Credentials
Overview
Credentials are used to discover additional information within your environment. Credentials also allow a Configuration Item to gather information from your environment without loading or enabling additional agents and services. Depending on your environment, valid Credentials may be required. Use the Credentials Management page to add and update Credentials.
In order for FireScope to connect to or collect data from your infrastructure, an SNMP community string or username and password may be required. This includes APIs such as VMware, NetApp, Cisco UCS, Amazon AWS and others. These credentials are also used by Discovery to collect details regarding a discovered asset, such as configuration information and potential Attributes for monitoring. To simplify configuration, all credential configuration is centralized in the Credentials section of the Configuration menu. From here you can create or edit any Credentials that FireScope SPM may need.
Note: Credentials are Edge Device specific. This allows you to designate shared Credentials (such as SNMP) per environment with a dedicated Edge Device.
LDAP Credentials
FireScope SPM has the ability to perform queries against LDAP servers such as Microsoft Active Directory, for e.g. identifying user privilege escalation, changes in Group Policy and more. In order to perform these queries, proper authentication information will need to be provided by adding an LDAP Credential. LDAP credentials allow you to add LDAP connections which can be associated with a CI to collect data.

To create an LDAP Credential,# Click on Configuration > Discovery > Credentials Managements. Credential Management page will be displayed.
- Click on View next to LDAP credentials. LDAP Credentials Management page will be displayed.
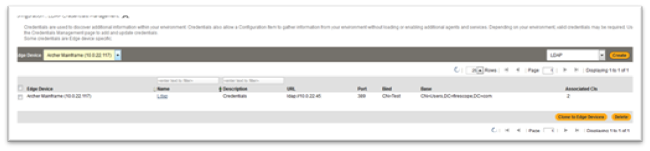
- Click on Create button in the upper right hand corner. Create LDAP Credentials Management form will be displayed.
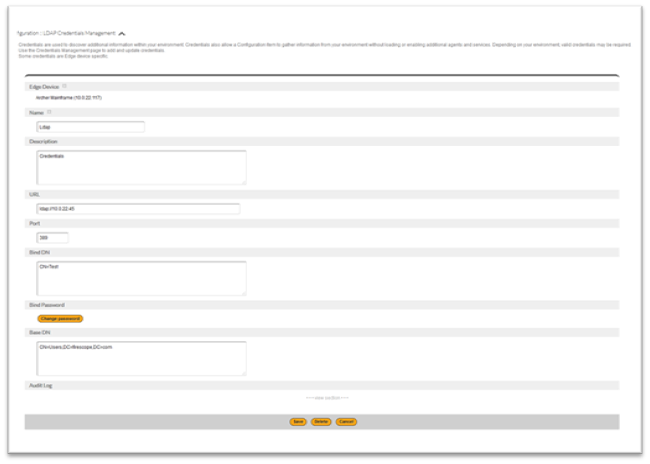
- Name: Enter a name which will be used to identify these credentials.
- Description: Enter helpful description that will help to understand these credentials.
- URL: Enter a path to an LDAP server. For e.g. Enter the path as LDAP://<server dns or IP>.Note: Do not put a trailing / at the end of the path.
- Port: Enter a port LDAP server will respond to. Mostly it is port 389
- Bind DN: Enter the container name of the account to be used. For e.g Bind DN: CN=Test
- Bind Password: Enter the password for the account.
- Base DN: Enter the entire container path for the account. For e.g. CN=Users,DC=firescope,DC=comIn the following example, the account to be used is “Test” and the full LDAP path to this account is CN=Test,CN=User,DC=firescope,DC=com.
- Click Save to complete the setup of the LDAP credentials.
Note:- Once a LDAP credential have been defined, a CI can be associated to a single LDAP credential, via the CI Form.
- Now that you have working LDAP credentials attached to the CI, you can create the LDAP check attributes. Only attributes of CI’s associated to an LDAP credentials will be able to collect LDAP data.
- Attributes will need to be created with a type of LDAP check. Attributes of CI’s associated to an LDAP connection will be able to collect LDAP data.Data can be viewed by clicking on data history icon
SNMP Credentials
SNMP credentials are utilized by the following: * CI/Attributes – SNMP attributes within a CI will utilize the SNMP credential linked to the CI to establish connection and access
- Network Discovery Jobs – Network discovery jobs will utilize SNMP credentials on a first-match basis. If you want to create and configure CIs with discovery profiles, order your SNMP credentials with the setting that can the most access first.Note: All credentials are associated to an Edge Device to better target multiple environments that may have different settings for community or authentication. Discovery job and CIs can only utilize credentials that have the same Edge Device.
- Click on Configuration > Discovery > Credentials. Manage Credentials page will be displayed.

