Performing emergency recovery
Performing emergency recovery
This section details the emergency recovery process. Emergency recovery may be needed in one of the following situations:
| Situation | Solution |
| Remote recovery: You have forgotten your password or lost/misplaced your smart card. | In this case you can recover the system via either the Helpdesk option (for details, see Helpdesk) or the recovery CD or USB stick (for details, see Recovery via CD or USB stick). |
| On-site: The boot code/pre-boot system is damaged/cannot boot to Windows after the system has been reinstalled | On-site: The boot code/pre-boot system is damaged/cannot boot to Windows after the system has been reinstalled |
The prerequisite for on-site emergency recovery is a valid ERI file! If you have not created one to a secure location (i.e. USB stick or CD) then this section is useless to you – your data is LOST!
For details about generating an ERI file, see Creating an ERI file.
Recovery via the Help Desk option
HelpDesk scenarios
The PBA component has built-in functionality to help you start the computer in the following emergency scenarios:
- Defective smart card readers, lost/forgotten/broken smart cards (via PBA HelpDesk). PBA HelpDesk will help you start the system a predefined number of times without a smartcard or a smart card reader (after successful authentication via the HelpDesk). For details, see Scenario 1.
- Forgotten Windows credentials (via PBA HelpDesk). PBA HelpDesk will help you start the system a predefined number of times without a smart card or a smart card reader (after successful authentication via the HelpDesk). For details, see Scenario 1.
- Forgotten/blocked smart card PIN (cards issued via Third-Party). For details, see Scenario 2.
- For smart Card PIN change refer to Change PIN of your Smart Card.
Challenge and response
The methodology behind the PBA HelpDesk is called ‘challenge and response’ - the user must relay a ‘challenge sequence’ to a HelpDesk administrator and in return receives a “response sequence” that authorizes PBA to set a specific recovery procedure in motion.
This process offers you the following:
- A more secure challenge–response process than in previous versions while still being 50% shorter. This is known as ‘Strong’ in the PBA admin GUI.
- A very short challenge–response process that offers a compromise between speed and security. This is known as ‘Comfort’ in the PBA admin GUI.
- Compatibility to HelpDesk keys generated in previous generations of the HelpDesk application.
The HelpDesk feature only applies if the following criteria are met:
- You have access to this form of remote assistance.
- The HelpDesk application has been installed, HelpDesk keys have been exported from it, and these keys have been correctly imported into PBA either during or after installation.
- The following procedure only describes the process as seen by the user. For further information about the HelpDesk application what both sides of the challenge–response process involves, refer to the Matrix42 Console Manual, description “Using Helpdesk”.
Scenario 1: Misplaced/lost/stolen smart card reader/smart card – forgotten/compromised User ID-password (disable PBA)
This section will guide you through the HelpDesk procedure to be used if you have problems with the smart card reader, mislaid or lost your smart card, or have forgotten your user ID/password. Both you and the HelpDesk administrator share one or more secrets for the purpose of identification. As to how the secret is administrated and stored is up to the parties involved and is not part of this guide or the Matrix42 Full Disk Encryption product. If you use smart card authentication, after this process is implemented, the computer will be able to boot without a smart card – but only a limited number of times. This means that the system security status is set to ‘transparent encryption’. This is a much weaker security status! Re-implement smart card authentication as soon as possible. Follow these steps to help you through the HelpDesk process:
- Click the Helpdesk button (or press the Alt+H keys) in the PBA logon dialog for remote assistance:
- The following dialog appears:

- Select Deactivate pre-boot authentication.
- If Deactivate pre-boot authentication is not active (greyed-out) then you have not imported HelpDesk keys into PBA. Helpdesk keys cannot be imported into PBA while Matrix42 Full Disk Encryption is in this state. Either you have to wait until smart card authentication can take place or use an ERD to bypass PBA (see Emergency recovery via boot CD or USB stick for details).
- Click Next.
- The HelpDesk contact details dialog appears:

- Contact the HelpDesk using the information provided in the dialog. Identify and authenticate yourself to the HelpDesk administrator. After successful authentication, click Next.
- The Request ID dialog appears:

- Relay the Request ID sequence (fields a & b) to the HelpDesk administrator.
- Once the sequence has been relayed to the HelpDesk, click Next.
The Request ID has a specific sequence to it. Should the user relay the sequence incorrectly to the HelpDesk administrator, or the HelpDesk administrator enter the sequence incorrectly in the HelpDesk application on their side, the computer will ‘beep’, alerting the user and the HelpDesk administrator that the sequence must be clarified. The cause of an incorrect entry usually applies to the characters entered into each field. The letters B, D, O, Y have been removed from the challenge–response process because they can be confused with another letter or number. If one of these characters is entered the computer will beep.
- Read and relay the request ID carefully! For example, a ‘1’ can look like an ‘I’.
- The Challenge sequence dialog appears:

- Relay the Challenge sequence (fields a & b) to the HelpDesk administrator and then click Next.
The Challenge sequence has a specific sequence to it. If you relay the sequence incorrectly, the HelpDesk administrator will ask you to clarify the sequence (as stated above). Once the sequence has been successfully relayed to the HelpDesk, the HelpDesk administrator may query you as to when, if possible, you can next authenticate yourself via the smart card and will set the number of reboots (without a smart card – transparent mode) accordingly.
- The Response sequence dialog appears.
- The HelpDesk administrator will relay the response sequence to you field-by-field (a to n).

- Enter the sequence carefully. Once the sequence is entered click Finish to complete the process. You are now able to start the computer and bypass PBA for a limited number of reboots.
- If you cannot authenticate within the reboot limit set by the HelpDesk, then the HelpDesk process must be repeated.
Scenario 2: Forgotten/compromised/blocked smart card PIN (PIN reset with PUK)
This section will guide you through the HelpDesk procedure to be used if you have forgotten or lost your smartcard, or if the smart card PIN has been blocked. It is possible to reset the smart card PIN only if the following conditions have been met:
- The smart card issued by third-party.
- PUK to reset the PIN.
Follow these steps in the PBA logon dialog:
- Click the Helpdesk button (or press the Alt+H keys) in the PBA logon dialog for remote assistance:

- The following dialog appears:

- Select Reset PIN of your smart card (you have PUK) and click Next.
- The PUK detail dialog appears:

- 1Enter the PUK.
- Enter the New PIN and confirm it.
- Click OK.
Change PIN of your Smart Card
This section will guide you to change smart card pin in PBA dialog. Follow these steps in the PBA logon dialog:
- Click the Helpdesk button (or press the Alt+H keys) in the PBA logon dialog for remote assistance:

- The following dialog appears:

- Select Change PIN of your smartcard and click Next.
- The PIN detail dialog appears:

- Enter the PIN.
- Enter the New PIN and confirm it.
- Click OK.
Emergency recovery via boot CD or USB stick
In an emergency in which the computer will not start properly, or the PBA is damaged, you can access the hard disk using a customized boot media that contains the emergency recovery application. This is referred to as the ERD.
- The ERD will enable you to perform a number of repair operations, provided that you have either a valid ERI file for the damaged computer (see Load ERI), or know the encryption keys so you can enter them manually (see Enter the encryption key manually).
- To perform any of the tasks detailed in this section you need to create an ERD. For details see Creating a WinPE emergency recovery boot CD or USB flash drive.
There are two types of emergency recovery application supplied with Matrix42 Full Disk Encryption:
- pe_erd_w32.exe – This is a GUI-based recovery application. This is the recommended application as it provides a full feature set for the administrator.
- pe_erd_console.exe – This is a command line-based recovery application created to provide only certain functions for scripted, remote recovery.
The emergency recovery console (command line)
The command line console has been developed to help administrators perform basic, scripted recovery tasks from within the WinPE environment.
| Parameter | Details |
|---|---|
|
eripath |
The path of ERI file. Note: If the ERI path contains spaces, it must be enclosed in quotation marks. |
|
Eripwd |
The ERI file password. Note: If the ERI password contains spaces, it must be enclosed in quotation marks. |
|
partition |
The partition to be decrypted. |
|
/H |
Display information in the command prompt about each parameter listed here. |
|
/L |
Load keys to memory for all encrypted partitions. |
|
/injectkey |
Inject the encryption keys from an ERI file. An automatic comparison takes place to add only the keys of any partition that has been encrypted by a previous FDE installation but is unavailable in the new one. |
|
/tpmoff |
Deactivate TPM protection. |
|
/tpmon |
Configure activation of TPM protection for next boot. |
|
/tpmrebind |
Deactivate TPM protection and configure reactivation for next boot. |
- To decrypt a specific partition, use:
pe_erd_console.exe eripath=f:\fde.eri eripwd=12345678 partition=d
pe_erd_console.exe eripath=f:\fde.eri eripwd=12345678 /L
- The command prompt will return if the partition is decrypted successfully.
- If unsuccessful an error will appear followed by the help information in the command prompt.
- To inject the encryption keys in the ERI file (to re-enable the partitions encrypted by a previous FDE installation), use:
pe_erd_console.exe eripath=A:\fde.eri eripwd=12345678 /injectkey
- Start the emergency recovery application (GUI).
- If you have stored your ERI file(s) on removable storage media (i.e. USB stick), then insert the media into the computer before starting from the ERD.
- The first step in performing an emergency recovery with the ERD, is to open the recovery application:
- Insert the ERD into the CD/DVD drive, start the computer, and allow the computer to boot from the CD. The ERD interface will of course, differ according to which ERD you are using: the WinPE CD only has a command line interface.
- The Matrix42 Recovery application should start automatically, but if not, use the command prompt to navigate to the directory: X:\Program Files\FDE\
- Enter pe_erd_w32.exe <press Enter>. Go to step 4.
- If the computer does not boot from the CD, then it is likely that the device is not set as the primary boot device in the BIOS. If so, change the BIOS settings accordingly, or possibly start the computer from a ‘one-time boot menu’.
- Open the menu entry Go>Programs> Matrix42 ERD (ENG).
- The emergency recovery application will start by scanning the Matrix42 Full Disk Encryption configuration on the computer:

- The application gathers information about the hard disk as well as information about the PBA and FDE components. The scan may last for a minute so please be patient.
- Once the scan is complete, the main window appears:

The main window enables you to select and perform the operations necessary for recovery. This window has the following functionality:
- Menu commands: The heart of the recovery application. See Menu commands for details.
- Workbench: This area allows you to choose a topic/node in the left-hand pane to display the information about that node in the right-hand pane. It is possible to right-click each node and select a command specific to that node from the context sensitive menu However, the Workbench area is used mainly to display information specific to a node in the right-hand pane. For further details about each node, refer to the end of this section. For details about the workbench nodes visible for standard hard disks, see Workbench for standard hard disks.
Before proceeding with any recovery task you must first authenticate yourself via one of the following methods:
- Load the ERI file. For details, see Load ERI.
- Enter the encryption keys manually (software FDE). For details, refer to Enter the encryption key manually.
- The following commands are the heart of the recovery application.
| Menu command | Details |
|
File |
Open ERI file Load ERI file from cache End |
|
Partition |
Repair VBR Decrypt drive InputKey Key Injection |
|
BootChain |
Repair UEFI (only for UEFI systems) Repair MBR (only for BIOS systems) Restore original MBR (only for BIOS systems) Set Active Partition Disable PBA load check |
|
Administration |
Set admin-password Collect log files |
|
TPM |
Activate Deactivate Rebind For details about TPM usage, see Chapter 3 ‘Trusted Platform Module’. |
|
Help |
About |
Workbench for standard hard disks
Each node in the left-hand pane has a self-explanatory label. When selected, the details about that node are displayed in the right-hand pane:
- Logical drives

