Release Notes Silverback 20.0 Update 3
About This Release
Matrix42 Silverback 20.0 Update 3 provides new and improved features that have been implemented. During the development of this version, we have been focusing on valued feedback from our customers and partners in order to provide an ideal feature selection.
Please find the installation files of this version on Matrix42 Marketplace.
Global availability is ensured after the Matrix42 Release Day
System requirements, integration guides and instructions for installation and update are available in the Matrix42 Help Center
Important Announcements
Apple Push Notification Service Update
If you are managing Apple devices within your Organization, please read this section carefully!
Apple released in 2009 the push notification service and API which is used in any Mobile Device Management to communicate to managed devices. The API was fairly complex, leveraging a binary protocol, designed for speed of delivery but not necessarily ease of use. Apple has announced that this binary API is being discontinued on 31st of March and will be replaced by a new HTTP/2-based APNs provider API, which offers developers to take advantage of new features.
The change in the Apple Push Notification Service requires a new in-place backend technology for continuing Apple device management in your organization. This change in the Apple Push Notification Services requires a mandatory update to Silverback 20.0 Update 3 until the deadline of 31st of March.
With Silverback 20.0 Update 3 we ensure a seamless migration with no additional actions for all customers that are already hosting Silverback on a Microsoft Server 2016 or Microsoft Server 2019. The changes to the new HTTP/2-based APNs require present functionalities that are supported only in Microsoft Server 2016 and newer. This means all customers that are currently hosting Silverback on a Microsoft Server 2012 are required to migrate to a Microsoft Server 2016 until the 31st of March to continue with the Apple Device Management.
Please refer to our Server to Server Migration in case you are running Silverback currently on a Microsoft Server 2012.
HTTP/2-based APNs communication is utilizing Port 443/tcp to api.push.apple.com
Knox Validated Program Membership
The Knox Validated Program is an authentication program for Samsung partners with Unified Endpoint Management, Enterprise Mobility Management, and Mobile Device Management solutions integrated with the Samsung Knox platform and solution. We have been tightly cooperating with our partners from Samsung for the past several months and we are happy to announce that we now are on the last update of the Supported EMM Partner page, listed with all possible Knox Solutions (Validated by Samsung Knox, Knox Service Plugin and Knox Mobile Enrollment). From now on, customers deploying the Knox Validated solutions can have the fully visible confidence that our solution has been evaluated by the solution experts at Samsung and has met the requirements in order to receive the stamp of validation.

Decreasing support for Android device administrator
Google is encouraging movement off of device administrator management (Legacy Management) by decreasing its management support in new Android releases. With the upcoming Release of Companion 20.0 Update 3 and the increased target API level 29 for Android 10 devices, the following settings are deprecated:
Affected Devices
- Platform: Android (non Samsung Safe)
- Operating Systems: Android 10 and later
- Device Management: Legacy Management (non Android Enterprise)
Affected Deprecations
- Device Information - MAC Address, Serial Number and IMEI will no longer be reported. (Android + Samsung Safe including Work Profile)
- Passcode policies - Quality, length or expiry
- Restrictions - Allow Camera
- Wi-Fi- Profiles - Installing or updating Wi-Fi Profiles might lead to some undesired outcomes, like losing the Wi-Fi connectivity and settings on managed devices.
Overview
Management Console Improvements
Feature Pack for iOS & iPadOS 14
Feature Pack for macOS Big Sur
Endpoint Protection Features for Windows 10
- Configure devices with new restrictions
- Block end user access to various areas of Microsoft Defender Security Center App
- Provide IT contact information for Microsoft Defender Security Center App and/or Security notifications
- Configure protection phishing or malware websites and applications with Microsoft Defender Smart Screen
Power Management Options for Windows 10
Enhancements for Android Management
New Features
Management Console
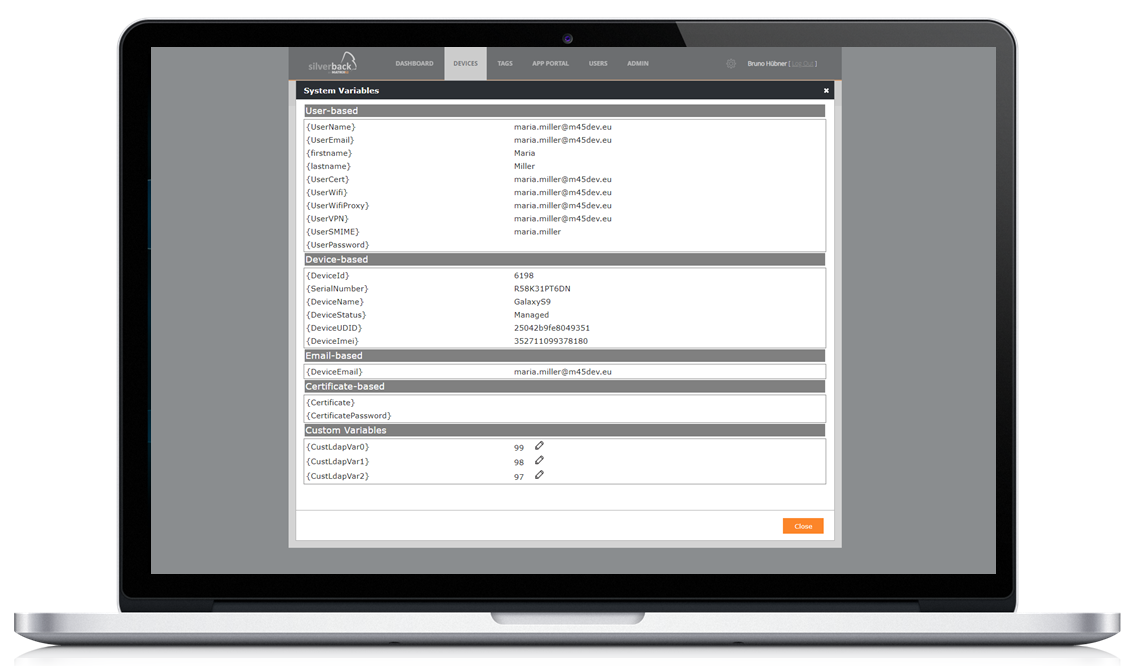
Please find the new capability to review and adjust captured System Variables within the Silverback Management Console below:
Display capture System Variables
With Silverback 20.0 Update 3 we added a new button named System Variables under the Action section in the device information overview. System Variables ensures a proper user based configuration of Profiles and Applications and are typically captured at the enrollment process. To make it more efficient for Administrators we are happy to share a new view of all captured system variables for a specific device.
For testing purposes of new or adjusted profiles or variables we added the ability to directly create or update existing Custom Variables.
