Release Notes Silverback 23.0 Update 1
About This Release
Matrix42 Silverback 23.0 Update 1 provides new and improved features that have been implemented. During the development of this version, we have been focusing on valued feedback from our customers and partners to provide an ideal feature selection.
Important Announcements
Update Information
If you are upgrading from a version older than Silverback 23.0, please note the new system requirements (new version of the .NET Core Hosting Bundle) for Apple devices introduced with Silverback 23.0.
Deprecations
The following feature or settings deprecations will take place with Silverback 23.0 Update 2 and newer:
Matrix42 Mobile
The Matrix42 Mobile application has been set to End of Life on 12 May 2023 and has been removed from sale in the Apple and Google App Stores. Existing installations of the application will remain on the devices, but new installations will no longer be possible. As the Matrix42 Mobile App included several features that also affect Mobile Content Management with Silverback, we would like to advise you to switch to Matrix42 Documents and provide your users the Mobile Content Management features with Silversync. The discontinuation in this case also affects the provision of content providers Box, Dropbox, ownCloud, as these are not supported in Matrix42 Documents and we will gradually remove the configuration options in Silverback related to the Matrix42 Mobile application from the Management Console.
Matrix42 Companion distribution as enterprise application for iOS/iPadOS
Historically, you can find the option to deploy the Matrix42 Companion for iPhone, iPad and iPod as an Enterprise App in the Silverback Management Console's Admin section under Companion. This option will be disabled in future Silverback releases. You can still deploy and configure the Matrix42 Companion application in the usual way using the policy settings in its tags.
App Store Apps for Android and Samsung Knox devices
As we continue to evolve our product and the market in the direction of Android Enterprise, we will be discontinuing a feature that was introduced in the pre-Android Enterprise timeframe. In the pre-Android Enterprise/Legacy Management era, you as an administrator could give your users access to Google Play applications via the App Portal (WebClip) installed on the device. The display in the App Portal was simply a link that would open the Google Play Store and the user could then install the application using their Google account. In the era of Managed Google Play on Android Enterprise, this feature is no longer state of the art, so in a future release we will disable the option to create new App Store applications in the App Portal for Android and Samsung Knox. Enterprise applications can still be viewed in the App Portal as usual, and Managed Play applications will still be visible and installable from the Managed Play Store.
Samsung ELM and Knox License support for Samsung Knox Devices
Samsung made the switch from ELM keys to KPE keys some time ago to take advantage of the capabilities of Samsung Knox Platform for Enterprise (KPE), and we made the switch for you in the background some time ago. In addition, you can currently find a Knox license in the Web Settings in Android, which was previously used to activate the Workspace Container on Samsung Knox. This feature has also been replaced by the standard Android Enterprise Work Profiles for some time now, so we will be disabling both fields. We recommend that customers who have entered a Samsung Knox license in the past remove the license manually.
Additional Web Settings Deprecations
In the Android section of the Web Settings, you will find options for Google Play settings that are also from the Android Legacy Management or pre-Android Enterprise era and are no longer relevant. For this reason, we will disable this information in a future release. This also applies to WP settings in the Windows section as they relate to Windows 10 Mobile devices.
Overview
New Features
Android Enterprise
iOS, iPadOS, macOS
New Improvements
Known Issues
New Features
Android Enterprise
In this release, we focused on enhancing the enrollment and user experience for Android Enterprise. This has resulted several different features that cover the device enrollment, and building or releasing applications to your users.
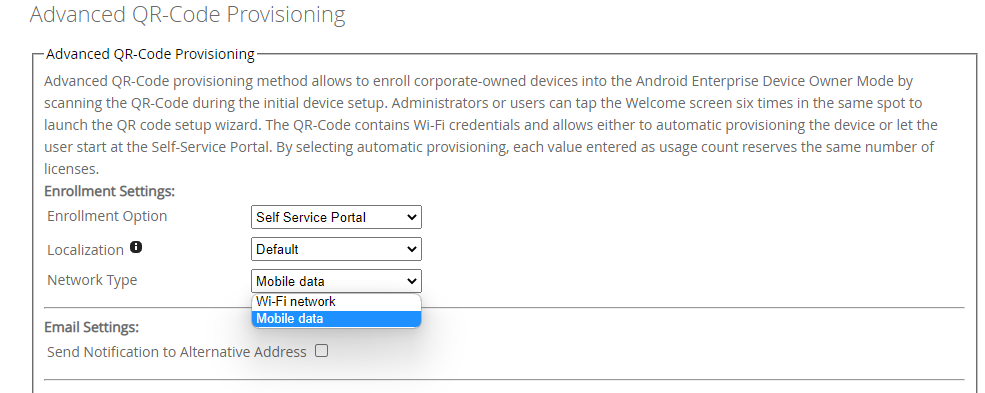
Advanced QR-Code with Mobile Data
The first feature that we want to introduce is the usage of mobile data while enrolling devices with the Advanced QR-Code provisioning. The Advanced QR-Code provisioning allows to enroll corporate-owned devices into the Android Enterprise Device Owner Mode by scanning the QR-Code during the initial device setup. In general, Administrators or users can tap the Welcome screen six times in the same spot to launch the QR code setup wizard. By scanning the QR-Code it allows either to automatic provisioning the device or let the user start at the Self-Service Portal. In the past, it was required to add Wi-Fi credentials to the QR-Code, but with this new Silverback release, a new option is added to use the Mobile data to enroll quick and easy devices that are equipped with a physical or electronic SIM card.
