Release Notes Silverback 23.0 Update 3
About This Release
Matrix42 Silverback 23.0 Update 3 provides new and improved features that have been implemented. During the development of this version, we have been focusing on valued feedback from our customers and partners to provide an ideal feature selection.
Visit the following playlists on the Matrix42 YouTube channel to get a short overview presentation of the major new features: Link to English Video-Playlist | Link to German Video-Playlist.
Build Information
- Download: Marketplace
- Initial Build Version: 23.0.3.60
- Knowledgebase Hotfix Overview
New Features
Android Enterprise
iOS, iPadOS, macOS
New Improvements and Changes
Known Issues
New Features
Android Enterprise
Please find all new Android Enterprise related features in Silverback 23.0 Update 3 below:
Embedded KPE Premium Key
This year, Samsung offered Enterprise Mobility Solution, a very nice opportunity to provide a premium key for the Knox Service Plugin to all customers. Whenever you perform a configuration with Silverback 23.0 Update 3 for the Knox Service Plugin, all premium features are automatically activated for you with us as a verified Knox partner and our EMM partner key generated for this purpose. Conversely, as a customer, you no longer need to activate your own premium license to benefit from the available premium features. The key is automatically added by us in a hidden value to the Knox Service Plugin configuration for both forms of Android Enterprise management, i.e. management with the Companion and via the Android Management API. The KPE Premium license is supported and will be sent to Android devices with Android version 13 and higher, and you can check the integration of the key in the Knox Service Plugin if you have enabled the debugging feature in the configuration, regardless of whether you configure the Knox Service Plugin via the standalone profile or via the managed configuration of the application.