Feature Pack for iOS & iPadOS 14
Apple released the new operating systems iOS 14 and iPadOS 14 in the mid of September. With the new Silverback 20.0 Update 3 release we address new features offered by these operating systems. Please find all new features below:
New Restrictions
With restrictions, Administrators can decrease the access or the usage of device features and functionalities. This helps to increase the security level on managed devices and prevent users from the usage of unwanted functionalities or settings. With iOS and iPadOS 14 Apple enhances the management capabilities for Administrators with two new restrictions.
| Setting | Availability | Options | Requirements | Description |
|---|---|---|---|---|
|
Allow App Clips |
|
|
|
Allows/Prevents users to download a smaller version of an app to do a specific task. Please refer to App Clips |
| Allow Apple Personalized Advertising |
|
|
|
Turning off personalized adds will limits Apple’s ability to deliver relevant ads to you but will not reduce the number of ads the user receives |
New Skip Setup Items for Device Enrollment Program
Apple developed the Device Enrollment Program to help businesses and educational institutions easily deploy iOS, iPadOS and macOS devices. Even when utilizing a mobile device management, the workflow to configure newly purchased iOS and macOS devices includes a bunch of steps manually taken from the user. The Device Enrollment Program supports to reduction in the number of required steps for a newly purchased device to be ready for use.
For devices added to the Device Enrollment Program administrators can configure which screens from the out-of-the-Box experience (OOBE) will appear to the user. In the best scenario the user will only see the initial mandatory screen(s) and the authentication for Silverback. iOS14, iPadOS14 and macOS 11 will bring a couple of new screens to users. To ensure to make the deployment of devices as fast as possible, we added the configuration of these screens into the Device Enrollment Program section.
| Setting | Availability | Options | Requirements |
|---|---|---|---|
| Restore Completed |
|
|
|
| Software Update Completed |
|
|
|
| Accessibility (OS X) |
|
|
|
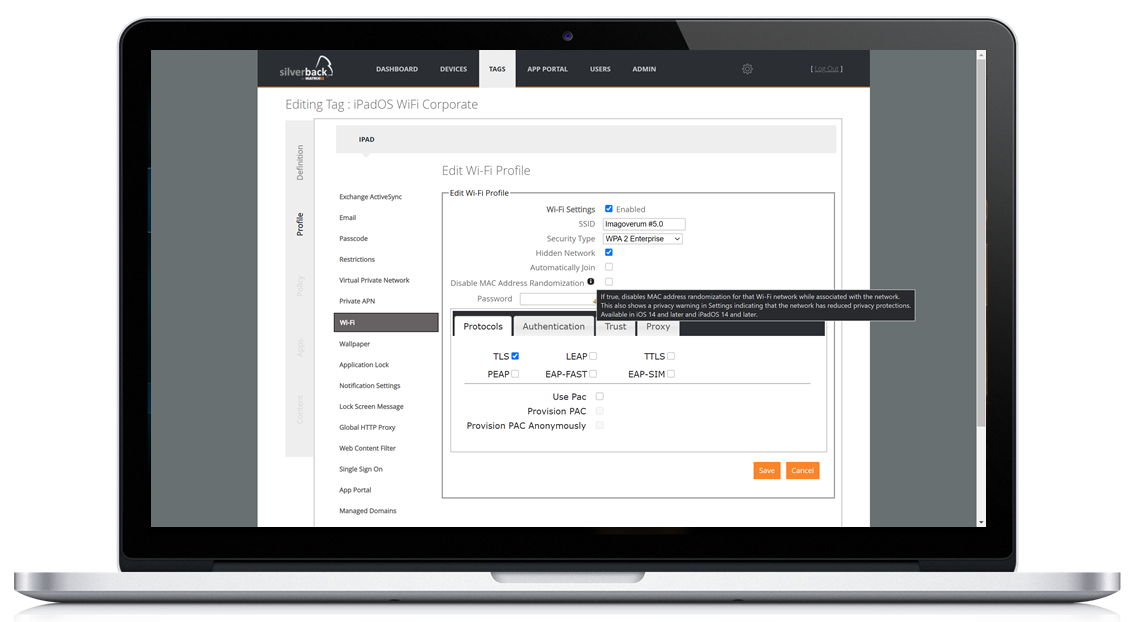
Control and disable MAC-Address Randomization
iOS14 and iPadOS14 brings a new privacy feature which will increase the level of privacy on devices for users. Until iOS13 each device had a physical device MAC-Address to identify devices within a network uniquely. With iOS14 this privacy feature is an option to use a private or randomized MAC-address when connecting a Wi-Fi network. Generally, devices identify themselves using the same MAC address when connecting to networks, which can allow tracking by network operators or organizations. Due to news announcements this feature might bring issues to administrators or organizations which are relying on the capability to identify devices. Also Cisco announced earlier that in particular cases and environments the randomized MAC-address may cause network issues. With the Disable MAC Address Randomization feature we ensure that Administrators can preset the MAC-Address Randomization option for deployed Wi-Fi Profiles on managed devices to disabled.
Disabling the MAC Address Randomization will initially disable the private address setting on the device for the particular Wi-Fi , but users will be still able to enable this setting.
With iOS and iPadOS 14.3, the private address setting is not changeable anymore by the user.
Configure Notification Preview
Notification Control specifies the restriction to enforce notification settings for apps, using their bundle identifiers. This control offers Administrators the capability to define specific per app notifications on managed devices. Notifications can be disabled at all or be permitted to options like sounds only or disallow them in CarPlay. iOS14 and iPadOS14 brings a new management control for notifications with Show Preview. This feature will ensure that applications do not provide any preview on the lock screen and ensures the security level on managed devices. Imagine a message for a multi-factor authentication has been sent to the device. Without disabling the preview on the lock screen, attackers can easily get access to the verification code without needing the passcode for managed devices.
| Setting | Device |
|---|---|
| By default, notifications for applications are set to always show preview. In this case sensitive content from notifications might be visible on the lock screen. Attackers or any other person can read the content without the need to have direct physical access to the device or the necessity of knowing the passcode. |  |
| Silverback offers the possibility to reduce the security risk for managed supervised devices. Administrators can now control on a per application base the show preview options "Always", "When unlocked" or "Never". The options "When unlocked" and "Never" will prevent that sensitive information can be captured from the lock screen. |  |
Non-removable iOS apps selection
One important part of bringing managed devices into desired states, is to distribute and configure applications. Until iOS 13, Apple offered for Mobile Device Management systems the possibility to configure applications to the specific needs, including the following settings that are represented in the App Management section of each application:
- Automatically push to managed devices (Automatic Installation)
- Prevent Backup of App Data
- Take over the management if the app is already installed on the device
- Remove the application when the MDM Profile will be removed
Additionally with the Allow App Removal restriction, Administrators had or has the possibility to prevent that applications can be manually uninstalled by users on managed supervised devices. This setting reflects a globally enforced control which affects all installed applications on the device. Whenever this restriction has been enforced by Administrators, users are not able to uninstall any installed application on the device.
With iOS and iPadOS 14 Apple offers a new and more granular way to control application uninstallations, even for non-supervised devices. This means that the Administrator can now easily control per application, if it can be uninstalled or not and mark applications as mandatory. With Silverback 20.0 Update 3 you will find now for each application a checkbox "Allow Uninstallation" in the App Portal, in the Manage Config option in the Apps section of a Tag and in the Import settings for Apps purchased by the Volume Purchase Program.
