UEM Patch and Vulnerabilities
UEM Patch & Vulnerabilities
Patch Management information from Empirum is greatly enhanced and allows users to easily get the information they need to assess new patches and their vulnerabilities based on the great data navigation and dashboard capabilities of the ESM platform.
Acronyms and external resources
Some data is related to information based on external databases and services.
- CVE: Common Vulnerabilities and Exposures. The mission of the CVE™ Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
- CVSS: Common Vulnerability Scoring System. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities.
- VRR: Vulnerability Risk Rating . Vulnerability Risk Rating (VRR) considers industry-standard Common Vulnerability Scoring System (CVSS), Common Weakness Enumeration (CWE) data, OWASP (Open Web Application Security Project), open-source threat intelligence, subject matter expertise, trending information, and more. VRR represents the risk posed by a given vulnerability, provided as a numerical score between 0 and 10, to an organization or business. The higher the risk, the higher the VRR.
- KB Number: Knowledge Base article. (also known as Q-number). Vendor specific information about patches.
- Bulletin ID: Vendor information on security related issues.
- Patch Type: All patches are categorized by the following criteria:
-
Security Patches
-
Security Tools
-
Non-security Patches
-
- Severity: Rating of the severity:
-
Critical: A vulnerability whose exploitation could allow the propagation of an Internet worm without user action.
-
Important: A vulnerability whose exploitation could result in compromise of the confidentiality, integrity, or availability of users' data, or of the integrity or availability of processing resources.
-
Moderate: Exploitability is mitigated to a significant degree by factors such as default configuration, auditing, or difficulty of exploitation.
-
Low: A vulnerability whose exploitation is extremely difficult, or whose impact is minimal.
-
Product architecture
The Patch & Vulnerability information visualized in the UEM extension is based on two main sources:
- Matrix42 Patch Catalog data. The catalog data is retrieved from an external API and contains information on patches including related information like bulletin data, CVE data, CVSS and VRR scorings. This information is initially transferred when activating the Patch & Vulnerabilities and updated on a daily base. The first import might take very long as the patch catalog contains information on more than 500.000 patches. The following updates are delta updates and therefore much faster.
- Computer Patch Status data. Empirum sends the patch status of each computer via the Enterprise Service Bus whenever the data is updated from a patch scan or fix run on the computer. Empirum sends from version 25.4 onwards the patch status details via Enterprise Service Bus (ESB). Earlier versions just sent base information without any details on the installed or missing patches.
Activating Patch & Vulnerabilities
The import of patches is deactivated by default and needs to be enabled if you want to use feature to its full extent.
UUX for UEM
- The synchronization of the patch catalog is only performed if the attached Empirum system has a valid Patch Management license and is 25.0.0 or newer. You can check this in the node information in Administration -> Integration -> Enterprise Service Bus -> Nodes -> Empirum node

