and Android restriction Allow Remove Work Profile
iOS, iPadOS, macOS
- Increased cryptography for client certificates to SHA-256 with RSA algorithm and key length 2048 bits
- Volume Purchase Program Logs will now be cleared after selected Retention Period under Logs
- Added a queue check for Install Enterprise Application commands when tag settings changed
- Adjusted visibility for Shared Devices & Classroom restrictions from iPhone and iPod Tags due to non-support
- Renamed Authentication for Device Enrollment Program from Active Directory Authentication to Authentication
- Added drop down list for Device Enrollment Program Authentication with Username + Password or Username + OTP option.
Windows 10/11
- Switched from Azure Active Directory Graph API to Microsoft Graph API for Azure AD and Autopilot devices
- Fixed an issue with the SSL Client Cert Search Criteria value in registry for Azure AD and Autopilot devices
- Fixed an issue with Managed Application List for Azure Active Directory Joined devices (including Autopilot)
- Allow MSI Always Install With Elevated Privileges restriction will now be installed in user and device scope
- Fixed an UI issue for scheduled Antivirus scan as 11 am was shown as 1 am.
- Fixed an UI alignment in Device Information for Current state of the product (German)
- Fixed an validation issue with Specify Search URL for Microsoft Edge
- Adjusted several naming and tool tips for Defender Firewall Rules
- Fixed an issue with adding and removing Defender Firewall Rules
- Removed Storage value from Managed Devices Overview
Knowledge Base
Several new Knowledge Base articles has been added:
- Windows 10/11 Bulk Enrollments with Empirum and Provisioning Packages
- Bulk Enrollments with Samsung Knox Mobile Enrollment
- Windows 10/11 Create custom profiles
- Advanced QR-Code Provisioning
- Windows 10/11 Diagnostics and Logs
- Uninstall UEM Agent on macOS devices
- Device Enrollment Program: Token Alerts
- Windows 10/11 Working with Firewall Rules and Remote Desktop
Changes
- Knox Service Plugin is now handled and can be configured as a Profile
- Samsung Safe has been completely renamed to Samsung Knox
- Changed *.apk and *.ipa extractor to DotNetZip due to some upload failures
- Removed ASP.NET Core Runtime from Installer as it will be a new System Requirement for future installations
- Removed .Net Framework binaries for Silverback and Cloud Connector executables as they are a general system requirement
- Removed LDAP Administrator Filter as the authentication is planned to be transferred to Group Memberships only
- Increased security baseline for CheckOut request for Apple and Android devices
Known Issues
- When selecting clear passcode for Samsung Knox devices, the information "Without entering a new passcode, the current one will be cleared. Depending on the targeted device and operating system the end user experience may differ. Your device may ask to enter the current active passcode before any changes can be performed" is not shown.
- After adding an Enterprise application (*.ipa) to the App Portal, the App Management option Allow Uninstallation will disappear and is not changeable. The application might be shown in the App Portal on devices as Non removable, even if the application can be uninstalled by users.