Release Notes Silverback 20.0 Update 2
About This Release
Matrix42 Silverback 20.0 Update 2 provides new and improved features that have been implemented. During the development of this version, we have been focusing on valued feedback from our customers and partners in order to provide an ideal feature selection.
Please find the installation files of this version on Matrix42 Marketplace.
System requirements, integration guides and instructions for installation and update are available in the Matrix42 Help Center.
Important Announcements
Knox Validated Program Membership
The Knox Validated Program is a new authentication program for Samsung partners with Unified Endpoint Management, Enterprise Mobility Management, and Mobile Device Management solutions integrated with the Samsung Knox platform and solution. We have been tightly cooperating with our colleagues from Samsung for the past several months and we are happy to announce that we have successfully received the certificate as a Knox Validated Program Member. Customers deploying the Knox Validated solutions can have the confidence that our solution has been evaluated by the solution experts at Samsung and has met the requirements in order to receive the stamp of validation.

Operating System Review
During this development phase of our product we reviewed all current beta version of upcoming releases for the following operating systems:
- iOS 14
- iPadOS 14
- macOS 11.0
- Android 11
At os today all platforms are supported out of the box, so that a Silverback update for supporting the new versions isn't required.
Overview
- UUX for SUEM
- Restriction Updates
- Security Feedback on Android Enterprise
- Windows 10 Security and Privacy
- macOS Applications and Operating System
New Features
UUX for SUEM
We've added valuable information to the Secure Unified Endpoint Management. Please find all new information listed below.
Device Information
The following device information will now be sent over the Service Bus to the UUX for SUEM. Within the UUX perform a double click on the device and navigate through the corresponding target fields.
| Information | UUX |
|---|---|
| Supervised | Management > Overview |
| Device Owner | Management > Overview |
| Lost Mode | Management > Overview |
| Active Sync ID | Management > Mobile Data |
| Device ID | Identification > Import Identifiers |
| Device Capacity used | Inventory > Equipment Data |
| Device Capacity | Inventory > Equipment Data |
| Battery Level | Inventory > Equipment Data |
Profile Information
Besides the extended device information, we added the Profile List to be sent over the Service Bus to the UUX for SUEM. Within the UUX perform a double click on the devices and navigate to Management to view installed profiles.
Defender Antivirus Information
With this Release, we added the Defender Antivirus Information for Windows 10 devices into the Silverback Management Console and additionally we are sending these information to the Secure Unified Endpoint Management Console as well.

Restriction Updates
Silverback 20.0 Update 2 provides a complete revised experience with restrictions. At glance restrictions are now grouped by categories to provide a better user experience and we've added overall 68 new valuable device configuration options.
New Restriction Grouping
All restrictions for all supported platforms are now grouped and can be expanded and collapsed with one click. Please find the overview about the available categories sorted by management type below.
| Android Enterprise | |
|---|---|
| Management Type | Android Enterprise |
| Categories |
|
| Management Type | Samsung Safe |
| Categories |
|
| iOS, iPadOS | |
| Management Type |
General |
| Categories |
|
| Management Type |
Supervised |
| Categories |
|
| macOS | |
| Management Type | All |
|
|
New Restrictions for iOS, iPadOS
Additionally we've added 36 new restrictions for iOS and iPads. With these missing items we arrived at the 100% level of device configuration via restrictions for iPhones and iPadsuntil iOS13.
| Restrictions | Availability | Options | Requirement | Description |
|---|---|---|---|---|
| Applications | ||||
| Allow Apple Music Radio |
|
Enabled or Disabled | iOS 9.3 (supervised) | If false, disables Apple Music Radio. Requires a supervised device. Available in iOS 9.3 and later. |
| Allow System Apps Removal |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables the removal of system apps from the device. Requires a supervised device. Available in iOS 11 and later. |
| The Maximum Level of App Content Allowed on The Device |
|
|
iOS 4 | The maximum level of app content allowed on the device. Available in iOS 4 and later. |
| The Maximum Level of Movie Content Allowed on The Device |
|
|
iOS 4 | The maximum level of movie content allowed on the device. Available in iOS 4 and later. |
| App Store & iTunes | ||||
| Allow Enterprise Book Backup |
|
Enabled or Disabled | iOS 8 | If false, disables backup of Enterprise books. Available in iOS 8 and later. Also available for user enrollment. |
| Allow Enterprise Book Sync |
|
Enabled or Disabled | iOS 8 | If false, disables sync of Enterprise books, notes, and highlights. Available in iOS 8 and later. Also available for user enrollment. |
| Network & Connection | ||||
| Allow Cellular Plan Modification |
|
Enabled or Disabled | iOS 11 (supervised) | If false, users can't change any settings related to their cellular plan. Requires a supervised device. Available in iOS 11 and later. |
| Allow eSIM Modification |
|
Enabled or Disabled | iOS 12.1 (supervised) | If false, disables modifications to the eSIM setting. Requires a supervised device. Available in iOS 12.1 and later. |
| Allow USB Restricted Mode |
|
Enabled or Disabled | iOS 11.4.1 (supervised) | If false, allows the device to always connect to USB accessories while locked. Requires a supervised device. Available in iOS 11.4.1 and later. |
| Allow VPN Creation |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables the creation of VPN configurations. Requires a supervised device. Available in iOS 11 and later. |
| Force AirPlay Outgoing Requests Pairing Password |
|
Enabled or Disabled | iOS 7.1 | If true, forces all devices receiving AirPlay requests from this device to use a pairing password. Available in iOS 7.1 and later. Also available for user enrollment. |
| Managed Open-In | ||||
| Allow Managed Apps Write Contacts to Unmanaged |
|
Enabled or Disabled | iOS 12 | If true, managed apps can write contacts to unmanaged contacts accounts. If Allow Open In from Managed to Unmanaged Apps is true, this restriction has no effect. Available in iOS 12 and later. |