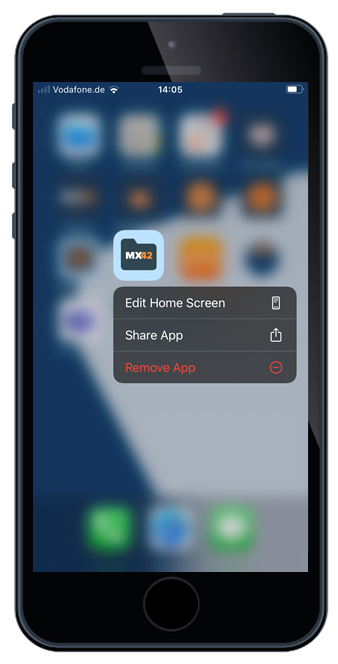 |
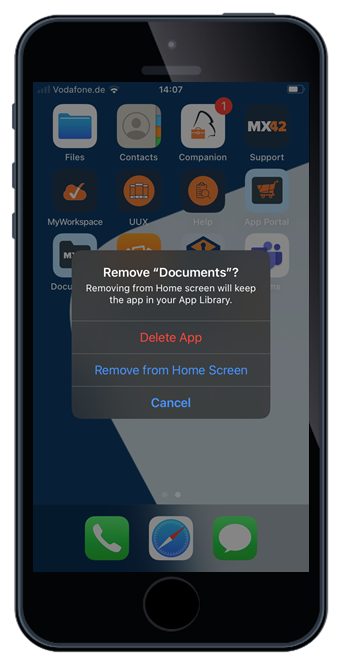 |
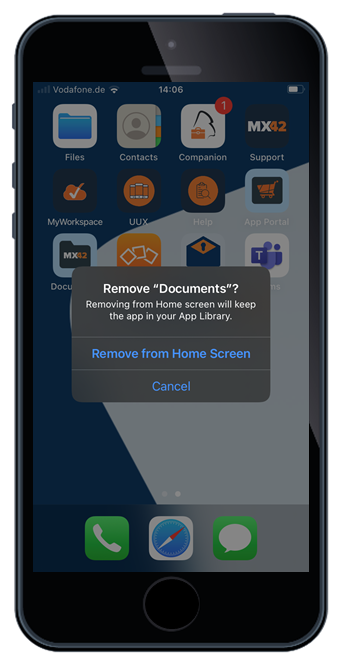 |
| Independent from the allow or disallow setting the "Remove App" button will be visible to users. | But with an enabled allow uninstallation setting users are able to use the "Delete App" button to remove the application from the device | With a disallowed uninstallation setting the "Delete App" button from the UI will be hidden to users |
Feature Pack for macOS Big Sur
In November 2020 Apple released with macOS Big Sur the new operating system on desktop devices. The new operating system includes a bunch of new management capabilities and changes for Administrators. As an example, any macOS device enrolled in a user approved enrollment will now be considered supervised, which will provide a greater control of managed devices. Additionally, the user approved enrollment received a slight change when adding the management profile. With macOS Big Sur users now need to confirm, as on iOS and iPadOS devices, the installation of the profile separately.
Please find all new related macOS Big Sur features for Silverback 20.0 Update 3 below:
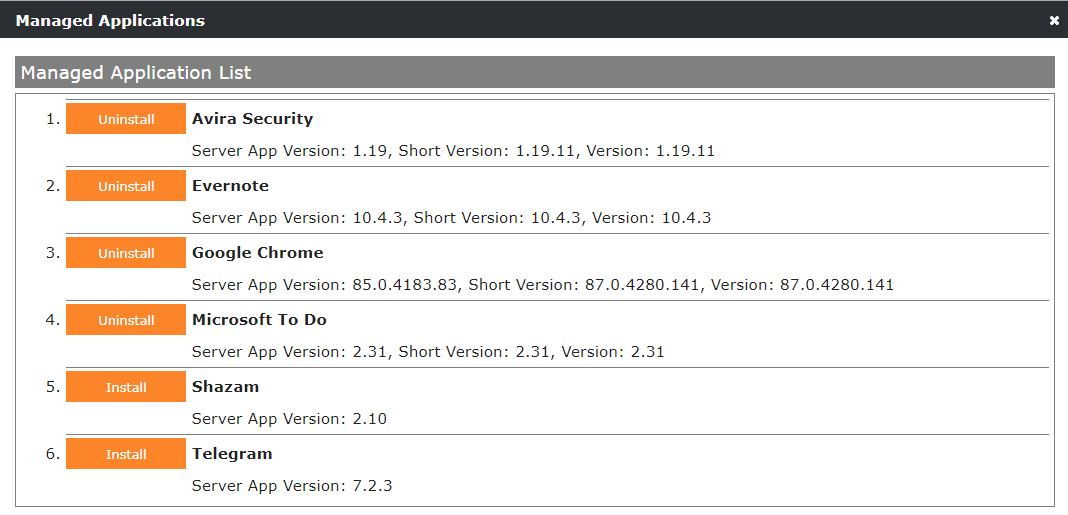
Remote uninstallation of applications
As an example, with Silverback Administrators can remotely install and uninstall applications through the Management Console. With the current macOS devices, the functionality is limited by the operating system to install applications only. Even if the device will be removed from the Management System, distributed applications will stay on the device. With macOS Big Sur it is now possible to remove managed applications from the device through the device management. If applications were installed through Silverback, an uninstall button is now shown for each application within the Managed Applications view.
macOS Big Sur has currently problems with installing VPP apps if the app has never been installed before. Please refer to Apple Developer Forum for additional information.
Force OS Updates
Apple releases a new major operating system for macOS every year, followed by several intermediate updates and companies struggles usually with the three different types of users:
The first ones are users that will update to the new operating system on the day one when the device pings that a new OS Update is available. This usually is a bit risky when applications are used that might not be updated in an appropriate time and might not work with the newest update. For that the possibility to defer updates to 90 days already in the last release. The second group is a very sensitive group of users which might ask the IT department if it will be ok to install the new operating system and the department can answer based on the experience they already have.
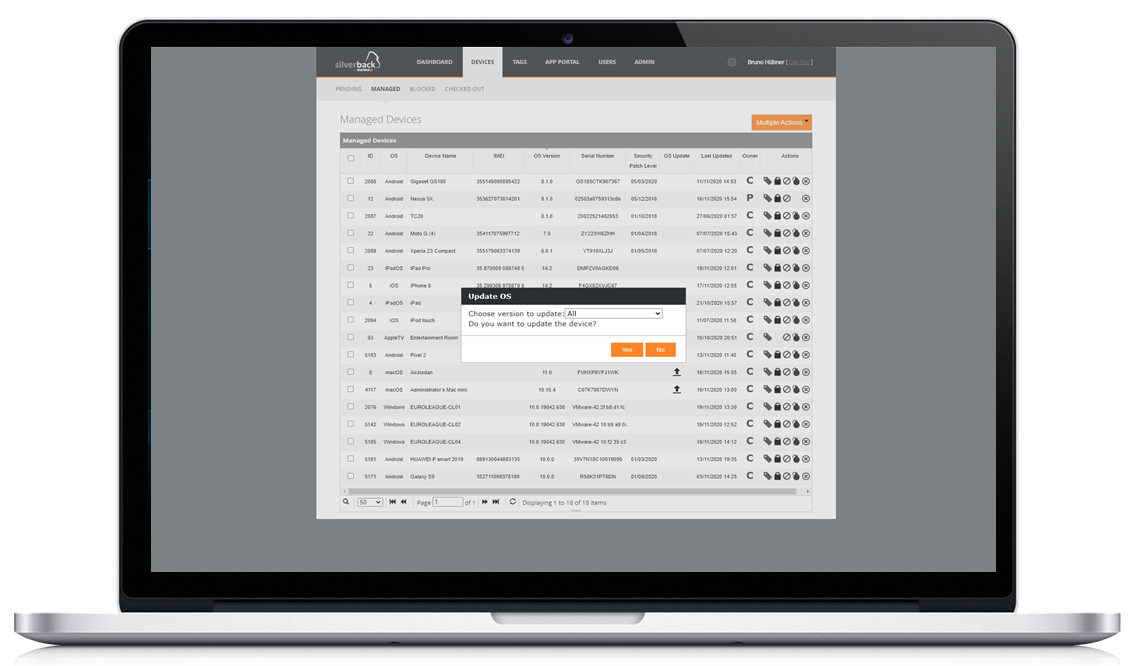
Then you a third group of where you have to deal with people which will never update the operating system, even months and years after they appeared. This leads most of the time into a security issue. For this group and in general Silverback offers already the possibility to control OS updates with settings, where Administrators can keep macOS devices on the highest available operating system.
