Installation Guide I: System Requirements
Silverback Server
Hardware
- 64 Bit CPU, 2.6 GHz Xeon or faster
- 8GB RAM
- 10GB of free disk space
- SCSI or SAS speed disks or equivalent SAS
- 1GB Network Interface Cards
Operating System
- Microsoft Windows Server 2016, 2019, 2022 or 2025
- The server must exist in the same LAN as the SQL Server. 10ms latency minimum is required to the SQL Server
- The same date and time as the Silverback SQL Database Server
- The server must be configured for English (United States) language, date and time settings (How-To)
- Executed Hardening Script for enabling and disabling appropriate for Protocols & Cipher
Roles and Features
Silverback requires the following Roles and Features:
Try our PowerShell script for Roles and Features Installation: Knowledge Base
| Windows Server 2025, 2022 | Windows Server 2019 | Windows Server 2016 | |
|---|---|---|---|
| Server Roles |
|
|
|
| Features |
|
|
|
|
Web Server Role (IIS) Role Services |
|
|
|
Additional Software
- Minimum installed Microsoft .NET Framework Runtime Version 4.7.2
Open File Explorer and Browse the following path: C:\Windows\Microsoft.NET\Framework, Enter the folder with the latest version – for example, v4.0.30319. and Right-click any of the ".dll" files and select the Properties option. Click the Details tab. Under the "Product version" section, confirm the version of .NET is not lower than 4.7.2
- Minimum installed ASP.NET Core Runtime Hosting Bundle Version 6.0.15
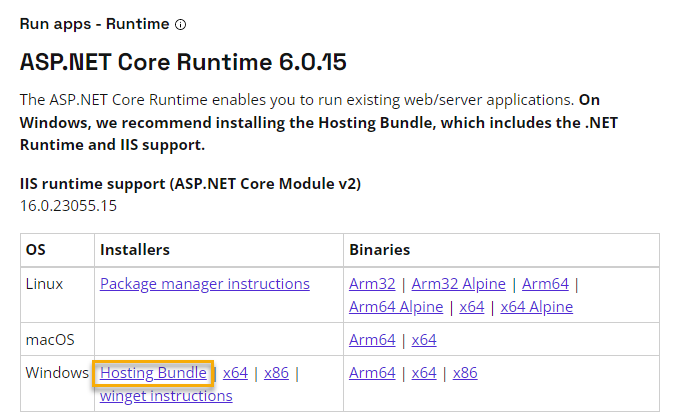
Ensure to install the ASP.NET Core Runtime Windows Hosting Bundle from the .NET Core Major Version 6.0. Newer versions, e.g. starting with 7.X.X are not supported.
Browsers
Access to Silverback for End Users, Help Desk and System Administrators is via a web-based console. Supported browsers are:
- Google Chrome (recommended)
- Mozilla Firefox
- Safari
- Microsoft Edge
- Internet Explorer 11
To provision a device, users must have access to the Silverback Self Service Portal. If a web proxy processes the user’s web traffic, then ensure the proxy server can serve the Self Service Portal. If this is not possible, proxy server exclusions must be set to allow direct access to the site.
Supported Devices
- Android 8.0 or higher
- iOS 12.0 or higher
- iPadOS 13.0 or higher
- tvOS 12.0 or higher
- Windows 11 21H2 or higher
- Windows 10 1803 or higher
- macOS Sierra or higher
- ChromeOS 69 or higher
Accounts & Groups
Accounts
The following accounts are needed:
| Type | Minimum Rights | Purpose | Required |
|---|---|---|---|
| Domain Account | Local Administrator | Install Silverback | mandatory |
| SQL Account |
db_creator Role db_owner Role |
Install Silverback Database with SQL Server Authentication Upgrade Silverback Database with SQL Server Authentication |
mandatory (for SQL Server) |
| Azure SQL Account |
db_owner Role |
Upgrade Silverback Database with SQL Server Authentication. Please refer to Contained user access for additional information |
mandatory (for Azure SQL) With Azure SQL, the database creation itself is not part of the Silverback installation and the database should be already present. |
| Service Account | Read permission to Active Directory | LDAP Lookups | optional |
Groups
The following groups are required. The Silverback Mobile Device Manager groups contains either the Active Directory Computer Object of the Silverback or Cloud Connector Server. The second Silverback Enterprise Device Management group contains the group Silverback Mobile Device Manager and consequently also the computer object of the Silverback or Cloud Connector server.
| Type | Name | Purpose | Included |
|---|---|---|---|
| Global Security Group | Silverback Mobile Device Manager |
Install Silverback Database with Windows Authentication Upgrade Silverback Database with Windows Authentication Certificate Distribution
|
For on-premise installations: SilverbackComputerAccount$ For cloud customers: CloudConnectorComputerAccount$ |
|
Domain local Security Group with delegated Read permissions to Active Directory |
Silverback Enterprise Device Management |
Install Silverback Database with Windows Authentication Update Silverback Database with Windows Authentication Certificate Distribution |
Silverback Mobile Device Manager Global Security Group |
SQL Server
Hardware
10GB of space per 1000 devices – This will change depending on individual requirements for logging and data retention.