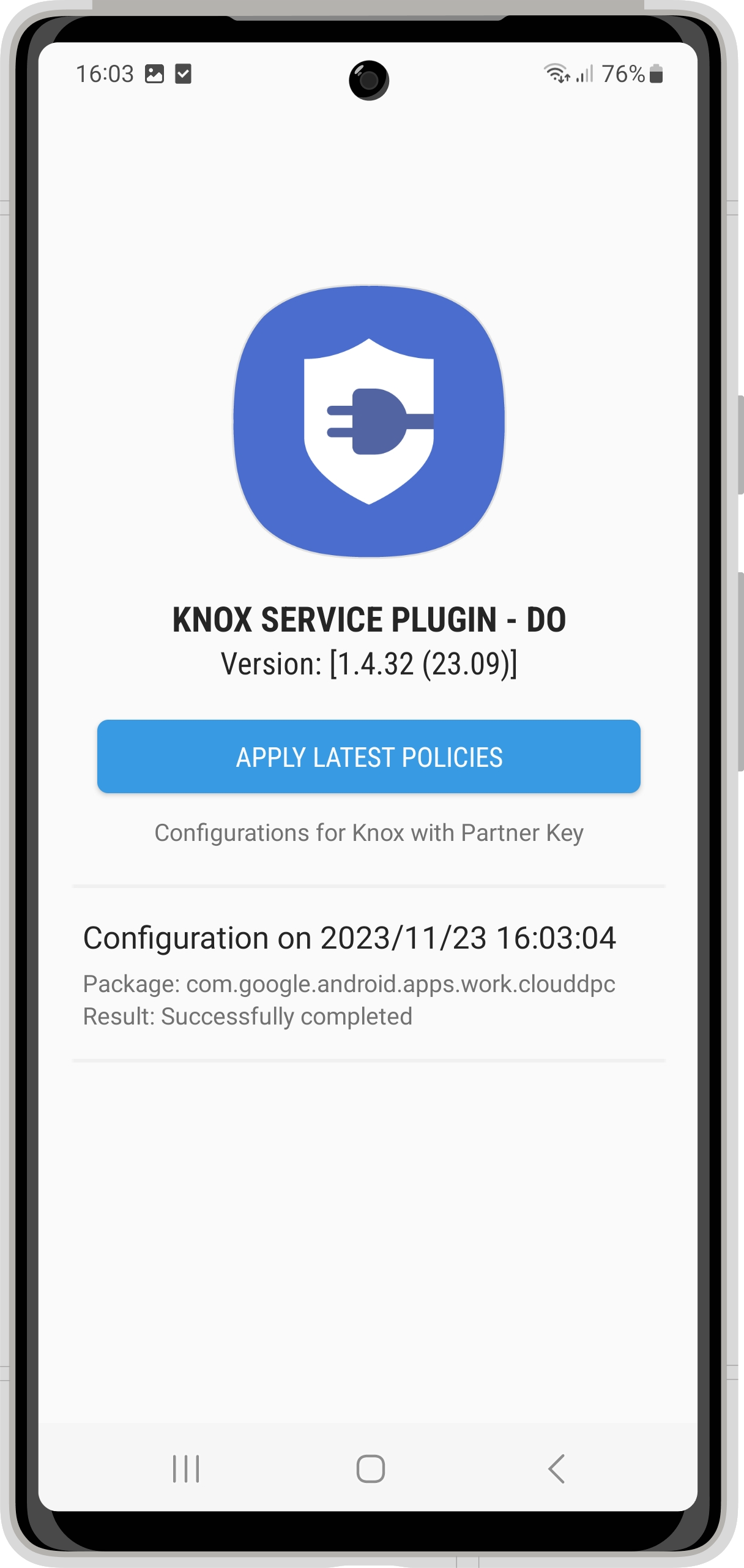 |
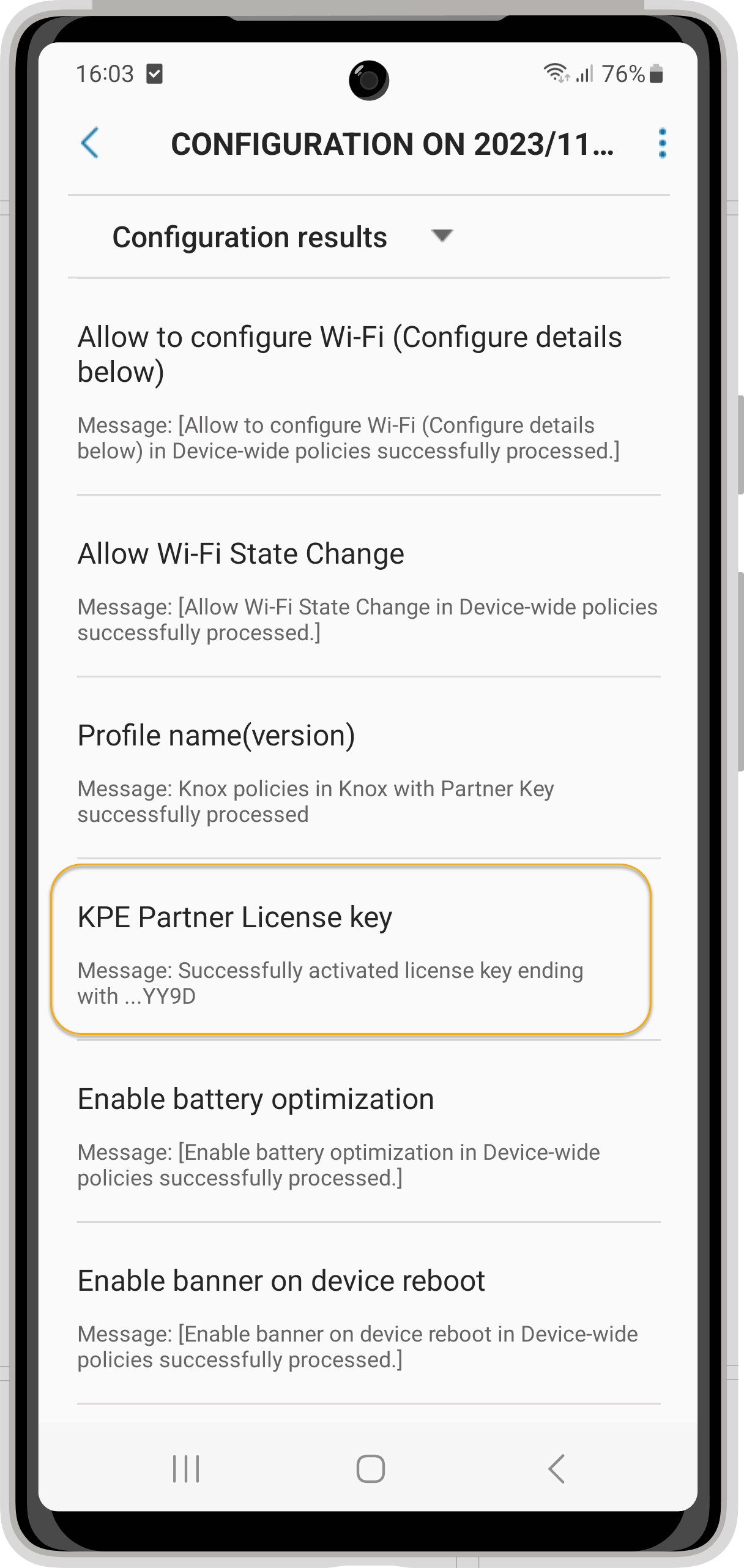 |
Google Play Device Integrity Compliance
We introduced device integrity checking via Google's SafetyNet Attestation in Silverback a few years ago. The device integrity check allows you to see if you have devices in your management that have, for example, an unlocked bootloader, a custom ROM installed, a virtual device, or devices that have not been certified by the manufacturer, including other security features that can be checked by Google. You can view device integrity information for each Android and Samsung Knox device in the Device Overview, and you can also enforce compliance rules with Silverback by configuring a lockdown policy if devices fail to meet security requirements. Google announced, that the Play Integrity API will replace the SafetyNet Attestation API to consolidate several device integrity offerings (including the SafetyNet Attestation integrity verdict) under a single API. The Integrity API unifies Google Play anti-abuse features with a collection of integrity signals to help Android app and game developers detect potential risks, and with Silverback 23.0 Update we added the Play Integrity API.
The operation has remained relatively similar. The Companion application has the ability to submit a request for an assessment to Play Integrity and Play returns multiple device integrity verdicts and rules can be enforced based on that with the Silverback backend. Therefore, with this new Silverback release, you will now find new device information that displays