But you as an Administrators might not want to have at the day one a global rollout of a new macOS version, so we added with Silverback 20.0 Update 3 the capability to decide for each device, to force an Operating System Update in case a Software Update profile for automatic updates is not used. As for iOS and iPadOS devices an indication of an available update is now as well present for macOS in the OS Update column in the devices tab. With a click on it, the device will represent all available updates, which Administrators can force for a specific or for all present updates.
Forcing Operating System updates requires a supervised device.
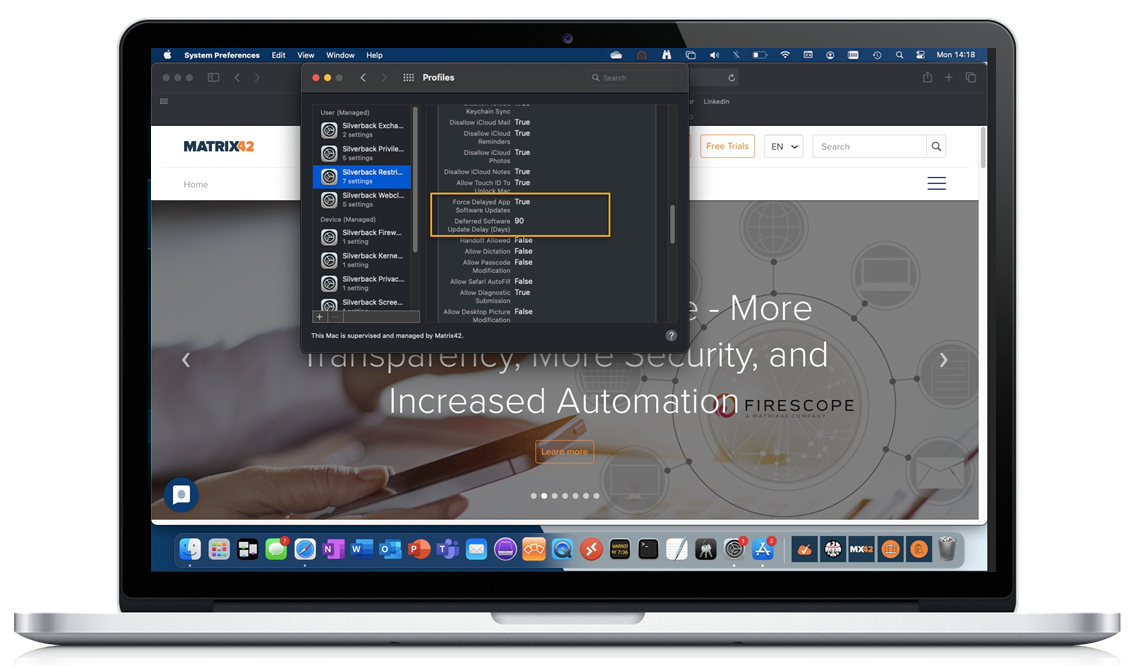
Defer Non-operating system updates
Silverback 20.0 Update 3 ensures a more granular option to delay OS Updates on macOS BigSur. The existing Defer Operating System Updates setting has been extended with the Defer Non-operating System Updates option. The timeframe for defer updates will apply to Operating System Updates and Non-Operating System Updates. The delay can be set from 1 day up to 90 days.
Endpoint Protection Features for Windows 10
With Silverback 20. Update 2, we added new security and privacy settings for Windows 10 devices into the management system. This included receiving important defender information from the device fleet, a control mechanism for operating system updates or the extension of BitLocker settings for device encryption and configuring the Windows Defender Firewall. With Silverback 20.0 Update 3, we increased the management capabilities with new restrictions, the configuration of the Defender Security application, SmartScreen settings for Windows 10 and new Power Management options. Please find all the new capabilities below:
Configure devices with new restrictions
Overall Silverback 20. Update 3 provides over 20 new restrictions, that allow Administrators to configure devices to the specific needs and requirements of the organization. With the Restriction Spotlight we want to provide some insights how restrictions reduce the possibilities for users to change specific settings or execute specific tasks, like to end the Task Manager or redirect user profiles on the file system. All new restrictions are covered within the Overview of new Restrictions.
Restriction Spotlight
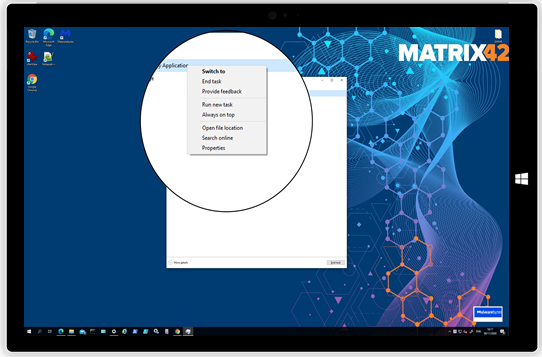
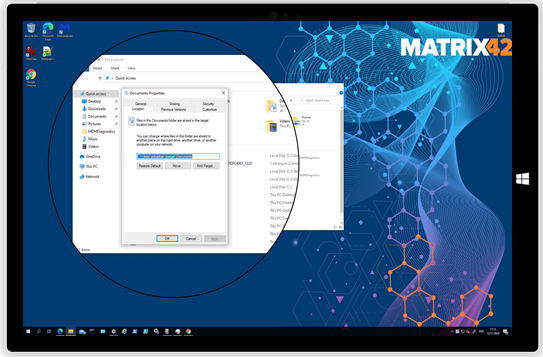
The restrictions spotlight shows that users as an example will not be able anymore to End Tasks in Task Manager or redirect their User Profiles.