Software
- SQL Server 2016 to 2022 or Azure SQL
For Azure SQL, ensure that the Database Name does not contain a "-".
- Database Compatibility Level must be 100 for SQL Server 2016 to 2022 and for Azure SQL 150
- This is set by the script on the Silverback database automatically
- Server/Instance collation must be either
- Windows Collation or
- Latin_General_CI_AS
- Latin1_General_CI_AS
- SQL Collation
- SQL_Latin_General_CP1_CI_AS
- SQL_Latin1_General_CP1_CI_AS
- Windows Collation or
- Database Collation must be set to:
- Latin1_General_CI_AS
- This is set by the script on the Silverback database automatically
SQL Account Permissions
Please review all SQL Account Permissions for On-Premise SQL and Azure SQL below:
Azure SQL
- User Account with db_owner permissions for database upgrades
- Please review Contained Database Users - Making Your Database Portable
- Please review Authorize database access to SQL Database, SQL Managed Instance, and Azure Synapse Analytics
SQL Server
- SQL Account with db_creator permissions to create the SQL Database
- SQL Account with db_owner permissions for database upgrades (optional)
You can downgrade your permissions from db_creator to db_owner after the initial Silverback installation.
Database
Silverback will create and configure its database during the Installation.
The following values can be specified.
- Use Azure SQL
- Data Server Address
- Failover Database Server Address
- Database Name
- Authentication Method
- Username
- Password
For an Azure SQL hosted database, ensure that your Silverback Server is able to establish a remote connection to the cloud hosted database.
Firewall Rules
| Source (from) | Destination (to) | Port Protocol |
|---|---|---|
| General | ||
| Silverback Server | SQL Server or Azure SQL | 1433/tcp |
| Silverback Server | Domain Controller | 389,636/tcp |
| Silverback Server | Certification Authority | 389,443/tcp |
| Silverback Server | Certification Authority | Random Port above 1023 /tcp (DCOM/RPC) |
| Silverback Server | Exchange Server (for Exchange Protection) | 443/tcp, 5985/tcp |
| Reverse Proxy | Silverback Server | 443/tcp |
| Devices | Silverback Server or Reverse Proxy | 443/tcp |
| SMTP | ||
| Silverback Server | SMTP Server / Provider | 25/tcp |
| Silverback Server | SMTP Server / Provider | 587/tcp |
| Apple | ||
| Silverback Server | Addressblock: 17.0.0.0/8 (internet) | 443/tcp, 2195/tcp |
| Silverback Server | api.push.apple.com | 443/tcp |
| Silverback Server | mdmenrollment.apple.com | 443/tcp, 2195/tcp |
| Silverback Server | vpp.itunes.apple.com | 443/tcp, 2195/tcp, |
| Silverback Server | itunes.apple.com | 443/tcp, 80/tcp |
| Devices | Addressblock: 17.0.0.0/8 (internet) | 5223/tcp |
| Devices | api.push.apple.com | 443/tcp |
| For additional information, see Use Apple products on enterprise networks and TCP and UDP ports used by Apple software products | ||
| Google Android Enterprise | ||
| Silverback Server | Please review Android Enterprise Network Requirements for Consoles. | 443/tcp, 5228/tcp , 5229/tcp, 5230/tcp |
| Devices | Please review Android Enterprise Network Requirements for Devices | 443/tcp, 5228/tcp , 5229/tcp, 5230/tcp |
| For additional information, see Android Enterprise Network Requirements and FCM Ports and your firewall | ||
| Samsung | ||
| Devices (Global Load Balancers) | gslb.secb2b.com (EMEA & America) china-gslb.secb2b.com.cn (China) |
443/tcp |
| Devices (Knox License Management) | eu-prod-klm.secb2b.com (EMEA) eu-prod-klm-b2c.secb2b.com (EMEA) us-prod-klm.secb2b.com (America) china-gslb.secb2b.com.cn (China) china-b2c-klm.secb2b.com.cn (China) |
443/tcp |
| For additional information, see KME Firewall exceptions | ||
| Matrix42 | ||
| Silverback Server | mobile.matrix42.com | 443/tcp |
| Silverback Server | accounts.matrix42.com | 443/tcp |
| Silverback Server | pa.cloud.matrix42.com | 443/tcp |
| Microsoft | ||
| Silverback Server | *.wns.windows.com | 443/tcp |
| Silverback Server | *.notify.windows.com | 443/tcp |
| Silverback Server | login.live.com | 443/tcp |
| Devices | *.wns.windows.com | 443/tcp |
| Devices | *.notify.windows.com | 443/tcp |
| Devices | login.live.com | 443/tcp |
| For additional information, see Enterprise Firewall Configurations to Support WNS Traffic | ||
| SMS Provider | ||
| Silverback Server | rest.messagebird.com apiaerialink.net secure.redcoal.net |
443/tcp |
Servers & Network
Bandwidth
We recommend at least 100Mbps network connections, with latency under 10ms between all internal systems
Domain and Forest Level
- Silverback support the following Domain and Forest Level:
- Windows Server 2003
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012 R2
- Windows Server 2016
DNS
As Silverback requires devices to connect via DNS, appropriate DNS entries must be setup for your server.