the verdicts from Google Play Device Integrity, and you will find new compliance rules in the Lockdown section of Tags that you can enforce based on the verdicts that Play Integrity reports about the device. Compared to the SafetyNet API, the Play Integrity API does not have an advisory response, but it does have a slightly more granular structure for the different levels of integrity checking.
Device Overview
When your devices are running on the new Companion version 23.0 Update 3 and checking in, you will find the new 3 verdicts in the Device Overview, which come via the Google Play Integrity API. The verdicts include a check of Basic, Device and Strong Integrity.
- Basic Integrity: The Basic Integrity indicates that the devices passes basic system integrity checks., but the device may not meet Android compatibility requirements and may not be approved to run Google Play services. For example, the device may be running an unrecognized version of Android, may have an unlocked bootloader, or may not have been certified by the manufacturer.
- Device Integrity: Device Integrity represents that the device is an Android-powered device with Google Play services and that the device passes system integrity checks and meets Android compatibility requirements. If the device does not meet the Device Integrity it means that the device that has signs of attack (such as API hooking) or system compromise (such as being rooted), or the device is not a physical device (such as an emulator that does not pass Google Play integrity checks).
- Strong Integrity: The Strong Integrity offers the highest resilience against attacks and circumvention because devices returning this label include a strong guarantee of integrity, such as hardware-backed proof of boot integrity.