Enable and Disable System Apps
After enrolling devices, many administrators are faced with the question of which apps should and must be available for different use cases. Android distinguishes between system apps and non-system apps, which can be defined by the manufacturer. In the past, we used the Companion application to maintain a custom list of which apps would be enabled by default after the enrollment in to Android Enterprise (Device Owner or Work Profile). This often leads to scenarios where we need to extend the list for different manufacturers based on customer feedback. Based on this experience, we have decided to move in the direction of allowing you, as an administrator, to decide whether you want to leave system applications enabled by default after enrollment, or whether you want to leave the manufacturer-defined system applications disabled and then distribute required apps either as an Enterprise application or as a Managed Play application.
As a result, you now have the option in Silverback to configure the Enable System Applications setting for the Managed Account and Work Profile to either enable or disable system applications when the device is first enrolled. The two screenshots below this text illustrate the differences between the two device owner enrollment variants. In the left screenshot, the device has been enrolled with system applications disabled, so only a minimum number of applications are active after the enrollment. With system applications enabled, more applications are available after the enrollment. Please note that changing this setting will not affect devices that have already been enrolled.
We identified an issue when the setting is changed in the original release version, that the managed account is re-provisioned and consequently all provisioned managed play apps are reinstalled and the issue is fixed with Hotfix 23.0.1.26.