|
Allow Unmanaged Apps to Read Managed Contacts |
|
Enabled or Disabled | iOS 12 | If true, unmanaged apps can read from managed contacts accounts. If Allow Open In from Managed to Unmanaged Apps is true is true, this restriction has no effect. Available in iOS 12 and later. Also available for user enrollment. |
| Printing | ||||
| Allow AirPrint |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables AirPrint. Requires a supervised device. Available in iOS 11 and later. |
| Allow AirPrint Credentials Storage |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables keychain storage of user name and password for AirPrint. Requires a supervised device. Available in iOS 11 and later. |
| Allow AirPrint iBeacon Discovery |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables iBeacon discovery of AirPrint printers, which prevents spurious AirPrint Bluetooth beacons from phishing for network traffic. Requires a supervised device. Available in iOS 11 and later. |
| Force AirPrint Trusted TLS Requirement |
|
Enabled or Disabled | iOS 11 (supervised) | If true, requires trusted certificates for TLS printing communication. Requires a supervised device. Available in iOS 11 and later |
| Siri | ||||
| Allow Siri User-Generated Content |
|
Enabled or Disabled | iOS 7 | If false, prevents Siri from querying user-generated content from the web. Requires a supervised device. Available in iOS 7 and later. |
| Force Assistant Profanity Filter |
|
Enabled or Disabled | iOS 11 (supervised) | If true, forces the use of the profanity filter assistant. Requires a supervised device. Available in iOS 11 and later. |
| Security & Privacy | ||||
| Allow Diagnostic Data to be Modificated |
|
Enabled or Disabled | iOS 9.3.2 (supervised) | If false, disables changing the diagnostic submission and app analytics settings in the Diagnostics & Usage UI in Settings. Requires a supervised device. Available in iOS 9.3.2 and later. |
| Allow Fingerprint Modification |
|
Enabled or Disabled | iOS 8.3 (supervised) | If false, prevents the user from modifying Touch ID or Face ID. Requires a supervised device. Available in iOS 8.3 and later. |
| Allow Password AutoFill |
|
Enabled or Disabled | iOS 12 (supervised) | If false, disables the AutoFill Passwords feature in iOS (with Keychain and third-party password managers) and the user isn't prompted to use a saved password in Safari or in apps. This restriction also disables Automatic Strong Passwords, and strong passwords are no longer suggested to users. It does not prevent AutoFill for contact info and credit cards in Safari. Requires a supervised device. Available in iOS 12 and later, and macOS 10.14 and later. |
| Allow Password Proximity Requests |
|
Enabled or Disabled | iOS 12 (supervised) | If false, disables requesting passwords from nearby devices. Requires a supervised device. Available in iOS 12 and later. |
| Allow Password Sharing |
|
Enabled or Disabled | iOS 12 (supervised) | If false, disables sharing passwords with the Airdrop Passwords feature. Requires a supervised device. Available in iOS 12 and later. |
| Allow Proximity Setup to New Devices |
|
Enabled or Disabled | iOS 11 (supervised) | If false, disables the prompt to set up new devices that are nearby. Requires a supervised device. Available in iOS 11 and later. |
| Allow Untrusted TLS Certificates |
|
Enabled or Disabled | iOS 5 | If false, automatically rejects untrusted HTTPS certificates without prompting the user. Available in iOS 5 and later. |
| Force Authentication Before AutoFill |
|
Enabled or Disabled | iOS 11 (supervised) | If true, the user must authenticate before passwords or credit card information can be autofilled in Safari and Apps. If this restriction isn't enforced, the user can toggle this feature in Settings. Only supported on devices with Face ID or Touch ID. Requires a supervised device. Available in iOS 11 and later. |
| Shared Device & Classroom | ||||
| Allow Shared Device Temporary Sessions |
|
Enabled or Disabled | iOS 13.4 | If false, temporary sessions are not available on Shared iPad. Available in iOS 13.4 and later. |
| Force Classroom Automatically Join Classes |
|
Enabled or Disabled | iOS 11 (supervised) | If true, automatically gives permission to the teacher's requests without prompting the student. Requires a supervised device. Available in iOS 11 and later. |
| Force Classroom Requests Permission to Leave Classes |
|
Enabled or Disabled | iOS 11.3 (supervised) | If true, a student enrolled in an unmanaged course through Classroom requests permission from the teacher when attempting to leave the course. Requires a supervised device. Available in iOS 11.3 and later. |
| Force Classroom Unprompted Apps and Device Lock |
|
Enabled or Disabled | iOS 11 (supervised) | If true, allows the teacher to lock apps or the device without prompting the student. Requires a supervised device. Available in iOS 11 and later. |
| Force Classroom Unprompted Screen Observation |
|
Enabled or Disabled | iOS 11 (supervised) | If true and Allow Remote Screen Observation is also true in, a student enrolled in a managed course via the Classroom app automatically gives permission to that course teacher's requests to observe the student's screen without prompting the student. Requires a supervised device. Available in iOS 11 and later. |
| System Settings | ||||
| Allow Music Service |
|
Enabled or Disabled | iOS 9.3 (supervised) | If false, disables the Music service, and the Music app reverts to classic mode. Requires a supervised device. Available in iOS 9.3 and later. |
| Allow News |
|
Enabled or Disabled | iOS 9 (supervised) | If false, disables News. Requires a supervised device. Available in iOS 9 and later. |
| Allow Remote Screen Observation |
|
Enabled or Disabled | iOS 12 | If false, disables remote screen observation by the Classroom app. If Allow Screen Capture is set to false, the Classroom app doesn't observe remote screens. Required a supervised device until iOS 13. Available in iOS 12 and later. |
| Force Set Date and Time Automatically |
|
Enabled or Disabled | iOS 12 (supervised) | If true, enables the Set Automatically feature in Date & Time and can't be disabled by the user. The device's time zone is updated only when the device can determine its location using a cellular connection or Wi-Fi with location services enabled. Requires a supervised device. Available in iOS 12 and later. |
New Restrictions for macOS
We've added 32 new restrictions for macOS. With these missing items we arrived at the 100% level of device configuration via restrictions for macOS devices.