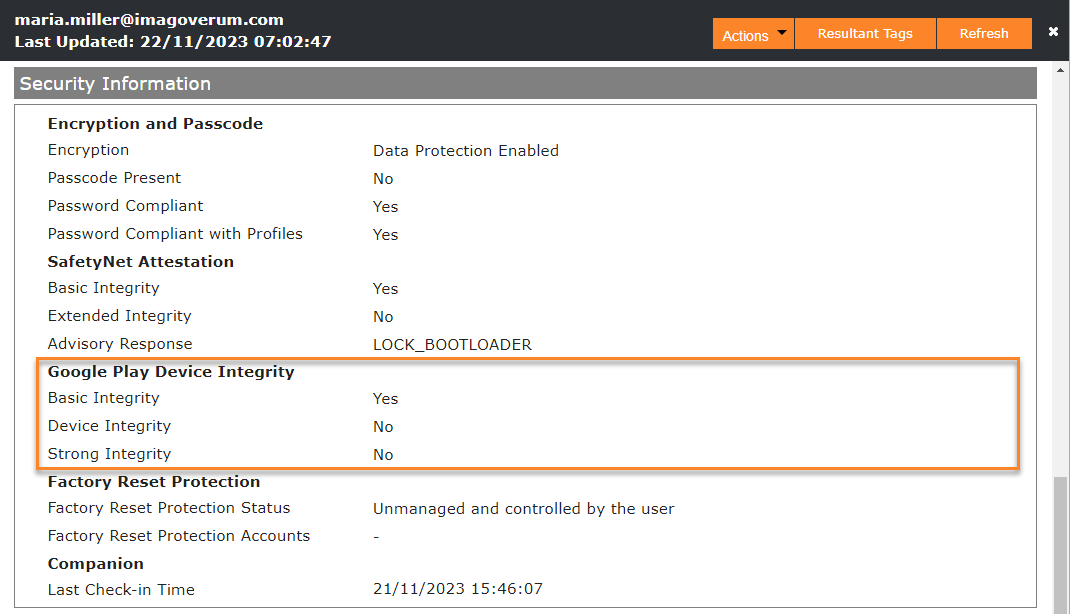
The screenshot above illustrates a device that has an unlocked bootloader.
Lockdown Policies
The Lockdown configuration in a Tag allows you to determine what device compliance policies are enabled and what action should automatically occur when a violation is detected. Each policy is enabled/disabled through their associated checkbox. Enabling a lockdown policy ensures that the device is inspected to ensure it is compliant with that policy during the initial enrollment as well as at regular intervals of check ins. With Silverback 23.0 Update 3 you will see three new lockdown policies with the familiar actions and options. Note that the blocking policies are only applied to devices for which game integrity information is available. If the information is displayed as - in the Device Overview, no action will be taken.
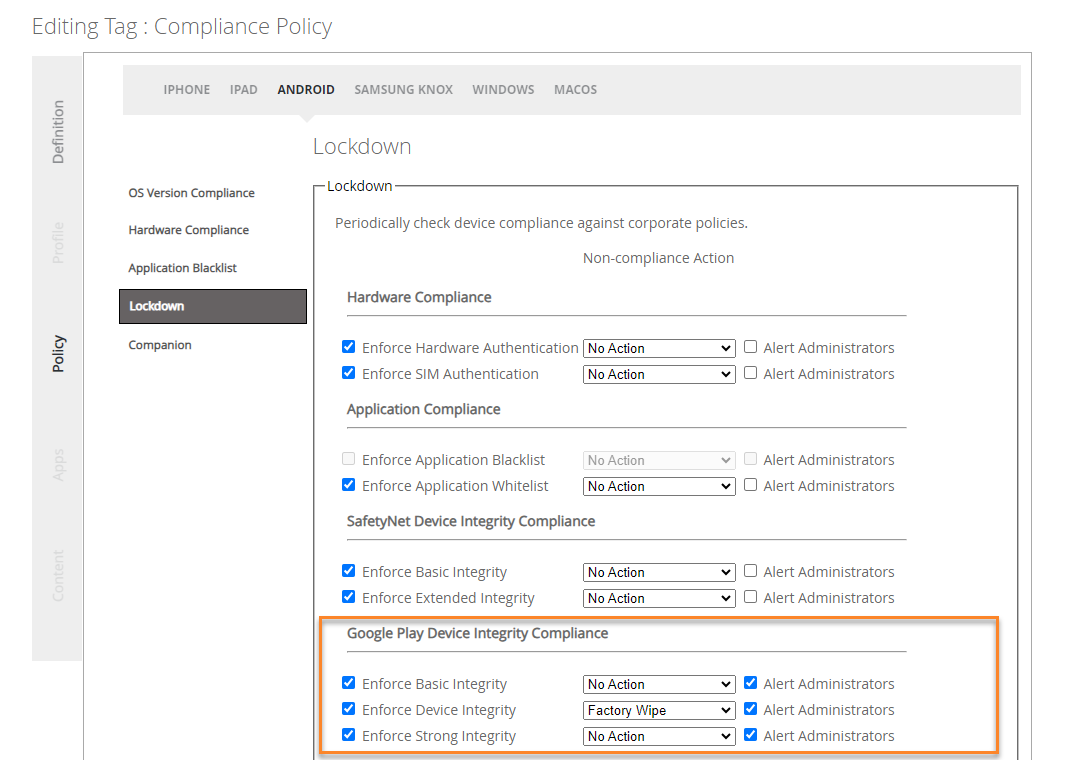
Migration
As the SafetyNet Attestation API will be retired by Google on January 31, 2025, we recommend that you start with disabling your SafetyNet device integrity compliance and start using the Google Play device integrity compliance lockdown policies, soon. You can also run both lockdown policies together for a period of time before fully switching to the Google Play Integrity API once you have ensured that your devices have at least Companion Version 23.0 Update 3 installed by January 2025. To ensure that your devices are updated to the new Companion version in a timely manner, we recommend that you distribute the Companion application as a Managed Play app for one day and enable the App Management option to automatically push to managed devices. In addition, ensure to configure the Auto-update apps option accordingly in the Managed Account and/or in the Work Profile configuration.