| Device Owner Enrollment with disabled System Apps option | Device Owner Enrollment with enabled System Apps option |
 |
 |
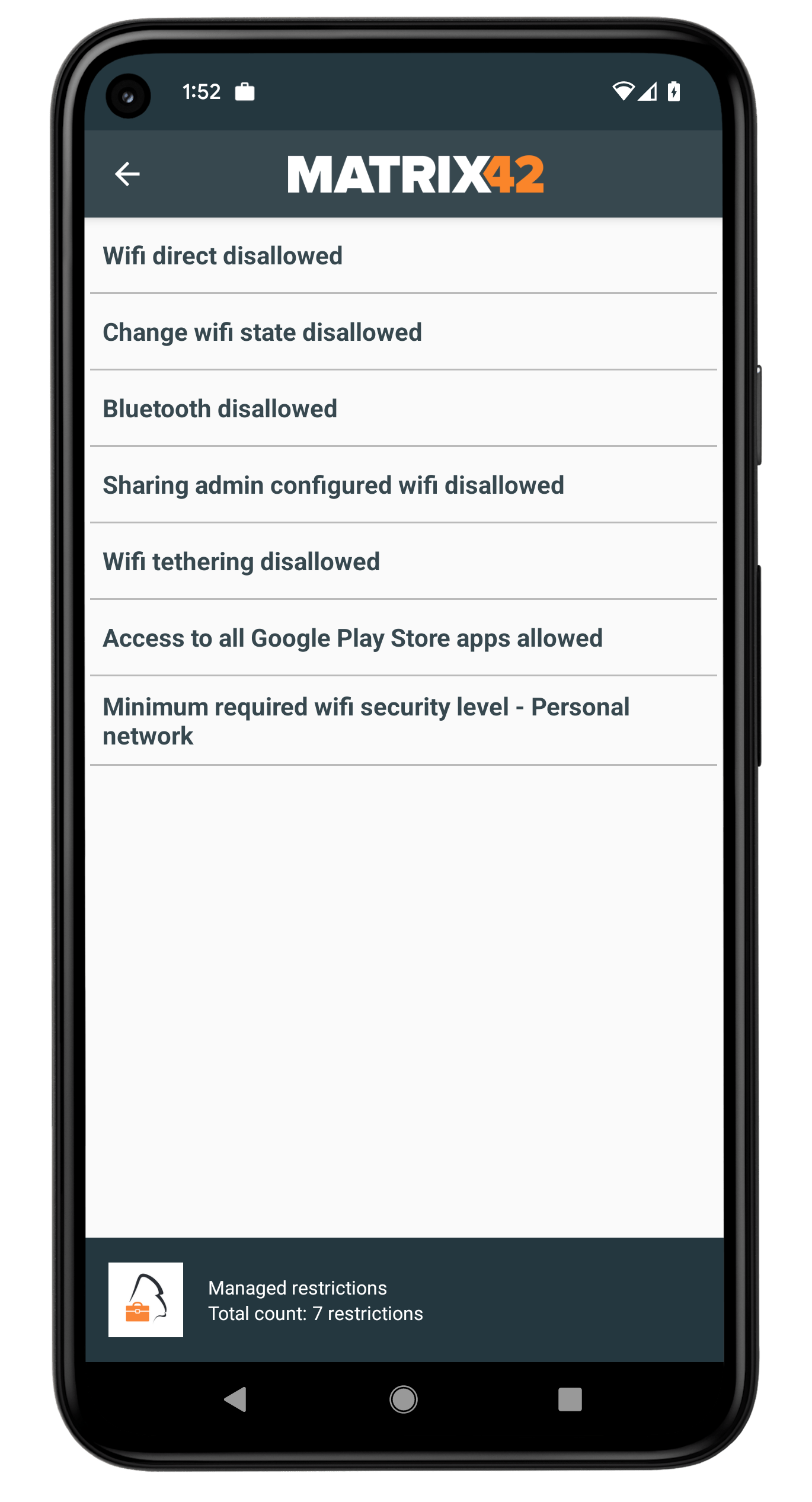
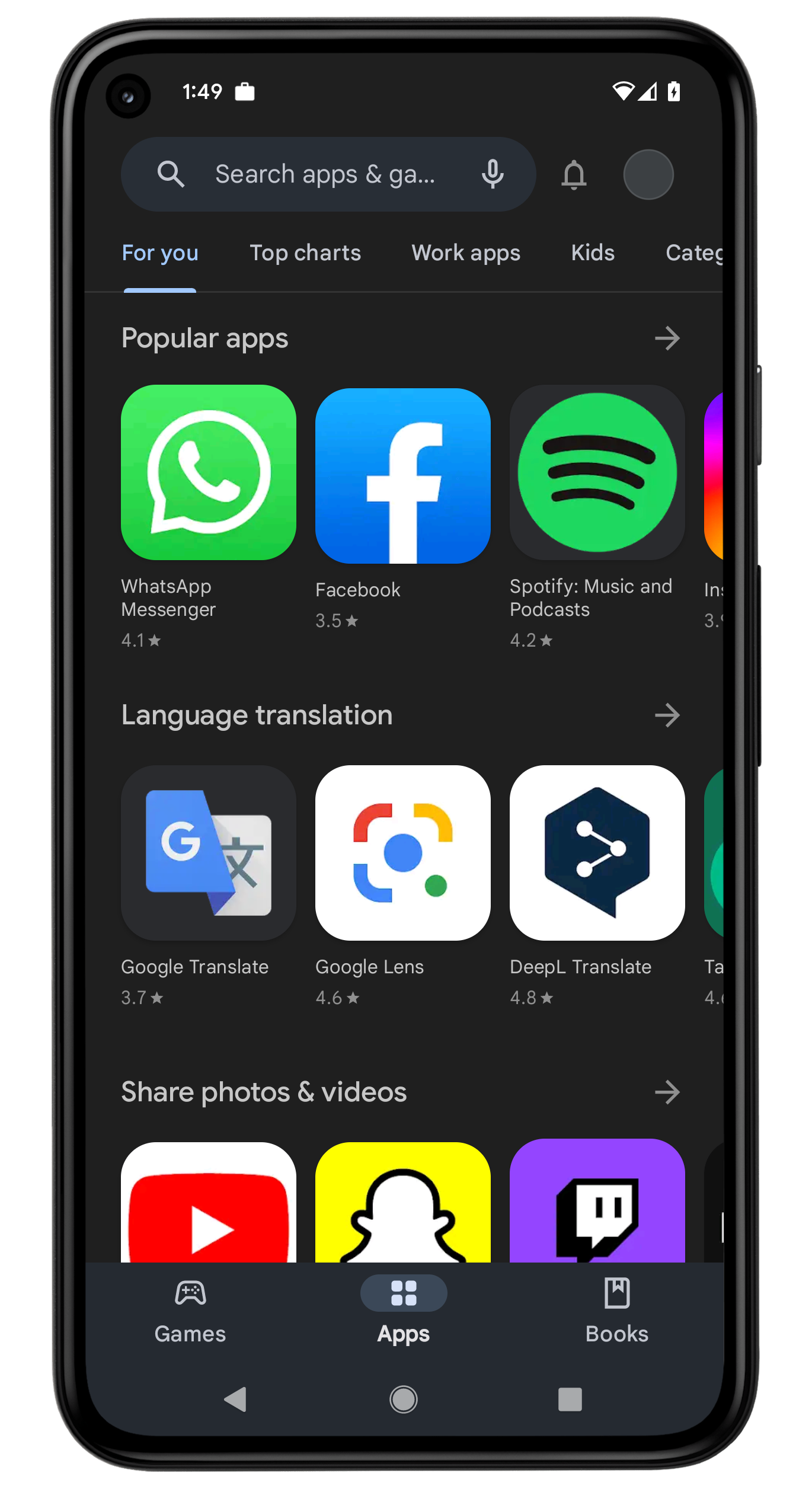
Allow access to Google Play Apps
Based on the valuable feedback from our customers, we are pleased to deliver another feature, which was also the most voted for feature in our Ideas Portal. Previously, applications could only be unlocked for users in Google Play if they were distributed as a Managed Play application via Silverback. Based on the feedback we received, some people wanted the ability to make the entire Google Play Store available and usable to users. To that end, there is now a new setting in the Restrictions profile under Applications called Allow Access to All Apps in Google Play Store, which makes the entire Google Play Store available to users. Applications can be installed without adding a personal Google account, and a new Work Apps tab in the