 |
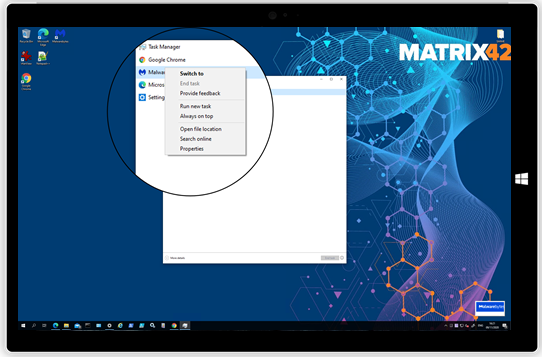 |
| A non-restricted configuration for the Task Manager grants users to End tasks. | Silverback 20.0 Update 3 grants the ability to Administrators to prevent non-administrative users from ending tasks in Task Manager |
 |
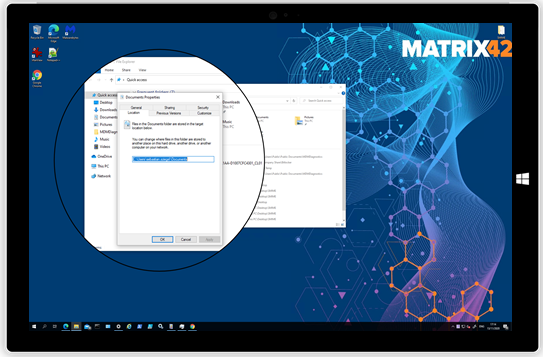 |
| A non-restricted configuration for the Desktop grants users to redirect profile folders to different locations. | Silverback 20.0 Update 3 grants the ability to Administrators to prevent users to redirect profile folders to different locations. |
Overview of new Restrictions
Please review all new Windows 10 Restrictions in Silverback 20.0 Update 3 below:
| Setting | Availability | Options | Requirement | Description |
|---|---|---|---|---|
| Desktop | ||||
| Prevent User Redirection of Profile Folders |
|
|
Users can change by default the location of their individual profile folder like Pictures and Documents etc. by changing the path in the Locations section of the folders properties box. With this setting it is possible to prevent users from redirecting profile folders. | |
| Device Lock | ||||
| Prevent Lock Screen Slide Show |
|
|
Disables the lock screen slide show settings in the Settings App and prevents a slide show from playing on the lock screen. If disabled or not configured, users can enable and modify slide show settings. | |
| Event Log Service | ||||
| Allow Adding Events When Log File Reaches Maximum Size |
|
|
This restriction controls the Event Log behavior when the log file(s) reaches the maximum size. In a not configured state log files will overwrite old events if the log file reaches the maximum size. In an enabled state, new events will not be written into the log and are lost. | |
| Max Application Log File Size (KB) |
|
|
Defines the maximum log file size in KB for Application Logs. Supported values are from 1024 (1MB) to 2147483647 (2 TB). The default value is 20480 KB (20MB) | |
| Max Security Log File Size (KB) |
|
|
Defines the maximum log file size in KB for Security Logs. Supported values are from 1024 (1MB) to 2147483647 (2 TB). The default value is 20480 KB (20MB) | |
| Max System Log File Size (KB) |
|
|
Defines the maximum log file size in KB for System Logs. Supported values are from 1024 (1MB) to 2147483647 (2 TB). The default value is 20480 KB (20MB) | |
| File Explorer | ||||
| Turn Off Data Execution Prevention for Explorer |
|
|
If enabled, data execution prevention can allow certain legacy plug-in applications to function without terminating the Explorer. | |
| Turn Off Heap Termination on Corruption |
|
|
If enabled, heap termination on corruption can allow certain legacy plug-in applications to function without terminating Explorer immediately, although Explorer may still terminate unexpectedly later. | |
| Games | ||||
| Allow Advanced Gaming Services |
|
|
|
Specifies if advanced gaming services can be used on the device. Advanced gaming services may send data to Microsoft or games publishers that use these services. |
| Handwriting | ||||
| Handwriting Panel Default Mode |
|
|
|
Defines the default mode for the handwriting panel.
|
| Lock Down | ||||
| Allow Edge Swipe |
|
|
|
This setting controls if a user is able to invoke the system user interface by swiping in from any screen edge using touch. |
| Maps | ||||
| Allows Auto-Update Over Metered Connection |
|
|
|
Controls whether the download and update of map data over metered connection is forced to disabled or forced to enabled. |
| Turn Off Automatic Download and Update of Map Data |
|
|
|
Controls whether the automatic download and update of map data is forced off (disabled) or forced on (enabled). |
| Messaging | ||||
| Allow Message Sync |
|
|
|
Allows or disallows users to backup and restore text messages and use Messaging Everywhere. Disabling this policies will avoid that information are stored on non-organization cloud servers. If disabled, message sync is not allowed and can't be changed by the user. |
| Notifications | ||||
| Turn Off Notification Network Usage |
|
|
|
This restriction block applications from using the network to send tile, badge, toasts and raw notifications. We highly recommend to not enable this restriction. It might cause issue in the device communication with the backend server. |
| Turn Off Notification Mirroring |
|
|
|
If enabled, application and system notifications will not be mirrored to other user devices. |
| Turn Off Tile Notification |
|
|
|
If enabled, applications and system features will not be able to update their tiles and badges in the start screen. |
| Speech | ||||
| Allow Automatic Update of Speech Data |
|
|
|
Specifies if devices will periodically check and receive updates to the speech recognition and synthesis models and download them from the Microsoft service using the Background Internet Transfer Service (BITS). |
| Task Manager | ||||
| Allow Use Task Manager to End Tasks |
|
|
|
Controls if non-administrators can utilize the Task Manager to end tasks. |
| Troubleshooting | ||||
| Troubleshooting Recommendations |
|
|
|
Allows to configure how to apply recommended troubleshooting for known problems on devices. |
| Windows PowerShell | ||||
| Allow PowerShell Script Logging |
|
|
Enables logging of all PowerShell script input in the Microsoft-Windows-Powershell/Operational event log. PowerShell will log, whether invoked interactively or through automation,the processing of commands, script blocks, functions and scripts. | |
| Log Script Block Invocation Start/Stop Events |
|
|
With enabled Log Script Block Invocation Start/Stop Events , PowerShell additionally logs when invocation of a command, script block, function, or script starts or stops. Enabling Invocation Logging generates a high volume of event logs. |
|
Defender Security Center
One part of the Endpoint Protection Features for Windows 10 in Silverback 20.0 Update 3 is the configuration of the built-in Microsoft Defender Security application, which offers protection settings against viruses, spyware and malware to users.
Overview
Windows 10 includes a built-in Windows Security Application, which provides the latest antivirus protection. Devices will be actively protected from the moment when a user starts Windows 10. Windows Security continually scans for malware (malicious software), viruses, and security threats. In addition to this real-time protection, updates are downloaded automatically to help to keep devices safe and protect it from threats. This security application has several sub settings pages like Virus & Threat Protection, Account Protection etc. and can be usually viewed and configured by users. With this feature we will grant Administrators to control the application appearance for managed devices.