Available OS Updates
Another new feature for Android Enterprise device management via the Companion application is the display of an available OS update in the device overview.
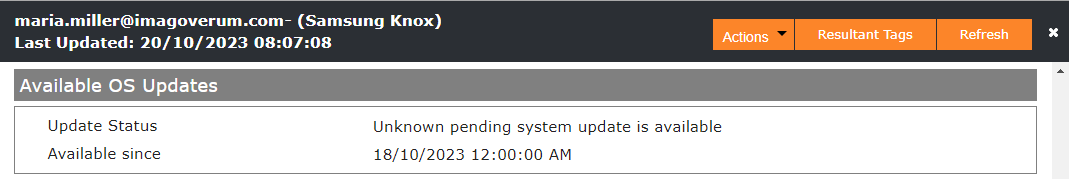
A total of 3 possible update status information can be displayed in addition to the Available since information:
- Pending OS update is available
- Pending security update is available
- Unknown pending system update is available
The information is gathered from the device to the Companion, and it appears that the main information provided via the SDK is that there is an Unknown pending system update available. So in most cases you will see the Unknown pending system update is available. If you want to control OS Updates, please refer to the System Update profile.
NFC Enrollment Enhancements
With Android Enterprise, you or your users can integrate your devices into the management in a number of ways. In addition to the various classic methods or zero-touch enrollment, provisioning devices via NFC tags is a very efficient and simple method. As the administrator, you only need to describe an NFC tag with a few configurations, and you or your users can then start and complete the enrollment process in the management system by contacting the NFC tag the first time the device is started. To provide more details, we have published a dedicated knowledgebase article on NFC enrollment, and with Companion 23.0 Update 3, a special authentication field is now available to integrate devices without requiring users to perform explicit authentication themselves.