Google Play Store will be created for applications assigned via Silverback. In principle, assigning and installing applications with the restriction enabled works as usual, except that the entire Play Store is also unlocked.
The screenshots below show Google Play with this setting disabled. If you enable the setting as an administrator and allow all apps, this will be shown in the Companion and the entire Google Play will be freely accessible and your assigned apps will be in the Work apps area.
 |
 |
 |
 |
| By default, the Access to All Apps in Google Play is disabled. | After enabling the option, an entry in Companion shows the setting to your users. | And the Google Play Store is fully accessible by your users. | Assigned Managed Play apps via Silverback are located in the Work Apps section. |
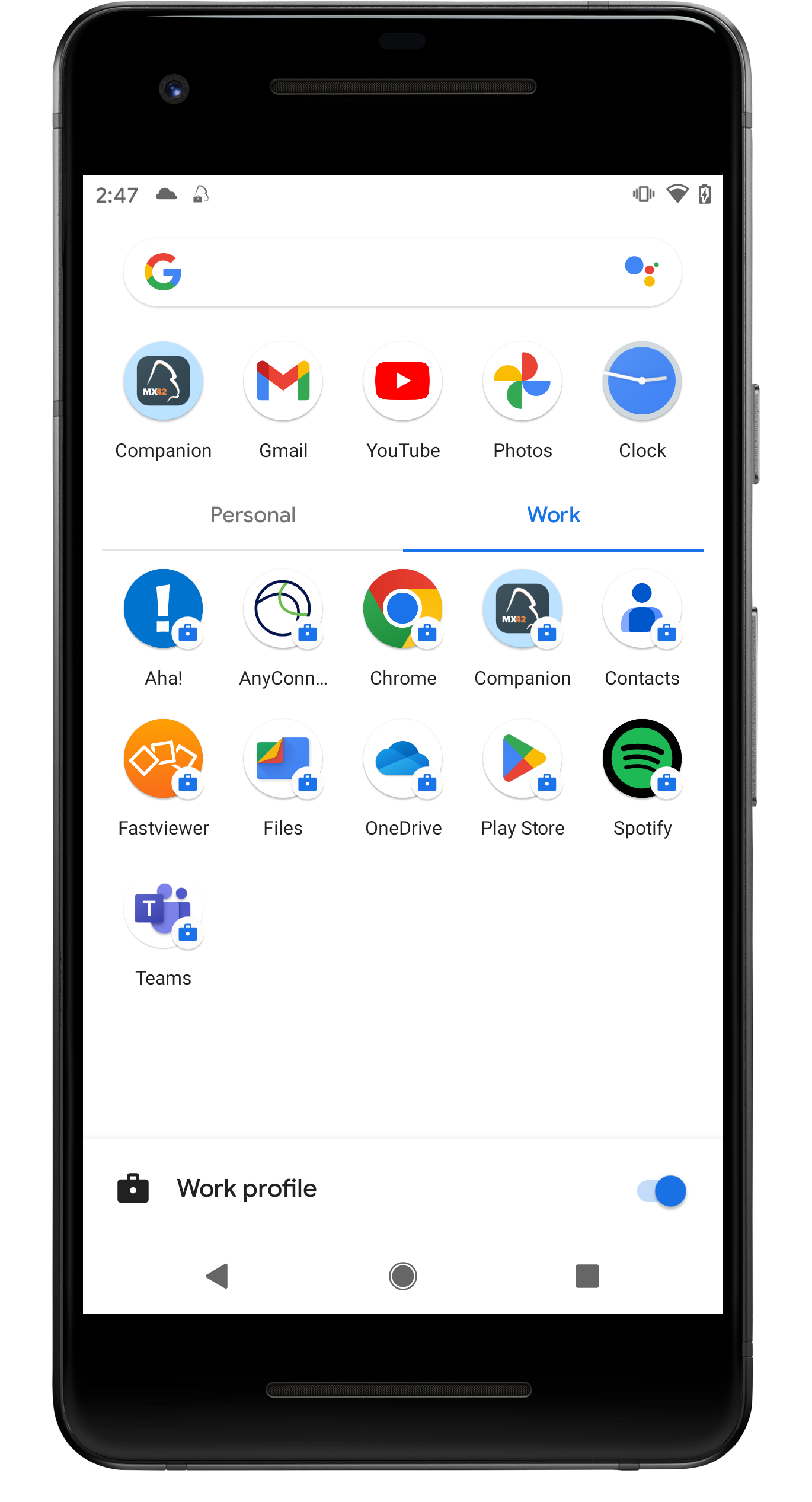
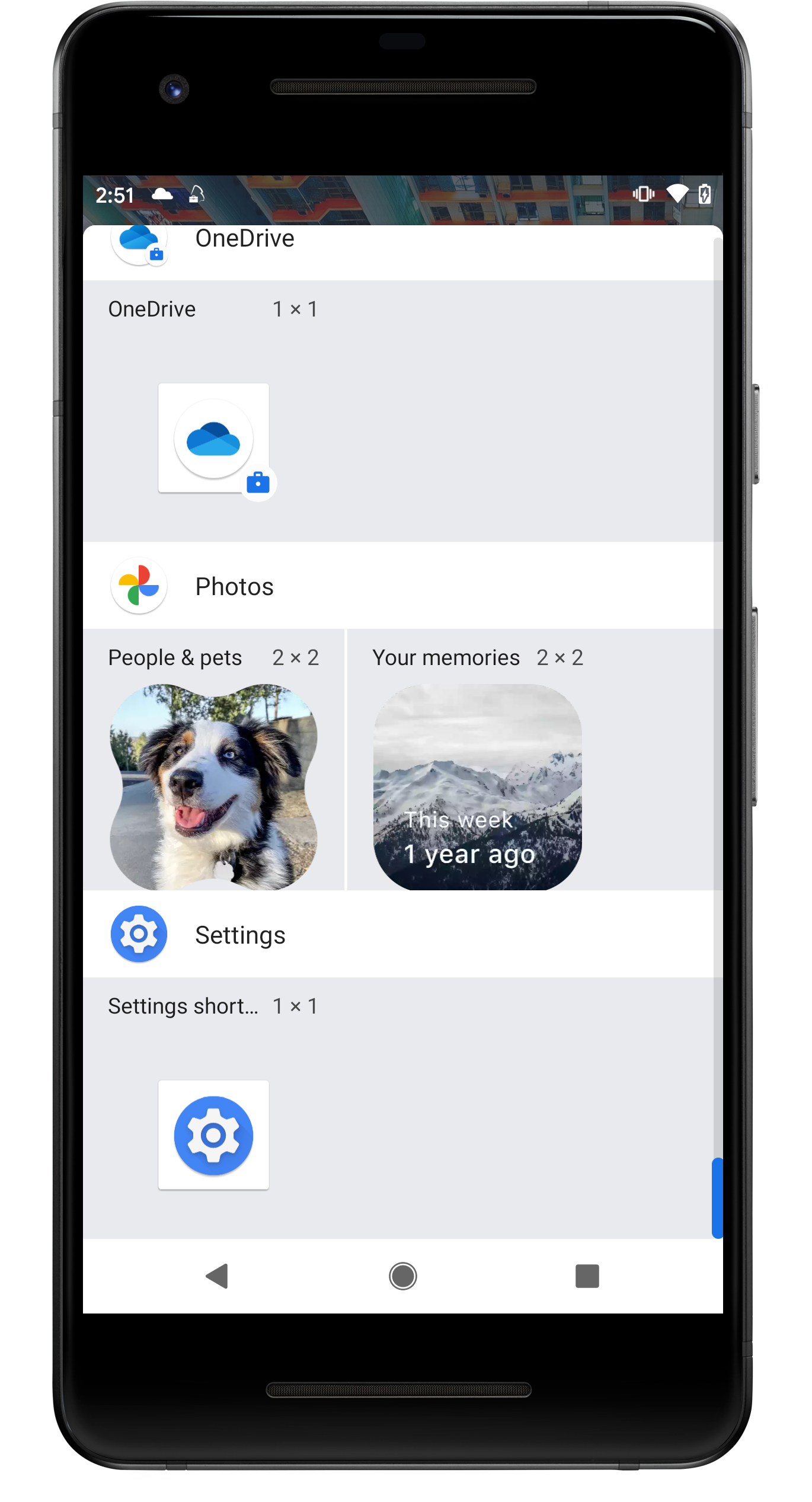
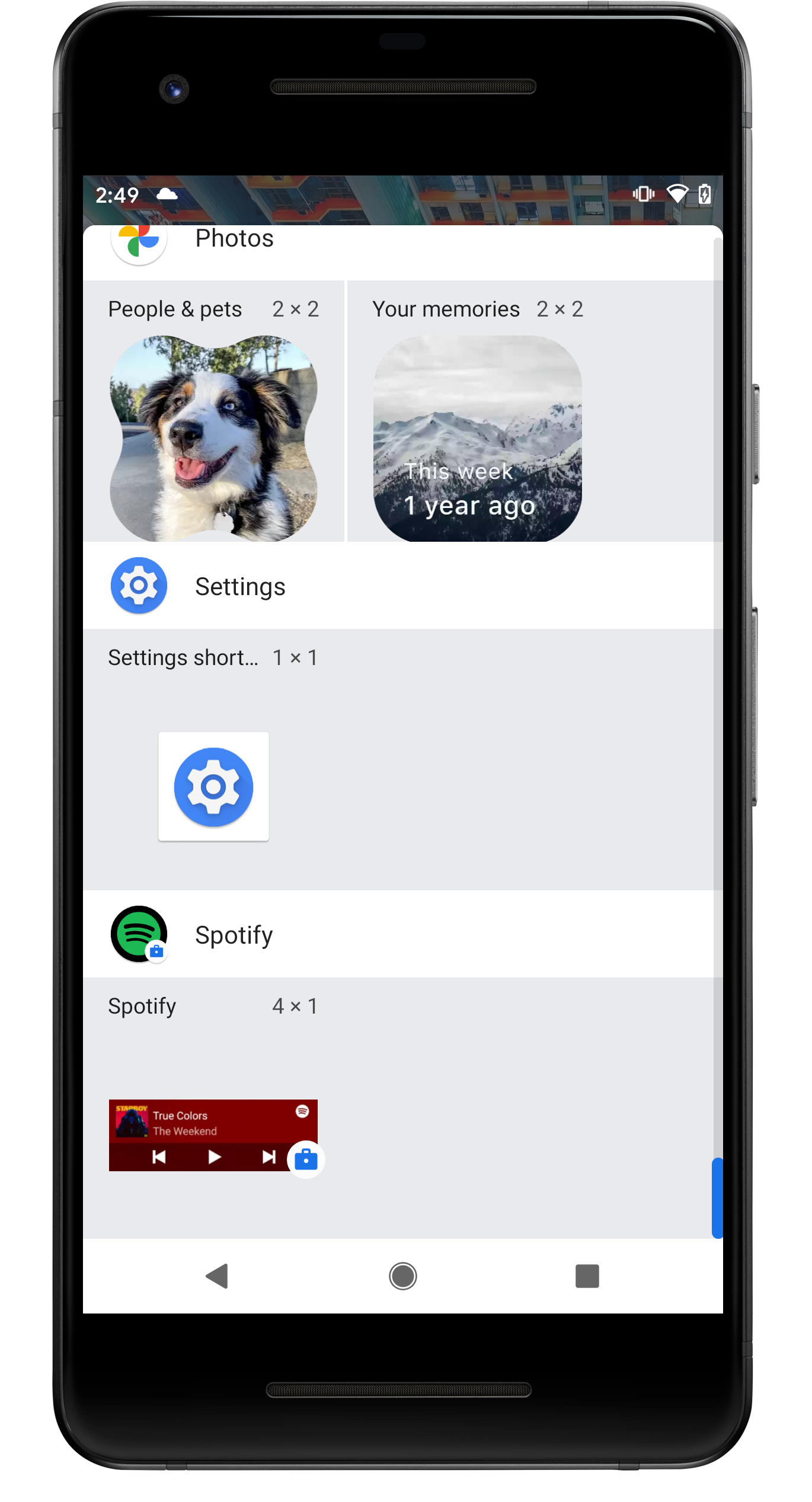
Allow Widgets From Work Profile Apps
By using a Work Profile with Android Enterprise on personal Android devices, you can strictly separate business data and applications from personal data, which has the great advantage of protecting your business information. At the same time, however, it can cause difficulties in day-to-day use. For example, as the home screen of the devices is not in the work profile and your users want to use and add a widget to a business application that is only available in the work profile, this is not possible by default due to the strict separation. To help you decide whether to allow widgets from work profile applications on the Home screen, you can now use a new restriction of the same name to allow users to add widgets from any application that is in the work profile to their Home screen. By default, the restriction is disabled, and the example below shows the difference between an enabled and disabled restriction using the Spotify application.