| Setting | Options | Requirement | Description |
|---|---|---|---|
| App Store & iTunes | |||
| Allow iTunes File Sharing Services | Enabled or Disabled | macOS 10.13 | If false, disables iTunes file sharing services. Available in macOS 10.13 and later. |
| Classroom | |||
| Force Classroom Automatically Join Classes | Enabled or Disabled | macOS 10.4.4 | If true, automatically gives permission to the teacher's requests without prompting the student. Requires a supervised device. Available in macOS 10.14.4 and later. |
| Force Classroom Requests Permission to Leave Classes | Enabled or Disabled | macOS 10.4.4 | If true, a student enrolled in an unmanaged course through Classroom requests permission from the teacher when attempting to leave the course. Requires a supervised device. Available in macOS 10.14.4 and later. |
| Force Classroom Unprompted Apps and Device Lock | Enabled or Disabled | macOS 10.4.4 | If true, allows the teacher to lock apps or the device without prompting the student. Requires a supervised device. Available in macOS 10.14.4 and later. |
| Force Classroom Unprompted Screen Observation | Enabled or Disabled | macOS 10.4.4 | If true and Allow Remote Screen Observation is also true, a student enrolled in a managed course via the Classroom app automatically gives permission to that course teacher's requests to observe the student's screen without prompting the student. Requires a supervised device. Available in macOS 10.14.4 and later. |
| iCloud | |||
| Allow iCloud Address Book | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Address Book services. Available in macOS 10.12 and later. |
| Allow iCloud Bookmarks | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Bookmark sync. Available in macOS 10.12 and later. |
| Allow iCloud Calendar | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Calendar services. Available in macOS 10.12 and later. |
| Allow iCloud Desktop and Documents | Enabled or Disabled | macOS 10.12.4 | If false, disables cloud desktop and document services. Available in macOS 10.12.4 and later. |
| Allow iCloud Document Sync | Enabled or Disabled | macOS 10.11 | If false, disables document and key-value syncing to iCloud. Available in macOS 10.11 and later. |
| Allow iCloud Keychain Sync | Enabled or Disabled | macOS 10.12 | If false, disables iCloud keychain synchronization. This restriction is deprecated on unsupervised devices and will be supervised only in a future release. Available in and macOS 10.12 and later. |
| Allow iCloud Mail Services | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Mail services. Available in macOS 10.12 and later. |
| Allow iCloud Notes Services | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Notes services. Available in macOS 10.12 and later. |
| Allow iCloud Photo Library | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Photo Library. Any photos not fully downloaded from iCloud Photo Library to the device are removed from local storage. Available in macOS 10.12 and later. |
| Allow iCloud Reminder Services | Enabled or Disabled | macOS 10.12 | If false, disables iCloud Reminder services. Available in macOS 10.12 and later. |
| Security & Privacy | |||
| Allow Auto Unlock | Enabled or Disabled | macOS 10.12 | If false, disallows auto unlock. Available in macOS 10.12 and later. |
| Allow Diagnostic Data to be Sent to Apple | Enabled or Disabled | macOS 10.13 | If false, prevents the device from automatically submitting diagnostic reports to Apple. Available in macOS 10.13 and later. Also available for user enrollment. |
| Allow Fingerprint For Unlock | Enabled or Disabled | macOS 10.12.4 | If false, prevents Touch ID or Face ID from unlocking a device. Available in macOS 10.12.4 and later. |
| Allow Passcode Modification | Enabled or Disabled | macOS 10.13 | If false, prevents the device passcode from being added, changed, or removed. Requires a supervised device. Available in macOS 10.13 and later. |
| Allow Password AutoFill | Enabled or Disabled | macOS 10.14 | If false, disables the AutoFill Passwords feature in iOS (with Keychain and third-party password managers) and the user isn't prompted to use a saved password in Safari or in apps. This restriction also disables Automatic Strong Passwords, and strong passwords are no longer suggested to users. It does not prevent AutoFill for contact info and credit cards in Safari. Requires a supervised device. Available in macOS 10.14 and later. |
| Allow Password Proximity Requests | Enabled or Disabled | macOS 10.14 | If false, disables requesting passwords from nearby devices. Requires a supervised device. Available in macOS 10.14 and later. |
| Allow Password Sharing | Enabled or Disabled | macOS 10.14 | If false, disables sharing passwords with the Airdrop Passwords feature. Requires a supervised device. Available in macOS 10.14 and later. |
| Allow Safari Autofill | Enabled or Disabled | macOS 10.13 | If false, disables Safari AutoFill for passwords, contact info, and credit cards and also prevents the Keychain from being used for AutoFill. Though third-party password managers are allowed and apps can use AutoFill. Available in macOS 10.13 and later. |
| Allow Spotlight Internet Results | Enabled or Disabled | macOS 10.11 | If false, disables Spotlight Internet search results in Siri Suggestions. Available in macOS 10.11 and later. |
| Sharing | |||
| Allow Content Caching | Enabled or Disabled | macOS 10.13 | If false, disables content caching. Available in macOS 10.13 and later. |
| System Settings | |||
| Allow Activity Continuation | Enabled or Disabled | macOS 10.15 | If false, disables activity continuation. Available in macOS 10.15 and later. |
| Allow Camera | Enabled or Disabled | macOS 10.11 | If false, disables the camera, and its icon is removed from the Home screen. Users are unable to take photographs. This restriction is deprecated on unsupervised devices and will be supervised only in a future release. Available in macOS 10.11 and later. |
| Allow Dictation | Enabled or Disabled | macOS 10.13 | If false, disallows dictation input. Requires a supervised device. Available in macOS 10.13 and later. |
| Allow Music Service | Enabled or Disabled | macOS 10.12 | If false, disables the Music service, and the Music app reverts to classic mode. Requires a supervised device. Available in macOS 10.12 and later. |
| Allow Screen Capture | Enabled or Disabled | ||
|
Allow Remote Screen Observation |
Enabled or Disabled | macOS 10.14.4 | If false, disables remote screen observation by the Classroom app. If Allow Screen Capture is set to false, the Classroom app doesn't observe remote screens. Required a supervised device until macOS 10.15. Available macOS 10.14.4 and later. |
| Allow Wallpaper Modification | Enabled or Disabled | macOS 10.14 | If false, prevents wallpaper from being changed. Requires a supervised device. Available macOS 10.13 and later. |
Security Feedback on Android
With this Release we are happy to announce two new features that will improve the security management capabilities for Administrator and a new application reporting method for Android Enterprise devices.