DNS Name
- Internally and externally the DNS name must be the same, so devices can resolve the server address inside your network and outside.
- A forwarding from an external DNS name to a different internal name will result in an invalid request message from the Secure Token Service.
- For example: silverback.imagoverum.com
Android & Companion
For Android Based devices, a DNS SRV record lookup is performed to find the server based on the username entered in the client. If the user enters e.g. tim.tober@imagoverum.com , then a SRV service record lookup is performed against “imagoverum.com” for the _silverback SRV record.
The SRV record should be setup like this:
| Service | _silverback |
|---|---|
| Protocol | _tcp |
| Priority | 0 |
| Weight | 0 |
| Port Number | 443 |
| Target or Service Hoster | e.g. silverback.imagoverum.com |
Windows 10/11
For user initiated enrollments through the Self Service Portal, an internal and a public Alias for the Enterprise Enrollment should be set to target your Silverback Server. This will prevent to enter the Silverback Server Address manually through the Enrollment Process.
| Type | Alias (CNAME) |
|---|---|
| Fully qualified domain name (FQDN) | e.g. EnterpriseEnrollment.imagoverum.com |
| Fully qualified domain name (FQDN) for target host | e.g. silverback.imagoverum.com |
SSL
Silverback utilizes device management protocols that require an established trust relationship between the device and server. This allows the server to provision and manage your mobile fleet securely. The Silverback web service requires a certificate signed by a Certificate Authority trusted by the devices. The certificate must also match the DNS Name outlined in Section DNS Setup. The Silverback Website Certificate is a core requirement for Silverback to function, please have the PFX/P12 Certificate Bundle available for the installation.
A full list of iOS trusted Certificate Authorities is available at: http://support.apple.com/kb/HT5012.
Web Proxy
Silverback is web based. Take it into consideration if there are any corporate web proxies in your network. If your end users are using a web proxy to browse the internet, then an appropriate configuration is needed to allow Silverback to function effectively:
- Ensure that each web browser (that has a proxy set) has an exclusion set for the Silverback server URL outlined in section DNS Setup.
- Configure each web proxy to allow traffic destined for the Silverback server to reach its destination unaltered.
- Ensure that any devices connected to Wi-Fi have access to the Apple push network, as outlined in Firewall Rules.
- Ensure that any Android devices enrolled in Silverback are able to access FCM, as outlined in Firewall Rules.
Reverse Proxy
If you are utilizing a reverse proxy, it is important to pass through the Client Request Headers, so that the backend can process the client. Additionally you need to ensure that the certificate chain is completed and fully trusted. As an example on the Sophos UTM Web Application it is required to enable the control "Pass host header" under the advanced configuration and to upload each trusted certificate from the trusted certificate chain in a *.pem format to the Certificate Authority section. If you are using the Microsoft Web Application Proxy publish a new Web Application with a Pass-through configuration.
Use the DigiCert® SSL Installation Diagnostics Tool to perform a SSL Certificate Check and validate the TLS chain.
SMTP
Silverback will notify administrators about key events in the system if configured to do so. The SMTP Server details are required for alerts. The SMTP Server must allow anonymous relay within the company domain.
Active Sync
Silverback is used to manage deployment of Exchange ActiveSync client configurations. Ensure your Exchange ActiveSync is currently configured and in a working state.