The Logical Drive node displays the internal partitions/hard disks on the computer. The hard disk/partition icon can change according to the hard disk state:
| Icon | Meaning |
|---|---|
 |
Partition is encrypted and the disk encryption key (DEK) is available. |
 |
Partition is encrypted but the disk encryption key (DEK) is not available. |
 |
Hard disk is currently unlocked. |
 |
The hard disk has a problem or is in an undefined state. This icon appears if the Matrix42 Full Disk Encryption is not yet installed. |
The following information is displayed when a partition/hard disk is selected:
| Attribute | Values |
|---|---|
|
Partitionsize |
The size of the selected partition. |
|
Filesystem |
The format of the selected partition. |
|
Volume Label |
The name of the partition (if any). |
|
Physical Drive |
The index of the physical hard disk. The primary hard disk is indicated by the value 0. Any other value indicates a secondary hard disk. |
|
Startsector |
The sector on the hard disk that is first used to store data. |
|
Number of Sectors |
The total number of sectors on the selected partition. |
|
Partitiontype |
The file system used in the partition. 07h means NTFS, 95 is our own proprietary partition, and 0E is FAT32. |
|
Stalled Sector |
The sector on the hard disk that is last used to store data. |
|
Algorithm |
The algorithm is used to encrypt the partition. An algorithm will only be recognized if the partition was encrypted using Matrix42 Full Disk Encryption. |
|
Flags |
This is a bitmap that indicates if the drive is encrypted, partly encrypted or plain (last bit is set) and how it is encrypted. For instance, 601 means the drive is CBC encrypted. |
|
Encrypted |
0= partition is not encrypted 1= partition is encrypted |
- Security Boot Manager
This node displays the following boot manager information:
| Attribute | Values |
|---|---|
|
FDE-Partition |
This entry is visible twice in the list. The first entry states whether an FDE partition is available, the second if it is active (i.e. encrypted). |
|
KEK-Information |
This entry indicates if the structure where the keys are stored exists. |
|
FDE Bootstrap |
This entry indicates if the section where the FDE boot code is stored exists. |
|
PBA Bootstrap |
This entry indicates if the boot sector of the 95 Partition (Linux boot loader) exists. |
|
PBA loader |
This entry indicates if the 16-bit code is executed after the Linux PBA was finished. |
|
Real-Mode-PBA |
This entry indicates if the bootcode that starts Windows exists. |
|
16Bit-Algorithms |
This entry indicates if the 16-bitimplementation of the encryption algorithms exists. |
- Security Boot System PBA
This node displays the following PBA component information:
| Attribute | Values |
|---|---|
| Security Boot System PBA | A short message to inform whether the PBA components are installed. |
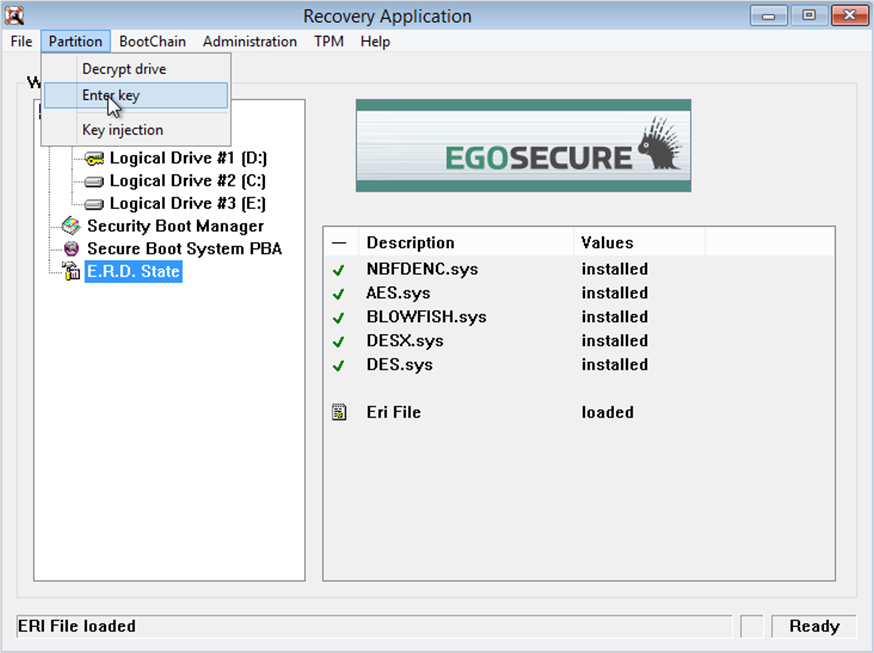
- ERD State

This node displays information about the encryption algorithms loaded into the environment as well as if an ERI file has been successfully loaded into the emergency recovery application. The following information is available:
| Attribute | Values |
|---|---|
|
NBFDENC.sys |
This entry indicates if the 32-Bit encryption driver for full-disk encryption exists. |
|
AES.sys, Blowfish.sys, DESX.sys, DES.sys |
These entries state whether each of the encryption components has been loaded by the emergency recovery application. |
|
ERI File |
This entry states whether the ERI file has been loaded into the emergency recovery application. |
Load ERI
Once the application is started, the next task you must perform is to load the ERI file into the emergency recovery application. The ERI file can be loaded from computer or emergency recovery information (ERI) can be loaded from cache.
Without loading an ERI file, none of the recovery functions are active.
Loading ERI file from computer
- Start the emergency recovery CD as stated in Start the emergency recovery application (GUI).
- Select the menu command File | Open ERI file.
- The Select ERI file dialog appears:

- The file explorer should automatically open the directory in which the relevant ERI file(s) are stored – providing that the creation of the ERD was performed according to Creating a WinPE emergency recovery boot CD or USB flash drive. If not, then use the following path: <ERD>\Programs\FIS\ERI\
- Select the correct ERI file and click Open. If you have stored the ERI file(s) on removable storage media (i.e. USB stick), then locate them there.
- If you protected the ERI file with a password during its creation, then you would now be prompted to enter the password.
- Once the password is entered, click OK.
- If the password is valid, the ERI file is loaded into the emergency recovery application.
- The main window reappears, confirming that the ERI file has been loaded:

Loading ERI from cache
ERI can be loaded from cache if the Cache emergency recovery information on disk option was checked before disk encryption. ERI file password is required.
- Start the emergency recovery CD as stated in Start the emergency recovery application (GUI).
- Select the menu command File | Load ERI from Cache.
- The Enter ERI Password dialog appears.
- Enter the password defined for the ERI file.
- Only the English keyboard layout is supported.
- Click OK.
Further tasks
Now that the ERI file is loaded you can continue to repair/recover the computer using the following methods:
- Decrypt a drive. For details, see Decrypt a drive.
- Update the master boot record (MBR). For details, see Repair MBR.
- Replace the Original MBR. For details, see Restore original MBR.
- Set the administration password. For details, see Set the administration password.
Entering the encryption key manually
If there is no ERI file available for the damaged computer, you have the option to enter the encryption keys manually. The keys used to encrypt each partition of the hard disk must be entered before you can use the emergency recovery application to decrypt any drive. Follow these steps to enter the encryption key(s):
- To activate all the recovery options in the recovery application, open an arbitrary ERI file via the Menu option File > Open ERI file (refer to Load ERI). It does not matter which ERI file is used – it can belong to any computer. If prompted, enter the password for the ERI file.
- Select the partition to decrypt from the Logical drives node in the left-hand pane of the main window. Subsequently, select the option Enter Key from the Partition menu:
- The Enter disk key dialog appears.

This dialog allows you to enter the encryption parameters set for the drive/partition in question.
The following options are available:
| GUI element | Details |
|---|---|
|
Algorithm |
Here you must select the algorithm that was used to encrypt the drive. |
|
Key length |
Some encryption algorithms support different key lengths. Use the slider to define the correct key length for the selected algorithm and partition. |
|
Key input |
Enter the encryption key password used for the partition into this field. Check Enter key in clear to make the password entry visible. |
- Once the information is entered, click OK. If the information is correct, it is loaded into the emergency recovery application.
- The ERD main window reappears. Repeat steps 2 and 3 for every encrypted partition you need to decrypt.
- Drive decryption can now be performed (see next section).
Decrypting a drive
This procedure can be used when you have either not decrypted the hard disk(s) before removing Matrix42 Full Disk Encryption or if the decryption of a hard disk was interrupted (due to power failure) and needs to be continued.
This procedure assumes that either a valid ERI file has been loaded or that the encryption key has been entered manually, and that the drive node has been selected.
Follow these steps to decrypt a partition/hard disk via the ERD:
- Make sure that you have loaded the correct ERI file via the Menu option File > Open ERI file (see Load ERI).
- Select the respective drive from the tree in the left-hand pane.
- Select the Decrypt drive option from the Partition menu.

- The Decrypt drive dialog appears.
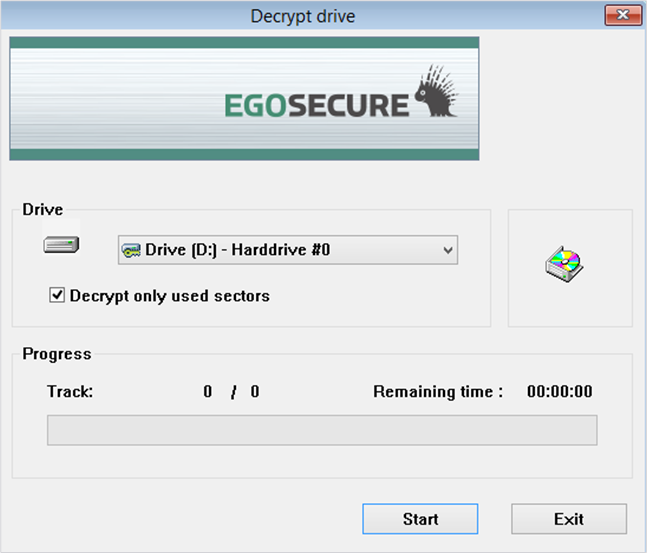
- From the Drive combo box, select a drive for decryption.
- Check the Decrypt only used sectors option to decrypt only those sectors of the selected drive that contain data. Leave this option unchecked to decrypt every sector (this will take longer).
- Click OK to begin the decryption.
Any loss of power during the decryption process may cause data corruption. The decryption of a hard disk may take some considerable time depending on the size of the disk and the speed of the computer.
Entering the encryption key from ERI file
Inject the encryption keys from an ERI file, the automatic comparison takes place to add only the keys of the any partition that has been encrypted by a previous FDE installation but is unavailable in the new one.
This procedure assumes that either a valid ERI file has been loaded or that the encryption key has been entered manually, and that the drive node has been selected.
- Make sure that you have loaded the correct ERI file via the Menu option File > Open ERI file (see Load ERI).
- Select the Key Injection option from the Partition menu