Android SafetyNet Attestation
The SafetyNet Attestation provides a cryptographically-signed attestation, assessing the device's integrity, which will help you to identify if devices in your device fleet has been tampered or modified. SafetyNet is an API provided by Google which validates software and hardware information on the device and creates a profile of that device, which then will be compared with certified devices. Based on the SafetyNet Attestation you will gain as an example the ability to detect devices with non-rooted custom ROMs or device emulators. The SafetyNet attestation provides different levels of integrity checks and thus intercepts different levels of security.
The Android SafetyNet Attestation requires the newest Companion version
| Information | Example | Description |
|---|---|---|
| Basic Integrity | Yes | Basic Integrity is a more lenient verdict of device integrity. If the value is yes, the device likely wasn't tampered but hasn't necessarily passed Android compatibility testing. |
| Extended Integrity | No | A stricter verdict of device integrity. If the value is yes, then the profile of the device matches the profile of a device that has passed Android compatibility testing. |
| Advisory Response | LOCK_BOOTLOADER | Provides a suggestion for how to get a device back into a good state. This Advisory Response can be empty and isn't influenced by the Management system. |
Please review the examples of what the different integrity levels cover.
| Device Status | Basic Integrity | Extended Integrity |
|---|---|---|
| Certified, genuine device that passes CTS | Yes | Yes |
| Certified device with unlocked bootloader | Yes | No |
| Genuine but uncertified device, such as when the manufacturer doesn't apply for certification | Yes | No |
| Device with custom ROM (not rooted) | Yes | No |
| Emulator | No | No |
| No device (such as a protocol emulating script) | No | No |
| Signs of system integrity compromise, one of which may be rooting | No | No |
| Signs of other active attacks, such as API hooking | No | No |
Depending on your desired security measurements for your device fleet, we've added the ability to perform lockdown actions based on the SafetyNet Attestation results. For this, we've created two the Lockdown settings for Android and Samsung devices with different non-compliance actions:
| Policy | Non-compliance Action | Description |
|---|---|---|
| Enforce Basic Integrity |
|
When the SafetyNet Attestation reports that the device does not meet the basic integrity requirements, the selected action will be triggered. |
| Enforce Extended Integrity |
|
When the SafetyNet Attestation reports that the device does not meet the extended integrity requirements, the selected action will be triggered. |
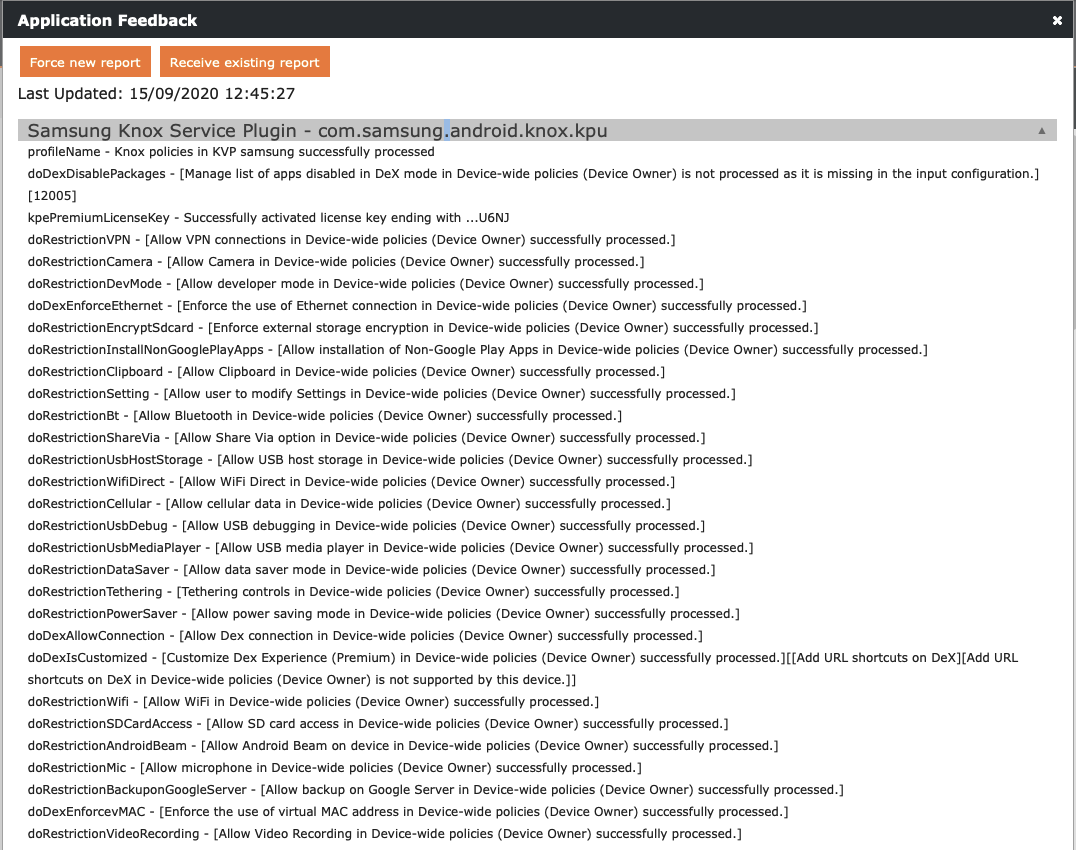
Application Feedback
For customers using Android Enterprise we are happy to introduce the App Feedback Channel. Enterprise-ready applications, like the Samsung Knox Service Plugin, are capable of sending feedback in form of a unique identifier (key), a corresponding message, the severity status and a timestamp. For this feature, the application needs to be integrated with the so-called Enterprise Jetpack library.
With Silverback 20.0 Update 2 you will find a new device action named as Application Feedback shown to Android Enterprise devices. By using the Application Feedback action, you will gain the possibility to receive feedback from installed and managed applications. As an example, after the installation of the Samsung Knox Service Plugin, the application reports the implementation of the applied configuration to your Management Console, as shown in the following screenshot. If multiple applications are on the device that can send feedbacks, you can easily expand and collapse the feedback per application in this view. If errors appear when installing a configuration for the application or in any other cases, the information will be reported to Silverback and highlighted in the Management Console with a readable message.