| Spotify is installed on this device in the Work Profile section (only). | By default and with disabled restriction, users won't be able to add the Spotify widget to the home screen. | If the restriction is enabled, Spotify is listed in the available Widgets section. |
 |
 |
 |
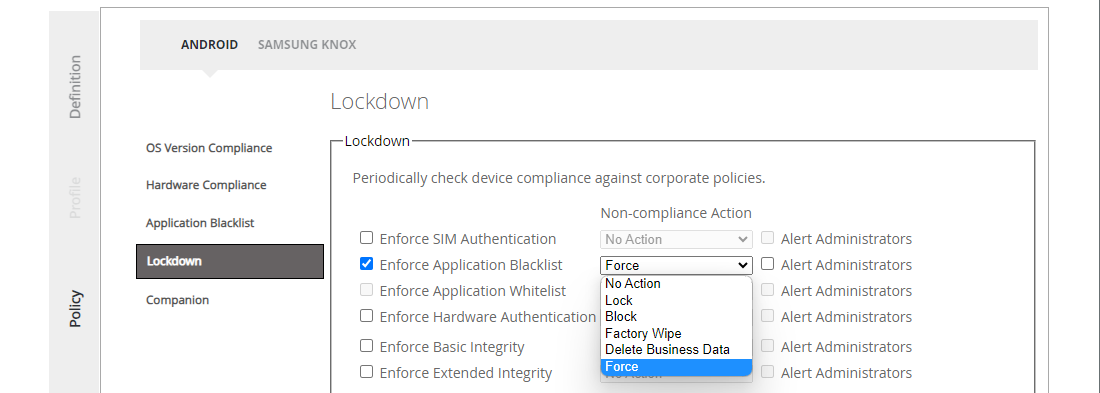
Force Application Blacklist
Silverback offers in general two ways to influence or track installed applications on Android or Samsung Knox devices. The fist one, the Silverback blacklist is a method that does not interfere directly with the device and Silverback will perform here certain actions based only on the list of installed applications that devices send to the management system if an unwanted application is installed or detected on the device. Another method is the Enforced Blacklist/Whitelist, which Samsung made available some time ago with the Samsung Knox API. Here, the management actively influences the device with a restriction and configures it in such a way that an array of unwanted or explicitly wanted applications become unusable/usable. With this release, we are happy to announce that the Enforced Blacklist is now available for Android devices, too. This improves the whole process of application management with the combination of enabling/disabling system apps through the enrollment process. For example, you may miss a particular app on the device because you have not enabled the new Enable System apps option. However, if you activate the option, you will probably have more applications on the device by default than you actually want. With the Enforced Blacklist, you have now the simple option of deactivating unwanted applications.
iOS, iPadOS, macOS
Please find all new iOS, iPadOS, macOS related features in Silverback 23.0 Update 1 below:
Rapid Security Response
Apple introduced with iOS/iPadOS 16 and macOS 13 with Rapid Security Response (RSR) a mechanism for shipping security fixes to users more frequently and we added in Silverback 22.0 Update 1 already the corresponding restrictions Allow Rapid Security Response Installation and Allow Rapid Security Response Removal to control the behavior for supervised devices. As each Rapid Security Response is versioned relative to its base operating system version, starting with “a,” then “b,” and so on, we added in this Silverback release an updated version of the Device Information for each device that includes the Rapid Security Response versioning . Please refer to the explanation belows to get an overview of all changes and improvements that will take place with Silverback 23.0 Update 1 with the integration of the Rapid Securiy Response information:
| Where | What | New Keys |
|---|---|---|
| Device Information | Three new keys corresponding to Build Versions and the Rapid Security Response has been added to the Device Information section when opening the Device View. |
|
| Available OS Updates | Three keys corresponding to the Rapid Security Response has been added to the Available OS information section when opening the Device View. |
|
| Managed, blocked, and checkout | The OS Version shows now the combined information between OS Version and the Supplemental OS Version Extra, which relates to the installed version of the Rapid Security Response. |
|
| API | The response string for the OS Version has been extended with the Supplemental OS Version Extra information. |
|
| Service Bus | The response string for the Version in SPSComputerClassOS and UemPlatformClassBase has been extended with the Supplemental OS Version Extra information. |
|
Available OS Updates
In addition to the already mentioned new keys for the Rapid Security Response information, we added additional information to the Available OS Updates section when opening the Device Overview.