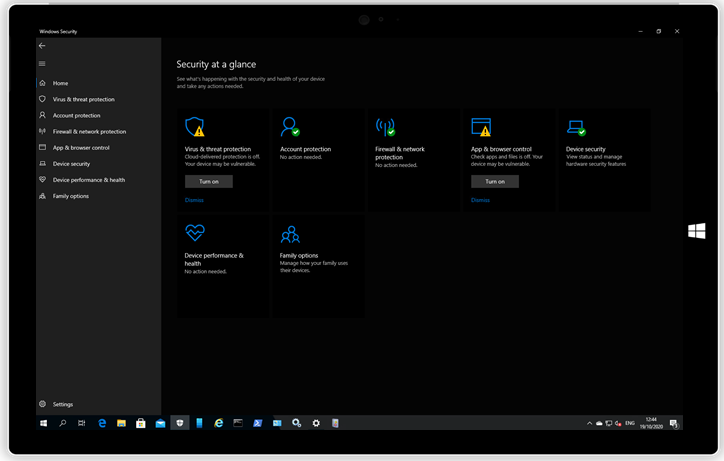 |
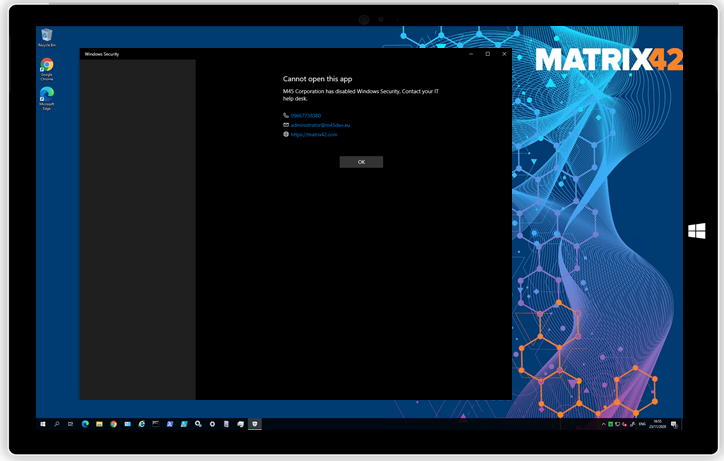 |
| A non-restricted configuration to the Windows Defender Security application grants users access to all settings and tabs within the applications. | Silverback 20.0 Update 3 grants the ability to Administrators to prevent users from starting the Microsoft Defender Security application. Instead of having access to all settings, users will receive the configured organizational IT contact information. |
Configuration
Please review all Microsoft Defender Security Center configurations in Silverback 20.0 Update 3 below:
| Setting | Availability | Options | Requirement | Description |
|---|---|---|---|---|
| Microsoft Defender Security Center app and notifications | ||||
| Defender Security Center |
|
|
Enabling this option will grant a customization of Microsoft Defender Security Center settings for managed devices. | |
| Virus and threat protection |
|
|
|
Configure if users can view the Virus and threat protection area in the Microsoft Defender Security Center. Hiding this section will also block all notifications related to Virus and threat protection |
| Ransomware data recovery |
|
|
|
Define if users can view the Ransomware data recovery area. Hiding this section will also block all notifications related to Ransomware protection. |
| Account protection |
|
|
|
Select whether users can view the Account protection area. Hiding this section will also block all notifications related to Account protection. |
| Firewall and network protection |
|
|
|
Specify if users can view the Firewall and network protection area. Hiding this section will also block all notifications related to Firewall and network protection. |
| App and browser Control |
|
|
|
Configure if users can view the App and browser control area. Hiding this section will also block all notifications related to App and browser control. |
| Exploit protection settings modifying |
|
|
|
Prevents users from making changes to the exploit protection settings area. |
| Device performance and health |
|
|
|
Select whether users can view the Device performance and health area or not. Hiding this section will also block all notifications related to this section. |
| Family options |
|
|
|
Configure if users can view the Family options in the Microsoft Defender Security center application. Hiding this section will also block all notification related |
| Device security area |
|
|
|
Use this setting to disable the display of the Device security area. |
| TPM Troubleshooter page |
|
|
|
Use this setting to disable the display of the Device security area. |
| Clear TPM button |
|
|
|
Configures if the Clear TPM button within the Security processor troubleshooting area is shown to users. |
| TPM firmware update warning |
|
|
|
Defines if recommendations to update the TPM Firmware are shown when a vulnerable firmware is detected. |
| Secure boot area |
|
|
|
Use this setting to hide the Secure boot area. |
| Windows Security Center icon in the system tray |
|
|
|
Specifies whether the Windows Security Center is shown as a tray icon in the Taskbar or is hidden. |
| Hide all notifications |
|
|
|
Determines if notifications will be displayed on devices. If hide is selected, users can't see Windows Defender Security Center notifications. |
| Hide non-critical notifications |
|
|
|
Determines if non-critical notifications will be displayed on devices. If hide is selected, Windows Defender Security Center only display notifications which are considered as critical. |
| IT contact information | ||||
| Display contact information in app |
|
|
|
Enabling this policy will display a customized company name and contact information in a contact fly out from Windows Defender Security Center. If not enabled or without a provided company name or a minimum of one contact method Windows 10 will not display the contact fly out notification. |
| Display contact information in notifications |
|
|
|
Enabling this policy will display a customized company name and contact information in the notifications. If not enabled or without a provided company name or a minimum of one contact method Windows 10 will display a default notification text |
| Specify contact company name |
|
e.g. Imagoverum |
|
Provides a predefined company name in contact fly outs and notifications. |
| Contact phone number or Skype ID |
|
e.g +4969667788650 |
|
Provides a predefined phone number or Skype ID in contact fly outs and notifications. Skype will be used to initiate the call. |
| Contact email address |
|
e.g. support@imagoverum.com |
|
Provides a predefined email address in contact fly outs and notifications. The default mail application will be used to initiate email actions. |
| Contact website |
|
e.g. https://imagoverum.com |
|
Provides a predefined help portal website in contact fly outs and notifications. The default browser will be used to initiate this action |
Microsoft Defender SmartScreen
Microsoft Defender SmartScreen is a built-in threat protection of Windows 10 and Microsoft Edge that protects users and your organization against phishing or malware websites and applications and the downloading of potentially malicious files. With Silverback 20.0 Update 3 all Microsoft Defender SmartScreen options are present in a standalone profile to configure SmartScreen in Microsoft Edge and Windows 10 together. Microsoft Edge settings were previously part of the Browser Restrictions. All other settings are new functionalities coming with Silverback 20.0 Update 3. Please review additional information here: Microsoft Defender SmartScreen
| Setting | Availability | Options | Requirement | Description |
|---|---|---|---|---|
| Microsoft Edge | ||||
| Configure Windows Defender SmartScreen |
|
|
|
Microsoft Edge is using Windows Defender SmartScreen for protecting users from potential security risks by default. Enabling this setting will protect users from potential threads and prevents users from turning SmartScreen on or off in Microsoft Edge. Disabling this setting will not protect users from threats and will prevent users from turning SmartScreen on. |
| Prevent Bypassing Windows Defender SmartScreen Prompts for Sites |
|
|
|
Microsoft Edge allows by default users to bypass or ignore Defender SmartScreen warnings about potentially malicious sites to access them. Enabling this setting will prevent users from bypassing the warnings. |
| Prevent Bypassing Windows Defender SmartScreen Prompts for Files |
|
|
|
By default, Microsoft Edge allows users to bypass or ignore warnings about potentially malicious when downloading unverified files. Enabling this setting will prevent users from bypassing the warnings and block the download of unverified files. |
| Reputation-based protection | ||||
| Check apps and files |
|
|
|
Configures the Microsoft Defender SmartScreen for Windows 10. |
| File execution | ||||
| Ignore Warnings and Run Malicious Files |
|
|
|
Defines if users can ignore SmartScreen warnings and run malicious files. |
| Source-based protection | ||||
| Install Apps only from Microsoft Store |
|
|
|
Allows to control whether users are allowed to install apps only from the Microsoft App Store. Installations are only blocked if the device is online. For blocking offline installation, Check apps and files must be set to Enabled and Ignore Warnings and Run Malicious Files to Block. |
Power Management Options for Windows 10
Windows 10 brings the ability to control the Power & Sleep Settings for devices. This helps and ensures Administrator to economic protection and saving money for energy costs within the organization. With Silverback 20.0 Update 3 we provide Administrators the control of power management options for Windows 10 like:
- Manage whether or not Windows is allowed to use standby states when putting the computer in a sleep state.