You can also force the device or the application to create a new report or force to receive an existing report. The last updated information displays when the Management System received the last application feedback report from the device.
Windows 10 Security and Privacy
With the last release we have already brought some new security and privacy features for macOS devices into the product. In this we focused on bringing the feature landscape to the Windows 10 device management. This includes receiving important defender information from the device fleet, control mechanism for operating system updates or the extension of BitLocker settings for device encryption and last but not least configuring the Windows Defender Firewall. Please proceed with the following chapters to get an overview of all new and valuable Windows 10 Security and Privacy features.
Defender Antivirus
The Windows Defender configuration service provider is used to configure various Windows Defender actions across the enterprise. Within the new Silverback Release, you are now capable of receiving important Defender Antivirus information like when the last scan for quick and full scanning was, what scanning signatures have been used and if they are maybe outdated. Also general information is present about the defender version and if the defender services is running at all on the client. All of the following information is available in the Device Overview for each particular Windows 10 device.
| Information | Example | Description |
|---|---|---|
| Defender version | 4.18.2007.8 | Version number of Windows Defender on the device. |
| Defender engine version | 1.1.17300.4 | Version number of the current Windows Defender engine on the device. |
| Defender signature version | 1.321.98.0 | Version number of the current Windows Defender signatures on the device. |
| Defender service is running | Yes | Indicates whether the Windows Defender service is running. |
| Signature is outdated | No | Indicates whether the Windows Defender signature is outdated. |
| Current state of the product | No status flags set |
Shows the current state of the product. It can contain one or multiple values from this list:
Requires Windows 10 Version 1809 |
| Current state of the device | Clean |
Displays the current state of the device like:
|
| Full scan is required | No | Indicates whether a Windows Defender full scan is required. |
| Last full scan | 07/24/2020 16:09:37 UTC | Time of the last Windows Defender full scan of the device. |
| Last full scan signature version | 1.319.2181.0 | Signature version used for the last full scan of the device. |
| Full scan is overdue for the device | No |
Indicates whether a Windows Defender full scan is overdue for the device. A Full scan is overdue when a scheduled Full scan did not complete successfully for 2 weeks and catch up Full scans are disabled (default). Review Windows 10 Restrictions for catch-up controls |
| Last quick scan | 07/29/2020 02:08:16 UTC | Time of the last Windows Defender quick scan of the device. |
| Last quick scan signature version | 1.321.74.0 | Signature version used for the last quick scan of the device. |
| Quick scan is overdue for the device | No |
Indicates whether a Windows Defender quick scan is overdue for the device. A Quick scan is overdue when a scheduled Quick scan did not complete successfully for 2 weeks and catch up Quick scans are disabled (default). Review Windows 10 Restrictions for catch-up controls |
| Real-time protection is running | Yes | Indicates whether real-time protection is running |
| Network protection is running | Yes | Indicates whether network protection is running |
| Tamper protection feature is enabled | No | Indicates whether the Windows Defender tamper protection feature is enabled. Requires Windows 10 Server 1903 |
| Device reboot is needed | No | Indicates whether a device reboot is needed. |
| Is a virtual machine | Yes | Indicates whether the device is a virtual machine. Requires Windows 10 Version 1903 |
Additional we've added two new device actions for Windows 10 devices:
| Action | Description |
|---|---|
| Defender Signature Update | Performs signature updates for Windows Defender. |
| Defender Offline Scan | Added in Windows 10, version 1803. Starts a Microsoft Defender Offline scan on the computer where you run the command. After the next OS reboot, the device will start in Microsoft Defender Offline mode to begin the scan. |
Defender Firewall
The Firewall configuration allows to control the Windows Defender Firewall global settings, per profile settings, as well as the desired set of custom rules to be enforced on the device. You can now manage non-domain devices, and reduce the risk of network security threats across all systems connecting to the corporate network. The Firewall configuration is supported beginning with Windows 10, version 1709.
| Settings | Options | Description |
|---|---|---|
| Defender Firewall Settings | Enabled or Disabled | Enables the Defender Firewall Profile |
| Global Settings | ||
| Security Association Idle Time Before Deletion (in secs) |
e.g. 400 |
Security associations are deleted after network traffic is not seen for this number of seconds. Supported Values from 300 to 3600 |
| Pre-shared Key Encoding |
|
Specifies the preshared key encoding that is used |
| IPsec Exemptions |
|
Configure specific traffic to be exempt from performing IPsec. |
| Certificate Revocation List Verification |
|
Defines how certificate revocation list verification is enforced. The following options are available:
|
| Packet Queuing |
|
Specifies how scaling for the software on the receive side is enabled for both the encrypted receive and clear text forward path for the IPsec tunnel gateway scenario. Use of this option also ensures that the packet order is preserved. |
| File Transfer Protocol | Enabled or Disabled | |
| Opportunistically Match Authentication Set Per Keying Module | Enabled or Disabled | If enabled, keying modules will ignore unsupported authentication suites. |
| Network Settings (applies to Domain, Private, or Public Network) | ||
| Microsoft Defender Firewall | Enabled or Disabled | If this setting is not enabled, no network traffic will be blocked regardless of other policy settings |
| Disable Stealth Mode | Enabled or Disabled | When this option is false, the server operates in stealth mode. The firewall rules used to enforce stealth mode are implementation-specific |
| IPsec Secured Packet Exemption With Stealth Mode | Enabled or Disabled | If stealth mode is enabled, this option will be ignored. Otherwise the stealth mode rules must not prevent the host computer from responding to unsolicited network traffic if that traffic is secured by IPsec |
| Shielded | Enabled or Disabled | If this value is true and Defender Firewall is on, the server must block all incoming traffic regardless of other policy settings |
| Disable Unicast Responses to Multicast Broadcasts | Enabled or Disabled | If true, unicast responses to multicast broadcast traffic is blocked. |
| Inbound Notifications | Enabled or Disabled | If false, the Firewall may display a notification to the user when an application is blocked from listening on a port. If this setting is enabled, the Firewall must not display such notifications. |
| Default Action For Outbound Connections |
|
This value is the action that the firewall does by default (and evaluates at the very end) on outbound connections. |
| Default Action for Inbound Connections |
|
This value is the action that the firewall does by default (and evaluates at the very end) on inbound connections. |
| Auth App Firewall Rules From the Local Store | Enabled or Disabled | If this value is false, authorized application firewall rules in the local store are ignored and not enforced |
| Global Port Firewall Rules From the Local Store | Enabled or Disabled | If this value is false, global port firewall rules in the local store are ignored and not enforced |
| Firewall Rules From the Local Store | Enabled or Disabled | If this value is false, firewall rules from the local store are ignored and not enforced |
| IPsec Rules From the Local Store | Enabled or Disabled | If this value is false, connection security rules from the local store are ignored and not enforced, regardless of the schema version and security rule version |
Windows Update Controls
For Windows 10, Administrators will get the control over OS Updates through the Mobile Device Management Layer. Microsoft presents the Update Policy CSP for that. With this integration you will gain control over how and when updates will be installed and which servicing channel will be used.