iOS, iPadOS, macOS
Please find all new iOS, iPadOS, macOS related features in Silverback 23.0 Update 3 below:
New Restrictions for iOS 17 and macOS 14
The new major iOS and macOS versions came across with a couple of new built-in mobile device management business capabilities, which we added into this release and happy to share with you. In general, restrictions are easy on/off settings that enhances the configuration options of your managed devices and increases security options. Silverback 23.0 Update 3 contains the following new restrictions for devices:
| Availability | Options | Requirements | Description | |
|---|---|---|---|---|
| Allow Widgets on a Mac | iOS | Enabled or Disabled | iOS 17 (supervised) | Disallows iPhone widgets on a Mac that has signed in the same AppleID for iCloud. |
| Allow Account Modification | macOS | Enabled or Disabled | macOS 14 | Disables account modification. Requires a supervised device. |
| Allow Remote Management Sharing | macOS | Enabled or Disabled | macOS 14 | Prevents modifying the Remote Management Sharing setting in System Settings. |
| Allow Siri | macOS | Enabled or Disabled | macOS 14 | Disables Siri. |
| Allow Bluetooth Sharing Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modifying Bluetooth setting in System Settings. |
| Allow iCloud Freeform Services | macOS | Enabled or Disabled | macOS 14 | Disallows iCloud Freeform services. |
| Allow Changing Device Name | macOS | Enabled or Disabled | macOS 14 | Prevents the user from changing the device name. |
| Allow File Sharing Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modifying File Sharing setting in System Settings. Available in macOS 14 and later. |
| Allow Fingerprint Modification | macOS | Enabled or Disabled | macOS 14 | Prevents the user from modifying Touch ID or Face ID. |
| Allow Internet Sharing Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modifying Internet Sharing setting in System Settings. |
| Allow Local User Creation | macOS | Enabled or Disabled | macOS 14 | Prevents creating new users in System Settings. |
| Allow Printer Sharing Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modifying Printer Sharing setting in System Settings. |
| Allow Remote Apple Events Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modifying Remote Apple Events Sharing setting in System Settings. |
| Allow Startup Disk Modification | macOS | Enabled or Disabled | macOS 14 | Prevents modification of Startup Disk setting in System Settings. |
| Allow Time Machine Backup | macOS | Enabled or Disabled | macOS 14 | Prevents modification of Time Machine settings in System Settings. |
| Force On-Device Only Dictation | macOS | Enabled or Disabled | macOS 14 | Disables connections to Siri servers for the purposes of dictation. Also available for user enrollment. |
New Improvements
Please find all new Improvements in Silverback 23.0 Update 3 below.
Management Console
- Added API Identifier into the Device Information
- Replaced the Silverback is unhandle to process screen with a user friendly message if wrong Service Bus Credentials were entered
- Certain French column names in the device overview now have shorter names
Android Enterprise
- Fixed an issue that Helpdesk role could Reset Passcode for AMAPI device
- The username shows now the user friendly short name in the Hardware Summary Dashboard for AMAPI devices
- Removed old dependencies for Log entries in the Android Enterprise section
API
- Fixed incorrect Device Parameter for deviceHardwareTypeName in the API Documentation for the get devices by parameter operation
- Added deviceSerialNumber, imei, udid as device parameter for the get devices by parameter operation
Windows 10/11
- Fixed a small UI issue when uploading an *.msi package and the validation message appears
- Added a self healing mechanism to automatically re-create the default WNS token if authentication fails
Knowledgebase
The following new Knowledge Base articles has been added:
New Changes
- Renamed Force On-Device Dictation to Force On-Device Only Dictation and moved to Siri Restriction Group
- In this release, we've implemented data telemetry to capture anonymous usage metrics of our software. This feature strictly collects non-personal data related to the usage and performance of the software, ensuring user privacy is fully respected. This will aid in enhancing future updates and overall user experience. For additional information, please refer to Supplementary data protection information on the transmission of so-called telemetry data.
Known Issues
- Some tooltips for German language restrictions have an extra space, and some tooltip translations are not adjusted correctly. This issue has been fixed with Silverback 23.0.3.61
- If all devices are selected in the device overview on the first attempt, the button for the multiple action does not work. The workaround is to first select 2 devices and then tick the box for All devices to activate the button for the multiple action. This issue will be fixed with Silverback 24.0. This issue has been fixed with Silverback 23.0.3.69