- Specify the period of inactivity before Windows turns off the display.
- Specify the period of inactivity before Windows transitions the system to sleep.
- Specify battery charge level at which Energy Saver is turned on.
- Prompt for a password when the system resumes from sleep.
| Setting | Availability | Options | Requirement | Description |
|---|---|---|---|---|
| Predefine Lid Switch Action |
|
|
|
Specifies the action that Windows 10 takes when the user closes the lid on the device. |
| Predefine Power Button Action |
|
|
|
This setting specifies the action that Windows 10 takes when the user presses the power button. |
| Predefine Sleep Button Action |
|
|
|
This setting specifies the action that Windows 10 takes when the user presses the sleep button. |
| Use Standby States When Putting the Computer in a Sleep State |
|
|
This option manages whether or not Windows 10 is allowed to use standby states when putting the computer in a sleep state. | |
| Specify Inactivity Timeout Before Windows Turns Off the Display |
|
|
|
Allows to specify the period of inactivity before Windows 10 turns off the display. If enabled, a value for Set Screen Off Inactivity Timeout (seconds) is required. |
| Set Screen Off Inactivity Timeout (seconds) |
|
e.g. 300 |
|
Defines the idle time in seconds should elapse before Windows 10 turns off the display. |
| Specify Period of Inactivity Before Hibernating |
|
|
|
This setting allows to specify the period before Windows 10 transitions to hibernate. If enabled, a value for Inactivity Timeout for Hibernating (seconds) is required. If the user has configured on the lock screen a slide show and the device is locked, this can prevent the sleep transitions. Please refer to Restrictions > Device Lock |
| Inactivity Timeout for Hibernating (seconds) |
|
e.g. 300 |
|
Defines how much idle time should elapse before Windows 10 transitions to hibernate. |
| Specify Inactivity Timeout Before Windows Turns Into Sleep |
|
|
|
Allows to specify the period of inactivity before Windows 10 transitions to sleep. If enabled, a value for Sleep Inactivity Timeout (seconds) is required. If the user has configured on the lock screen a slide show and the device is locked, this can prevent the sleep transitions. Please refer to Restrictions > Device Lock |
| Sleep Inactivity Timeout (seconds) |
|
e.g. 300 |
|
Defines how much idle time should elapse before Windows 10 transitions to sleep. |
| Specify Inactivity Timeout for Unattended Sleep |
|
|
|
Allows to specify the period of inactivity before Windows transitions to sleep automatically when a user is not present at the computer. If enabled, a value for Unattended Sleep Timeout (seconds) is required. If the user has configured on the lock screen a slide show and the device is locked, this can prevent the sleep transitions. Please refer to Restrictions > Device Lock |
| Unattended Sleep Timeout (seconds) |
|
e.g. 300 |
|
Defines how much idle time should elapse before Windows 10 transitions automatically to sleep when left unattended. A value of 0 seconds results in Windows does not automatically transition to sleep. |
| Require a Passcode When the System Resumes From Sleep |
|
|
If this setting is disabled, the user is not prompted for a password when the system resumes from sleep. | |
| Allow Hybrid Sleep |
|
|
|
Specifies whether Hybrid Sleep mode is allowed or not. Hybrid Sleep mode is a combination of the Sleep and Hibernate modes desktops. If you disable this setting, a hiberfile is not generated when the system transitions to Sleep. |
| Specify Battery Level for Energy Saver Activation |
|
|
|
This setting allows to specify the battery charge level at which Energy Saver is turned on. The Energy Saver will automatically turn on at (and below) the specified battery charge level. If enabled, a value for Battery Level (percentage) is required. |
| Battery Level (percentage) |
|
e.g. 30 |
|
Defines a percentage value that indicates the battery charge level when Energy Saver turns on. Supported values are 0-100. Default value is 70. |
Enhancements for Android Management
Please review all new Android Management enhancements in Silverback 20.0 Update 3 below:
New Onboarding Wizard
With the upcoming release of Companion 20.0 Update 3, the enrollment process for Android and Samsung Safe devices will change to a new wizard driven and more user friendly enrollment. In the first screen users will be informed about all upcoming steps for the device enrollment, which will be followed by a privacy overview of what information organizations can and may see from users and from managed devices. Before users are requested to grant the required application permissions, they will get informed about why each permission is requested. This ensures a better understanding of each permission and what organizations can gain by them. After the wizard, the enrollment process still remains with the two options of scanning the QR-Code or entering the authentication details manually.
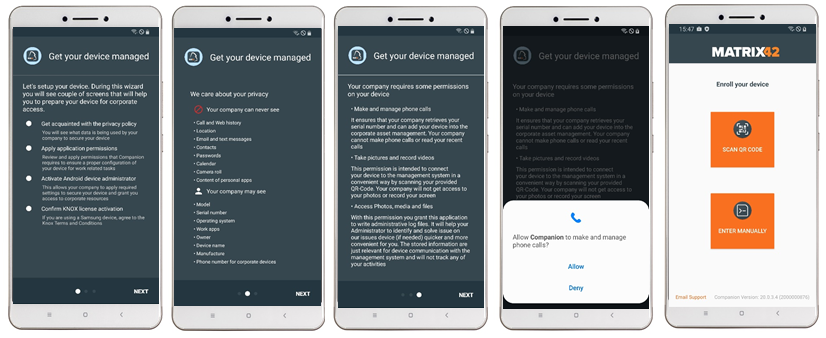
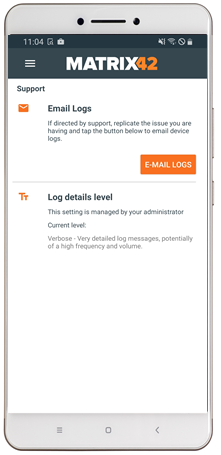
Remote Log Level Configuration
Logging and debugging is an important part for troubleshooting scenarios. With Silverback 20.0 Update 3 Administrators can granularly and remotely control the log level for the Companion application. By default the log level will be applied to Info within the System Tag. In case of troubleshooting scenarios Administrators can create a new Tag and set the Log level to any of the other offered levels, like Debug or Verbose and apply this Tag to affected devices. The Log Level is represented within the Companion under the Support section. Users will not be able to change manually the log level on managed devices.