| Setting | Options | Description |
|---|---|---|
| Windows Update Policy Settings | Enabled or Disabled | Enables the Windows Update Settings. |
|
|
|
Notify the user before downloading the update. This policy is used by the enterprise who wants to enable the end-users to manage data usage. With this option users are notified when there are updates that apply to the device and are ready for download. Users can download and install the updates from the Windows Update control panel. Auto install the update and then notify the user to schedule a device restart. Updates are downloaded automatically on non-metered networks and installed during "Automatic Maintenance" when the device is not in use and is not running on battery power. If automatic maintenance is unable to install updates for two days, Windows Update will install updates immediately. If the installation requires a restart, the end-user is prompted to schedule the restart time. The end-user has up to seven days to schedule the restart and after that, a restart of the device is forced. Enabling the end-user to control the start time reduces the risk of accidental data loss caused by applications that do not shutdown properly on restart. Auto install and restart. Updates are downloaded automatically on non-metered networks and installed during "Automatic Maintenance" when the device is not in use and is not running on battery power. If automatic maintenance is unable to install updates for two days, Windows Update will install updates right away. If a restart is required, then the device is automatically restarted when the device is not actively being used. This is the default behavior for unmanaged devices. Devices are updated quickly, but it increases the risk of accidental data loss caused by an application that does not shutdown properly on restart. Auto install and restart at a specified time. Specify the installation day and time. If no day and time are specified, the default is 3 AM daily. Automatic installation happens at this time and device restart happens after a 15-minute countdown. If the user is logged in when Windows is ready to restart, the user can interrupt the 15-minute countdown to delay the restart. Auto install and restart without end-user control. Updates are downloaded automatically on non-metered networks and installed during "Automatic Maintenance" when the device is not in use and is not running on battery power. If automatic maintenance is unable to install updates for two days, Windows Update will install updates right away. If a restart is required, then the device is automatically restarted when the device is not actively being used. This setting option also sets the end-user control panel to read-only. Turn off automatic updates. |
|
|
|
Allows to set which branch a device receives their updates from. Requires Windows 10 Version 1607. |
|
|
e.g. 15 | Defers Quality Updates for the specified number of days. Supported Values are 0-365. Requires Windows 10 Version 1607. |
|
|
e.g. 90 | Defers Feature Updates for the specified number of days. Supported Values are 0-365. Requires Windows 10 Version 1703. |
|
|
2-60 days | Enables to configure feature update uninstall period. Values range 2 - 60 days. Default is 10 days. Requires Windows 10 Version 1803. |
|
|
|
Option to schedule the day of the update installation. |
|
|
e.g. 08 AM |
Allows, when used with Active Hours End to manage a range of hours where update reboots are not scheduled. This value sets the start time. There is a 12 hour maximum from end time. Requires Windows 10 Version 1607. The default maximum difference from end time has been increased to 18 in Windows 10, version 1703. In this version of Windows 10, the maximum range of active hours can now be configured. Please refer to Active Hours Max Range |
|
|
e.g. 05 PM | Added in Windows 10, version 1607. Allows, when used with Active Hours Start to manage a range of active hours where update reboots are not scheduled. This value sets the end time. There is a 12 hour maximum from start time. Requires Windows 10 Version 1607. |
|
|
e.g. 12 |
Allows to specify the period for auto-restart warning reminder notifications. Supported values are 2, 4, 8, 12, or 24 (hours). The default value is 4 (hours). Requires Windows 10 Version 1703. |
|
|
e.g. 60 |
Allows to specify the period for auto-restart imminent warning notifications. The default value is 15 (minutes). Supported values are 15, 30, or 60 (minutes). Requires Windows 10 Version 1703. |
|
|
|
Display options for update notifications. This policy allows to define what Windows Update notifications users see. This policy doesn't control how and when updates are downloaded and installed. |
|
|
e.g. 90 |
Allows to specify the number of days a user has before feature updates are installed on their devices automatically. Updates and restarts will occur regardless of active hours and the user will not be able to reschedule. Supported Values are 2 - 30 (Default = 7), which indicates the number of days a device will wait until performing an aggressive installation of a required feature update. Requires Windows 10 Version 1903. |
|
|
e.g. 5 |
Allows to specify the number of days a user has before quality updates are installed on their devices automatically. Updates and restarts will occur regardless of active hours and the user will not be able to reschedule. Supports values from 2 - 30 (Default =7), which indicates the number of days a device will wait until performing an aggressive installation of a required quality update. Requires Windows 10 Version 1903. |
|
|
e.g. 1 |
Allows, when used with Deadline for feature updates or Deadline for quality updates to specify a minimum number of days until restarts occur automatically. Setting the grace period may extend the effective deadline set by the deadline policies. Supports a numeric value from 0 - 7 (Default =2), which indicates the minimum number of days a device will wait until performing an aggressive installation of a required update once the deadline has been reached. Requires Windows 10 Version 1903. |
|
|
Enabled or Disabled |
Option to download updates automatically over metered connections (off by default). A significant number of devices primarily use cellular data and do not have Wi-Fi access, which leads to a lower number of devices getting updates. Since a large number of devices have large data plans or unlimited data, this policy can unblock devices from getting updates. This policy is accessible through the Update setting in the user interface or Group Policy. Requires Windows 10 Version 1709. |
|
|
Enabled or Disabled |
Allows to exclude Windows Update (WU) drivers during updates. Requires Windows 10 Version 1607. |
| Enabled or Disabled |
If enabled and when used with Deadline for feature or quality updates, devices will not automatically restart outside of active hours until the deadline is reached, even if applicable updates are already installed and pending a restart. When disabled, if the device has installed the required updates and is outside of active hours, it may attempt an automatic restart before the deadline. Requires Windows 10 Version 1903. |
|
| Target release version | e.g. 1903 |
Allows to specify which version devices should be migrated to and/or which version they should keep until they reach the end of service or the policy is reconfigured. Requires Windows 10 Version 1803 |