- The success message appears if encryption keys are encrypted.
- Click OK to close the message.
Decrypting a drive in a silent mode
To enable the decryption of a partition without using a graphical user interface you can use the emergency recovery console (pe_erd_console.exe) from within the WinPE 2.x boot CDs. This section details the console and the commands/options open to you.
Follow these steps to decrypt a drive from the ERD:
- Once you have booted the target computer using the WinPE ERD, open a command prompt window.
- Use the following commands to decrypt drives/partitions (case insensitive):
pe_erd_console.exe eripath=<?> eripwd=<?> partition=<?>
- The following options are available:
| Option | Details |
|---|---|
|
ERIPATH |
The path to the ERI file |
|
ERIPWD |
The password for the ERI file |
|
PARTITION |
The letter of the partition/hard disk to be decrypted |
|
/H |
Help – information about each option available in the console |
|
/L |
Load keys to memory |
For example:
pe_erd_console.exe eripwd=87654321 eripath=f:\fde.eri partition=d
pe_erd_console.exe eripwd=87654321 eripath=f:\fde.eri /L
During and until the decryption process is finished, a series of dots will appear in the command prompt. Depending on how large the partition is, the number of dots may scroll the command prompt – this is normal! If the decryption is finished successfully, the message ‘Hard disk was successfully decrypted’ appears. If the decryption is unsuccessful an error message will appear.
Repairing MBR
It may be necessary to update the MBR if your computer does not start after the installation of a third-party application. The most likely cause is that the installer has modified the MBR.
Follow these steps to update the MBR:
- Make sure that you have loaded the correct ERI file via the Menu option File > Open ERI file (see Load ERI).
- In the main window select the Menu option BootChain > Repair MBR. The Repair MBR dialog appears:
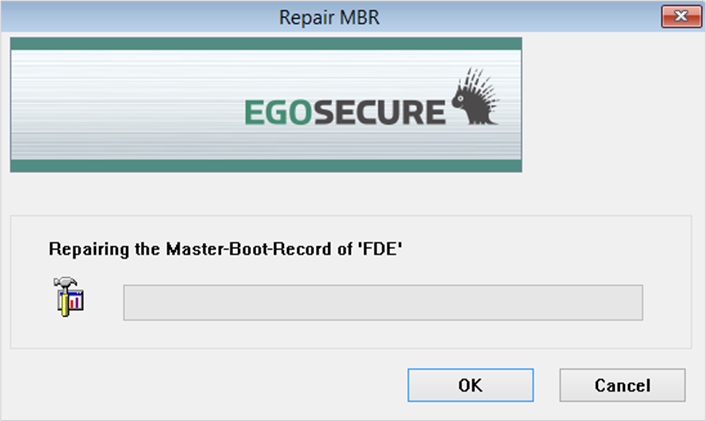
- Click OK to start the procedure.
- Once complete, the dialog will close automatically with no further prompting or interaction.
Restoring original MBR
This option replaces the Matrix42 MBR with the original MBR archived by Matrix42 during installation. Follow these steps to replace the Matrix42 MBR:
- Make sure that you have loaded the correct ERI file via the Menu option File > Open ERI file (see Load ERI).
- In the main window select the Menu option BootChain > Restore Original MBR.
- The MBR repair dialog appears:

- Once complete, the dialog will close automatically with no further prompting or interaction.
Setting active partition
This option allows the user to set an active partition for the MBR. The active partition becomes the boot sector for the MBR to load the boot program. Follow these steps to set active partition:
- Make sure that you have loaded the correct ERI file via the Menu option File > Open ERI file (see Load ERI).
- In the main window select the Menu option BootChain > Set active partition. The Set active partition dialog appears:

- Select the partition and click Set active.
- The selected partition becomes the active partition for the MBR.
Setting the administration password
Use this feature to set the Control Center administration password.
- In the main window select the menu option Administration > Set admin password.
- The Set admin password dialog appears.
- Enter and confirm a new password.
- Click OK.
- Once the password has been changed close the emergency recovery application (File > Exit).
- Click GO > Shut down > Restart to end this procedure and to restart the computer. Windows should boot as normal.