| Where | What | New Keys |
|---|---|---|
| Available OS Updates | Six news keys has been added to the Available OS information section when opening the Device View. If platforms will not report a specific key it will be indicated with a minus sign. |
|
Especially the Last Scheduled Update Response is a very useful information while forcing an OS Update via the Silverback Management Console. After executing the action and with a new device refresh, the device will report the status of the installation with one of the following responses:
- Idle: The update is idle.
- Downloading: The software update is downloading.
- Download
Failed: The download failed. - Download
Requires Computer: Tether the device to download this update. This value is only available in iOS. - Download
Insufficient Space: There isn’t enough space to download the update. - Download
Insufficient Power: There isn’t enough power to download the update. - Download
Insufficient Network: The network capacity is insufficient to download the update. - Installing: The software update is installing.
- Install
Insufficient Space: There isn’t enough space to install the update. - Install
Insufficient Power: There isn’t enough power to install the update. - Install
Phone Call In Progress: Installation couldn’t occur because a phone call is in progress. - Install
Failed: Installation failed due to an unspecified reason.
New Improvements
Please find all new Improvements in Silverback 23.0 Update 1 below.
Management Console
- Added mechanism to adjust the logo size for Azure AD Terms & Conditions in case of big logos are used
- Renamed the headline in Editing Device IDs in Hardware Authentication
Apple Management
- Fixed an issue with forcing OS Updates while device reports duplicates for Available OS Updates
- Fixed an issue with automatic updates for VPP applications
- Renamed the following labels Available OS Update section in the Device Overview:
- Is Critical to Critical Update
- Is Configuration Data Update to Configuration Data Update
- Is Firmware Update to Firmware Update
- Allow Install Later to Allows Later Installation
- Restart Required to Requires Restart
- Changed the visibility of labels in the Available OS Update section according to the supported platform:
- Product Name is now no longer displayed for macOS
- Install Size is now no longer displayed for macOS
- App Identifiers to Close is now only displayed for macOS
- Configuration Data Update is now only displayed for macOS
- Firmware Update is now only displayed for macOS
- Is Preview has been removed completely
- Added parsing condition for unsupported platforms for synchronized VPP apps that caused the log entry Error casting app to device due to unsupported platforms
- Extended length for database values for company settings information in the Device Enrollment Program Token
- Added App Management information for macOS Enterprise applications in App Portal and Tags
Android Enterprise
- Added information for mandatory fields while creating an Advanced QR-Code Provisioning
- The counter for OTP expiry (hours) now uses increments of 1 instead of 10 while creating an Advanced QR-Code Provisioning
- An entered Wi-Fi password is now temporarily kept if a mandatory setting is not specified while creating an Advanced QR-Code Provisioning
- Fixed an issue with true false values for Advanced QR-Code Provisioning (e.g. Hidden Network) that cause an issue to review the QR-Codes
- Fixed an issue with the installation of Private APN Profiles for Samsung Knox
- Adjusted Label Names and added with Configuration Name and APN Type new configuration keys for the Private APN Profiles for Samsung Knox
- Fixed an issue where Shared Device Information Profile is sent to Android and Samsung Knox devices
- Fixed an issue with Tag Auto Population via Pre-Assigned Label through Hardware Authentication
- Fixed an issue with showing multiple entries for the same app name in Whitelist Violation
- Added App Identity information when editing an Enterprise application in App Portal
Windows 10/11
- Added missing condition for WNS Push task to send WNS Push Notification only to active devices
Knowledgebase
The following new Knowledge Base articles has been added:
Known Issues
In the initial release version of Silverback 23.0 Update 1, an issue occurred that when the Enable System Apps setting is changed, the managed account is re-provisioned and consequently all provisioned managed play apps are reinstalled. The issue has been fixed in the Silverback 23.0.1.26 Hotfix.