| Update service url | e.g. http://wsus.imagoverum.com:8530 | Allows the device to check for updates from a WSUS server instead of Microsoft Update. This is useful for on-premises MDMs that need to update devices that cannot connect to the Internet. |
| Update service url alternate | e.g. http://alternate.imagoverum.com:8530 |
Specifies an alternate intranet server to host updates from Microsoft Update. You can then use this update service to automatically update computers on your network. Requires Windows 10 Version 1607 |
| Allow non-Microsoft signed updates | Enabled or Disabled | This policy is specific to desktop and local publishing via WSUS for 3rd party updates (binaries and updates not hosted on Microsoft Update) and allows to manage whether Automatic Updates accepts updates signed by entities other than Microsoft when the update is found on an intranet Microsoft update service location |
| Disable dual scan | Enabled or Disabled | Do not allow update deferral policies to cause scans against Windows Update. If this policy is not enabled, then configuring deferral policies will result in the client unexpectedly scanning Windows update. With the policy enabled, those scans are prevented, and users can configure deferral policies as much as they like. |
| Allow MU update service | Enabled or Disabled | Allows to manage whether to scan for app updates from Microsoft Update. |
| Update Power Policy for Cart Restarts | Enabled or Disabled |
For devices in a cart, this policy skips all restart checks to ensure that the reboot will happen at Scheduled Install Time When you set this policy along with Active hours start, Active hours end and ShareCartPC, it will defer all the update processes (scan, download, install, and reboot) to a time after Active Hours. After a buffer period after Active hours end, the device will wake up several times to complete the processes. All processes are blocked before Active hours start. Requires Windows 10 Version 1703 |
Extended BitLocker Controls
The BitLocker configuration service provider is used by the enterprise to manage encryption of PCs and devices. We already have the capability to force the bitlocker encryption for Windows 10 devices since a long time in the product, but with this Release we enriched the capabilities for Administrators to the extended feature set. This includes as an example to configure the encryption methods used for the system drive and/or data or removable data drives. Another benefit is that you can now force additional authentication settings when the machine is booting.
| Setting | Options | Description |
|---|---|---|
| BitLocker Settings | Enabled or Disabled | Enables the BitLocker Settings. |
| BitLocker base settings | ||
| Enabled or Disabled | Allows to require encryption to be turned on by using BitLocker. | |
| Enabled or Disabled | Allows to disable the warning prompt for other disk encryption on the user machines. Starting in Windows 10, version 1803, the setting can only be disabled for Azure Active Directory joined devices.
When you disable the warning prompt, the OS drive's recovery key will back up to the user's Azure Active Directory account. When you allow the warning prompt, the user who receives the prompt can select where to back up the OS drive's recovery key. The endpoint for a fixed data drive's backup is chosen in the following order:
Encryption will wait until one of these three locations backs up successfully. |
|
| Enabled or Disabled | Allows users without Administrative rights to enable BitLocker encryption on the device. This setting applies to Azure Active Directory Joined devices. | |
|
Allows to set the default encryption method for each of the different drive types: operating system drives, fixed data drives, and removable data drives. Hidden, system, and recovery partitions are skipped from encryption. If you disable or do not configure this policy setting, BitLocker will use the default encryption method of XTS-AES 128-bit or the encryption method specified by any setup script. | |
|
This setting allows you to configure the algorithm and cipher strength used by BitLocker Drive Encryption. This setting is applied when you turn on BitLocker. Changing the encryption method has no effect if the drive is already encrypted, or if encryption is in progress. | |
|
This setting allows you to configure the algorithm and cipher strength used by BitLocker Drive Encryption. This setting is applied when you turn on BitLocker. Changing the encryption method has no effect if the drive is already encrypted, or if encryption is in progress. | |
|
This setting allows you to configure the algorithm and cipher strength used by BitLocker Drive Encryption. This setting is applied when you turn on BitLocker. Changing the encryption method has no effect if the drive is already encrypted, or if encryption is in progress. | |
| BitLocker OS drive settings | ||
|
This setting allows you to configure whether BitLocker requires additional authentication each time the computer starts and whether you are using BitLocker with or without a TPM. This setting is applied when you turn on BitLocker. | |
| Enabled or Disabled | Block the use of BitLocker on computers without a compatible Trusted Platform Module. Requires a password for a startup key on a USB flash drive. | |
|
Configure if TPM is allowed, required or not allowed for startup | |
|
Configure if a TPM startup key is allowed, required or not allowed for startup | |
|
Configure if a TPM startup PIN is allowed, required or not allowed for startup | |
|
Configure if a TPM Startup key and PIN is allowed, required or not allowed for startup. | |
|
This setting allows you to configure a minimum length for a Trusted Platform Module (TPM) startup PIN. This setting is applied when you turn on BitLocker. | |
| e.g. 20 | The startup PIN must have a minimum length of 6 digits and can have a maximum length of 20 digits. | |
|
This setting allows to control how BitLocker-protected operating system drives are recovered in the absence of the required startup key information. This setting is applied when turning on BitLocker. | |
| Enabled or Disabled | Specify whether a data recovery agent can be used with BitLocker-protected operating system drives. Before a data recovery agent can be used it must be added from the Public Key Policies item in either the Group Policy Management Console or the Local Group Policy Editor. Consult the BitLocker Drive Encryption Deployment Guide on Microsoft TechNet for more information about adding data recovery agents. | |
|
Set whether users are allowed, required, or not allowed to generate a 48-digit recovery password | |
|
Set whether users are allowed, required, or not allowed to generate a 256-bit recovery key. | |
| Enabled or Disabled | Prevent users from specifying recovery options when they turn on BitLocker on a drive. This means that a user will not be able to specify which recovery option to use when turning on BitLocker. Instead, BitLocker recovery options for the drive are determined by the policy. | |
| Enabled or Disabled | Enable BitLocker recovery information to be stored in AD DS | |
|