- Click on View next to SNMP credentials, SNMP Credentials Management page will be displayed.

- Click on the Create button (upper right hand corner), SNMP Credentials Management create form will be displayed.
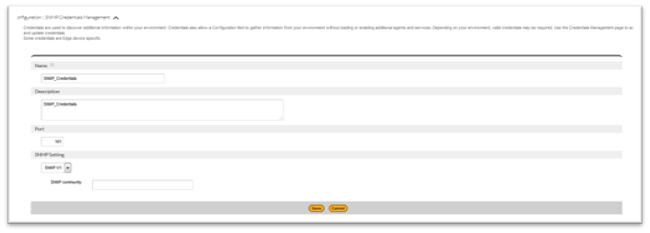
- Edge Device: Select an Edge Device to designate the data collection or operation target.
- Name: Enter a descriptive name for this item.
- Description: Enter description
- Port: Enter port number
- SNMP Setting:
- SNMP V1:
- Requirement: Device must be SNMPv1 compatible or have an SNMP Agent installed. This includes most networked assets.
- Information: The SNMPv1 SMI specifies the use of a number of SMI-specific data types, which are divided into two categories:
- Simple data types
- Application-wide data types
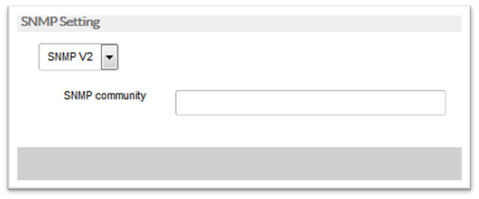
- Access Requirement: Community for e.g. most devices have a setting for public
- SNMP V1:
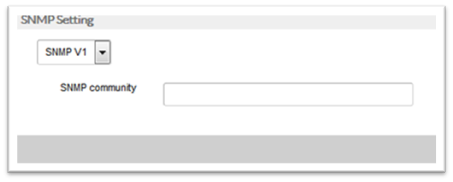
- SNMP V2:
- Requirement: Device must be SNMPv2 compatible or have an SNMP Agent installed.
- Information: The SNMPv2 SMI is described in RFC 2578. It makes certain additions and enhancements to the SNMPv1 SMI-specific data types, such as including bit strings, network addresses, and counters. Bit strings are defined only in SNMPv2 and comprise zero or more named bits that specify a value. Network addresses represent an address from a particular protocol family. SNMPv1 supports only 32-bit IP addresses, but SNMPv2 can support other types of addresses as well. Counters are non-negative integers that increase until they reach a maximum value and then return to zero. In SNMPv1, a 32-bit counter size is specified. In SNMPv2, 32-bit and 64-bit counters are defined.Additionally, SNMPv2 also specifies information modules, which specify a group of related definitions. Three types of SMI information modules exist: MIB modules, compliance statements, and capability statements.MIB modules contain definitions of interrelated managed objects.Compliance statements provide a systematic way to describe a group of managed objects that must be implemented for conformance to a standard.Capability statements are used to indicate the precise level of support that an agent claims with respect to a MIB group. An NMS can adjust its behavior toward agents according to the capabilities statements associated with each agent.
- Access Requirement: Community for e.g. most devices have a setting for public
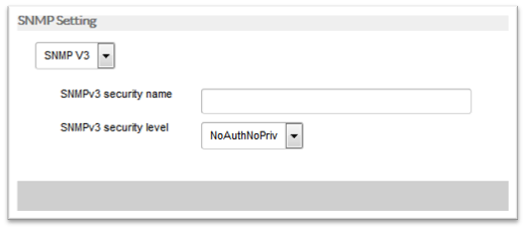
- SNMP V3:
- Requirement: Device must be SNMPv3 compatible or have an SNMP Agent installed.
- Information: Essentially offers the same information as SNMPv2, with the addition of 3 important security features:
- Message integrity to ensure that a packet has not been tampered with in transit.
- Authentication to verify that the message is from a valid source.
- Encryption of packets to prevent snooping by an unauthorized source.
-
- Access Requirement: SNMPv3 has several variations of access control. You will need to provide some of the following values based on the type of authentication required by the device’s settings.
- security name
- security level
- authentication type
- auth passphrase
- privacy type
- priv passphrase
- Access Requirement: SNMPv3 has several variations of access control. You will need to provide some of the following values based on the type of authentication required by the device’s settings.
- Click on the Save button.