In case of assigning multiple tags with different levels, the setting will win from top (Verbose) to down ( Error)
Change the Log Level to Debug or Verbose only in case of troubleshooting.
| Option | Description | Device |
|---|---|---|
| Verbose | Very detailed log messages, potentially of a high frequency and volume |
|
| Debug | Less detailed and/or less frequent debugging messages | |
| Info (default) | Informational messages | |
| Warn | Warnings which don't appear to the user of the application | |
| Error | Error messages |
Certificate Profile for VPN and Apps (Preview)
This feature is marked as preview because not all end to end tests were covered until of today. Please expect that not all use-cases were covered at this point.
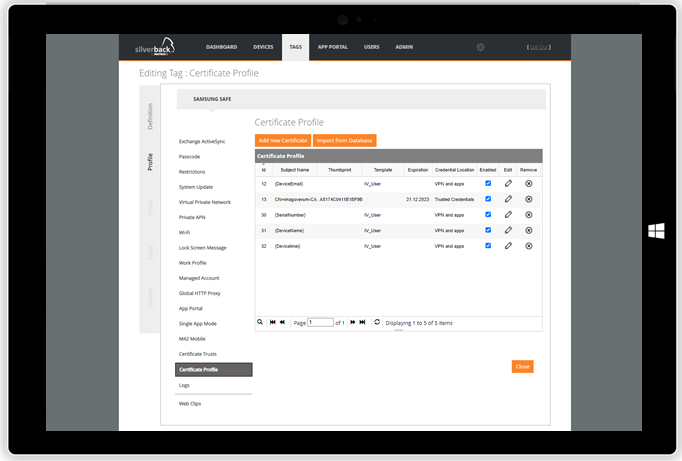
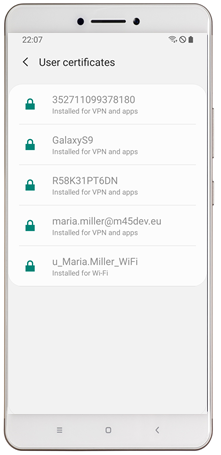
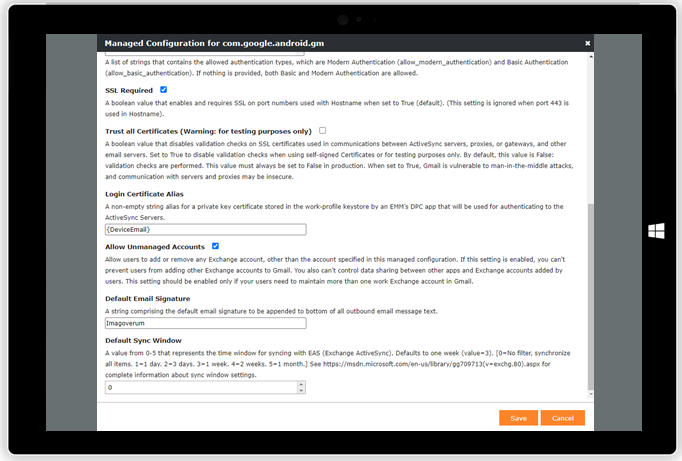
With Silverback you can use certificates to authenticate your users to applications and corporate resources like E-Mail, Wi-Fi and Virtual Private Networks. Distributing certificates facilitates the access for a seamless authentication without the need to enter any usernames or passwords. On Android Enterprise and with Managed Configurations application configurations are made very easy for any Administrators. With Silverback 20.0 Update 3 we want to introduce the preview of a new mechanism for distributing certificates to devices, which is dedicated to meet the great capabilities of Managed Configurations. This feature ensures that certificates from the new certificate profile are distributed to your managed devices and an alias can be provided in any supported Managed Configuration (e.g Gmail, Samsung Mail, Cisco AnyConnect, F5 Access etc.) to pre-choose certificates on the devices for VPN and other applications for the user. With the new profile you will benefit form the following:
- Created certificate profiles can be imported easily in other tags
- Trusted Credentials and VPN and Apps can be selected as credential location
- For VPN and Apps Enterprise Certificates with private keys can be uploaded and/or
- For VPN and Apps Individual Client Certificates can be configured
- Individual client certificates supports different templates
- Alias and Subject names are supporting System Variables and can be used in Managed Configurations
- Certificate Locations can be addressed for all supported management types
 |
 |
| Create one or multiple profiles within Tags | Certificates will be distributed to managed devices |
 |
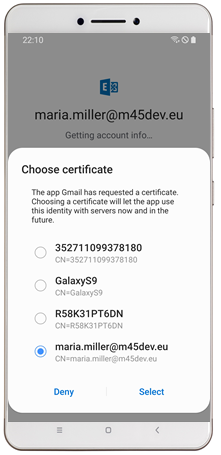 |
| Configure Gmail Account through Managed Configuration | In case of multiple present certificates, thealias will be pre-selected |
 |
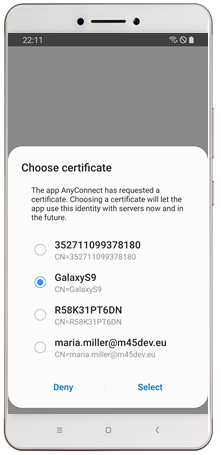 |
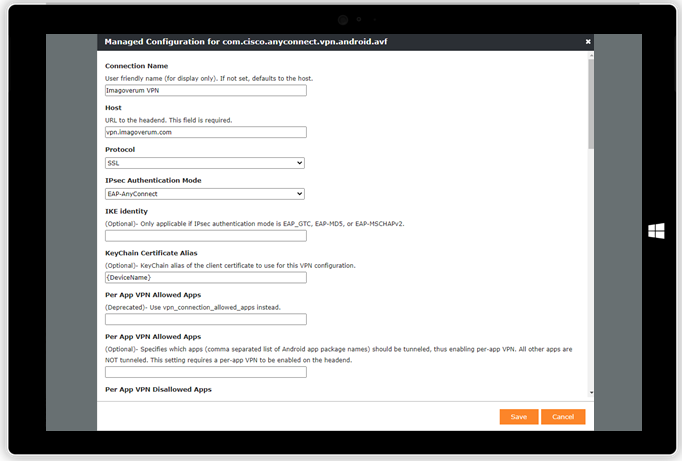
| Configure your Cisco AnyConnect VPN connection through Managed Configurations | In case of multiple present certificates, the alias will be pre-selected |
Improvements
- Added 190 new device models
- Windows 10 Restriction settings inside Tags have now a dedicated enabled or disabled setting
- New System App Translate has been added for iOS and iPadOS 14
- Improvements for French translations
- Solved the problem of requiring a passcode by default
- Solved the problem where device capacity for Android is sent in a negative value or is not shown
- Solved the problem where incorrect values for Service Bus lead to an error in Console
- Solved the problem that empty values for device and app conditions set the value to 0 in App Protection
- Solved a problem where application blacklist or whitelist result is empty in resultant tag
Changes
- Change to HTTP/2-based APNs provider API
- Change to Set Product Availability Policy for Android Enterprise Managed Play to whitelist
Known Issues
- Issue: Defer Operating System Updates on macOS devices will be set as 30 days deferral period by default.
- Workaround: Create a Tag and assign a different deferral period.
- Save & Close buttons might not work properly in all areas
- Workaround: Use save button instead.