System Requirements
Overview
The following outlines the minimum requirements required for implementation of FireScope. Please note that FireScope only supports environments whose dependencies are within the current support by the original equipment manufacturer. For example, FireScope virtual machines will not be supported on VMware versions that have reached the end of general support by VMware.
Edge Device System Requirements
Edge devices can be physical or virtual appliances. They are deployed on-premise to perform discovery of IT assets, data collection and accurately forwarding all of this data to the FireScope cloud.
- 8 vCPUs
- 12 GB of RAM
- 120GB for Primary Disk
Note: The storage requirement for the Edge device is large, to ensure sufficient storage space for caching in case of loss of connectivity with the FireScope cloud. The number of Configuration Items it collects from frequency of polling, and scope of data collection methodologies impact its performance.
Additional Components Required for an On-Site Implementation
In addition to the overall environment requirements, ensure that you meet the requirements for each individual component. Requirements for each component—EWC, EAC, ESC are outlined in the following sections. Please note that if you are implementing FireScope using the Software-as-a-Service(SaaS) model, the following components will not be required.
Elastic Web Component (EWC)
Of the three cloud components of FireScope , the EWC has the lowest requirements as this component is dedicated to delivering the FireScope user experience and nothing else. Because of this role, the primary consideration in sizing is the number of concurrent users. Factors such as the size of the environment and activity will not significantly impact the EWC. As a result, in many environments, only a few EWC instances may be required.
Each UI server needs:
- 4 vCPUs
- 4 GB of RAM
- 40GB for Primary Disk
Elastic Application Component (EAC)
The EAC is responsible for receiving data from the Edge device(s), normalizing the data, and analyzing status of Event Definitions, Aggregate Event Definitions, and Policies. Therefore, CPU becomes a critical requirement for this component.
- 6 vCPUs
- 12 GB of RAM
- 60GB for Primary Disk
Elastic Storage Component (ESC)
Storage and memory are key for the ESC, as this is where all Attribute data is stored and queried. As much of the data set as possible is stored in memory for best query performance, therefore the amount of memory provided for this type of instance has implications on performance of the entire solution. Data retention settings are also key considerations for this instance type.
- 4 vCPU
- 24 GB of RAM
- 60GB for Primary Disk
- 500GB for Secondary Disk
Note: For each ESC, provision a secondary VMDK with minimum storage of 500 GB. Also, anti affinity rules must be in place to ensure no 2 ESC nodes are ever on the same host or datastore.
Port Communication Requirements
All communication between the Edge device and the FireScope cloud is initiated by the Edge device for security purposes. The following ports will need to be open for successful communication between FireScope and each Edge device.
Internal
The following table specifies the internal ports you must keep open for the listed servers.
| Servers | Open Ports |
| Elastic Storage Component(ESC) <———-> Elastic Web Component (EWC) | 22, 27020, 30000, 40000 |
| Elastic Web Component (EWC) <–——-> Elastic Application Component( EAC) | 22, 25, 80, 443, 8080 http: 28050, 28051 https: 28060, 28061 |
| Elastic Application Component( EAC)<–——-> Elastic Web Component (EWC) | 15672, 5671, 5672 |
| Elastic Application Component( EAC)<———-> Elastic Storage Component(ESC) | 22. 30000, 40000 |
| Edge <———-> Elastic Application Component( EAC) | http: 18050, 18051 https: 18060, 18061, 5671, 5672 |
| Analytic Client Machine | 40000 |
External
The following table specifies the external ports you must keep open for the listed servers.
| Servers | Open Ports |
| Elastic Web Component (EWC) | 80, 443 |
| EMI | 8004 |
| Edge <———-> Elastic Application Component( EAC) | http: 18050, 18051 https: 18060, 18061, 5671, 5672 |
| Analytic Client Machine | 40000 |
| All Servers ←——-→ controller.firescope.com | 80, 443 |
| Web Services | 38050, 38051, 38060, 38061 |
| Edge —-> RabbitMQ | 5672 , 5671 |
| sFlow Collector ——> Edge | 6343(UDP) |
| NetFlow Collector —-> Edge | 2100 (UDP) |
| AWS VPC Flow Logs ——> Edge | 2200 |
Note:
- If you want to use 38060 for SSL you need to disable peer authentication.
- Edge to RabbitMQ—The edge has to reach web2 via ssl port 5671 or non ssl port 5672.
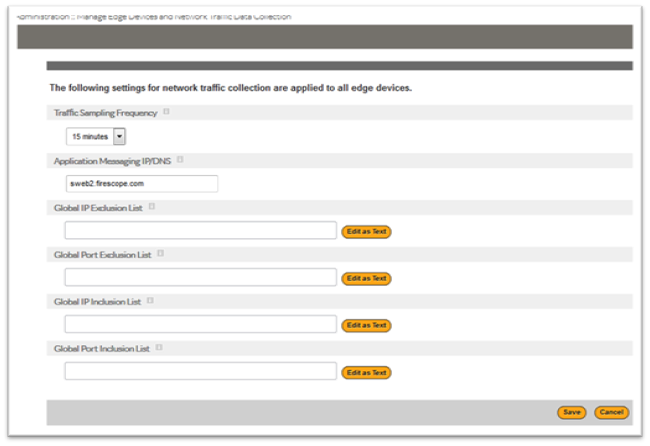
- The address each Edge should use to reach the RabbitMQ is to be filled out in the Global Network Traffic Settings form on the Edge Devices page inside your account.
Enter the address in Application Messaging IP/DNS field.
Web Browser Requirements
FireScope supports the following Web browsers:
| Internet Explorer | 8 and above Note: Compatibility mode not supported. HTML5 is not natively supported in versions older than 9. |
| FireFox | 6 and above |
| Safari | 3.2 and above |
| Chrome | 6.0 and above |
Additionally, the following requirements apply to all browsers:
- JavaScript is enabled
- Minimum resolution: 1024 x 768
On-Site Implementations Minimum Requirements
If you are opting for a private instance of FireScope , there are additional requirements needed for the FireScope Cloud itself. All of the previous minimum requirements are still required.
Ensure that you meet the following environment requirements to deploy FireScope successfully.
| ESX Servers | 3 (5 preferred) |
| Minimum Instances | 3 x EWC 2 x EAC 2 x ESC 1 x Edge Device |
| VM Environment | ESX servers with proper configuration, running versions currently under active support by VMware (Key settings are correct Time Source and Hostname) Standard VMware images, with VMDK support |
| Supported Storage | FC SAN (preferred) Fast iSCSI Direct Attached SAS *NAS is not supported. |
| Network | Fast Ethernet, fully switched Distributed vSwitches for ESX |
All primary components (EWC, EAC, and ESC) communicate over TCP/IP Protocol within the Cloud Environment. Each layer must have the appropriate access to the other layers in order for the application to perform optimally. As the Cloud Environment is typically housed in the same location, no special firewall rules or protocols should be required.