Choose which BitLocker recovery information to store in AD DS for fixed data drives. If Backup recovery password and key package selected, both the BitLocker recovery password and key package are stored in AD DS. Storing the key package supports recovering data from a drive that has been physically corrupted. If Backup recovery password only selected only the recovery password is stored in AD DS. | |
| Enabled or Disabled | Prevent users from enabling BitLocker unless the computer is connected to the domain and the backup of BitLocker recovery information to AD DS succeeds. In this case a recovery password is automatically generated. | |
|
This setting allows to configure the entire recovery message or replace the existing URL that is displayed on the pre-boot key recovery screen when the OS drive is locked. | |
|
Use default recovery message and URL: The default BitLocker recovery message and URL will be displayed in the pre-boot key recovery screen. If you have previously configured a custom recovery message or URL and want to revert to the default message, you must keep the policy enabled and set the value "to Use default recovery message and URL. Use custom recovery message. The message you set will be displayed in the pre-boot key recovery screen. If a recovery URL is available, include it in the message. Use custom recovery URL: The URL you type in will replace the default URL in the default recovery message, which will be displayed in the pre-boot key recovery screen. |
|
| BitLocker fixed data-drive settings | ||
|
This setting determines whether BitLocker protection is required for fixed data drives to be writable on a computer. If this setting is enabled, all fixed data drives that are not BitLocker-protected will be mounted as read-only. If the drive is protected by BitLocker, it will be mounted with read and write access. |
|
|
This setting allows to control how BitLocker-protected fixed data drives are recovered in the absence of the required credentials. This setting is applied when turning on BitLocker. | |
| Enabled or Disabled | Specify whether a data recovery agent can be used with BitLocker-protected fixed data drives. Before a data recovery agent can be used it must be added from the Public Key Policies item in either the Group Policy Management Console or the Local Group Policy Editor. Consult the BitLocker Drive Encryption Deployment Guide on Microsoft TechNet for more information about adding data recovery agents. | |
|
Set whether users are allowed, required, or not allowed to generate a 48-digit recovery password | |
|
Set whether users are allowed, required, or not allowed to generate a 256-bit recovery key. | |
| Enabled or Disabled | Prevent users from specifying recovery options when they turn on BitLocker on a drive. This means that a user will not be able to specify which recovery option to use when turning on BitLocker. Instead, BitLocker recovery options for the drive are determined by the policy. | |
|
Choose which BitLocker recovery information to store in AD DS for fixed data drives. If the Backup recovery password and key package are selected, both the BitLocker recovery password and key package are stored in AD DS. Storing the key package supports recovering data from a drive that has been physically corrupted. If Backup recovery password only is selected, only the recovery password is stored in AD DS. | |
| Enabled or Disabled | Prevent users from enabling BitLocker unless the computer successfully backs up the BitLocker recovery information to Azure Active Directory. Selecting Enanled will ensure the recovery keys are successfully stored in Azure Active Directory before enabling encryption. By selecting disabled, a device may become encrypted without recovery information stored in Azure Active Directory | |
| BitLocker removable data-drive settings | ||
|
Determine whether BitLocker protection is required for removable data-drives to be writable on a computer | |
| Enabled or Disabled | Determine if removable data-drives configured by an external organization can be written to | |
macOS
With this release of Silverback 20.0 Update 2 we enhanced the capabilities for Administrators to configure specific app controls through the Management Console. From now on it is possible to provide to Enterprise applications a specific XML formatted configuration file like on iOS and iPadOS applications. This feature is well known for iOS and iPadOS application management and we are happy to bring the same capabilities to macOS. Navigate to the App Portal, select your managed applications and click the Edit button next to App Config. Afterwards ensure to provide a proper xml configuration according to the application developer guidelines.
Managed Application Configuration
We are offering two ways of configuring the application. If you add the configuration in the App Portal section (1), this will be used every time as default when you add the application into a Tag. However you can at every time adjust and overrule the configuration inside the Tag with the edit button (2). The documentation about the App Configuration XML should be part of the applications developer, so please get in touch to receive information about the configuration options for your desired application. With the following example the Incognito Mode for Google Chrome will be deactivated.
After configuration you can review your configuration on the device under Settings > Profiles > Silverback Managed Preferences
By default the target folder for configurations is Library > Managed Preferences
 |
 |
| Global configuration for Chrome with allowed Incognito Mode | Tag based configuration with disallowed Incognito Mode |
 |
 |
Defer Updates
If you are managing supervised iOS and iPadOS devices then you might be already familiar with the feature to postpone OS Updates. With this new Silverback Version, Administrators will gain the possibility to defer operating system updates up to 90 days as well for macOS devices.
When creating the OS Updates policy ensure that Profile is enabled under the Tag definition.

Improvements
- Application names, descriptions and family types for Volume Purchase Program application will be now updated automatically
- Added Managed Configuration iFrame hierarchies view (e.g. for Samsung Knox Service Plugin)
- Deprecated macOS Restrictions has been remove (Allow Add to iPhoto, Allow Add to Reading List, Automatically enable new shared services)
- Removed HTTP-Header information
- Added all public release from Windows 10 (1803, 1809, 1903, 1909, 2004) to OS Version Compliance
- Removed "null" version for Microsoft Business Application in assign application window
- Changed ordering of settings for App Management section for Enterprise applications and aligned checkboxes
- Added tooltip to Edit managed configuration for Android Enterprise applications
- Removed Feedback Assistant application from enforced blacklist section
- Merged Bitlocker controls from Restrictions and Profiles
- Defender Antivirus controls are now a separated profile
- Passcode Settings for Windows 10 have been adjusted and merged with Device Lock Restrictions
- After activating Lost Mode, a Device Information command will be send instantly to retrieve status
- Added Service Bus connection to encrypted collection
- Replaced Companion Push Notification Service for iOS & iPadOS
- Updated to Service Bus Adapter version 3.1.0