- To enable the initial catalog sync and a daily update the engine activation needs to be activated:
- Go to Administration -> Services & Processes -> Engine Activations
- Select "Edit" on the preview of "UEM Device Patch Management Synchronizer Activation"
- Activate the engine by un-checking "Disable entire Activation"
The patch catalog is downloaded directly from the partner server. Make sure the following URLs are allowed to be accessed from the ESMP server.
The initial synchronization will take long as the amount of data is big. Subsequent synchronizations will be performed by using the delta and will not impact the performance.
Empirum Patch Data Sync
Empirum sends from version 25.4 onwards the patch status details via Enterprise Service Bus (ESB). Earlier versions just sent base information without any details on the installed or missing patches. See the section Deactivating the extended Patch Status Messages from Empirum if you want to stick with the overview patch information to reduce load and data transfer.
Automated Patch Catalog Download
When activated the patch catalog is imported on a nightly schedule. Please adjust the schedule so the system is not performing a lot of parallel imports from other systems at the same time. The synchronization of the patch catalog is only performed if the attached Empirum system has a valid Patch Management license and is 25.0.0 or newer (see UUX for UEM). The initial synchronization will take long as the amount of data is big. Subsequent synchronizations will be performed by using the delta and will not impact the performance.
Features
- Patch & Vulnerability Dashboard with insights on patch runs, device patch states and Windows versions
- Automatically synchronize the Patch catalog with patch details, associated bulletins and CVE numbers
- List of all patches, service Packs and bulletins including information about vulnerability scorings
- List of patch state of computers
- Update of the computer patch state with every patch scan and fix run sent from Empirum
- Detect if the connected Empirum system has a valid Patch Management license
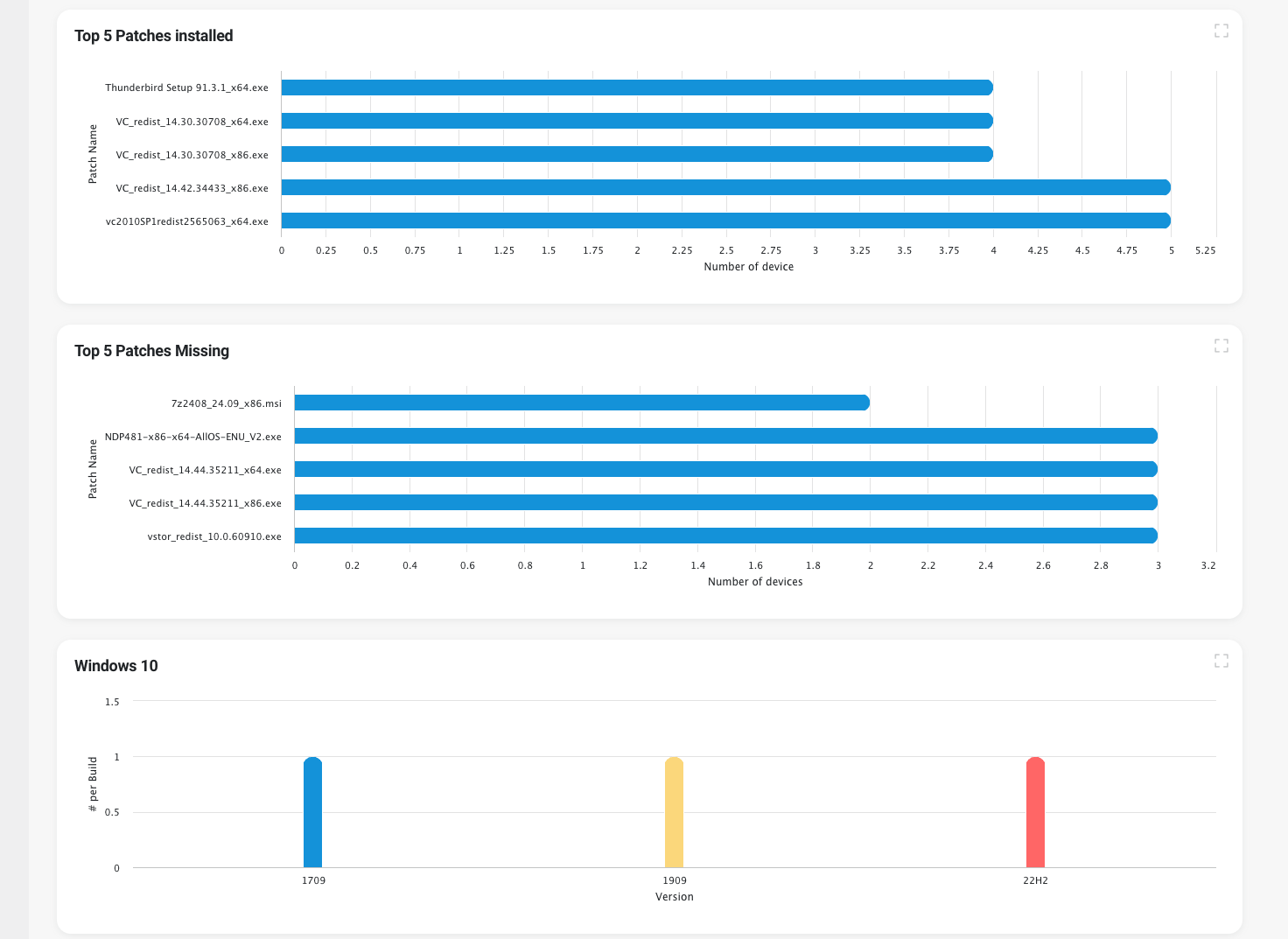
Patch & Vulnerabilities Dashboard
The new dashboard provides an initial overview on the patch state. Based on the dashboard capabilities of the ESMP it can be configured and new widgets can be added.
It is possible to switch back to the original Patch Management dashboard by using the option "Switch to Classic Dashboard"
Select in the UEM Extension: Patch & Vulnerabilities

List of all patches and bulletins
The list shows all available Bulletins. The preview allows to drill down to the associated patches and the vendor information (external link)
Using the grouping feature on Vendor, Family and Version provides a hierarchical view which is easy to navigate.
Bulletin List

Patch List

The patch list shows all patches and the associated products, vendors and bulletins.
Quick filters allow to filter for criticality based on CVSS and VRR scores. Red = 7.0 or higher, 4 - 6.9 is yellow and below is green.
CVSS and VRR numbers 7 or higher are colored in red.
Patches use an internal KB number for reference. This number is not the same KB Number provided by Microsoft but is related to it for Microsoft patches.
To search for a KB Number provided by Microsoft use the internal KB Number and replace the Q with the numbers of the MS KB Article.
Patch Preview
The patch preview shows all details of a patch. If one or CVE are related to the patch the number is shown and can be used as a link to the external CVE database.

List of patch state of computers
The patch state of computers is sent from Empirum with every patch can or fix run. It uses the Enterprise Service Bus. The list shows all patch states as individual entries with the state (Missing or Installed) and if it is assigned in Empirum via a patch group to the computer. The preview allows the drill down to the patch or computer.

Deactivating the extended Patch Status Messages from Empirum
In Empirum 25.0.0 and 25.0.1 the extended status messages are disabled by default. From Empirum 25.4 onwards the extended messages are enabled by default.
- To de-activate sending of the Empirum patch status messages via Service Bus the feature need to be enabled in the database:
- Run on the Empirum DB "update Options set EmpValue = 1 where EmpOption = 'UemDevicePmScanResultSkipActivated'"
- Customers using the Matrix42 Cloud offering need to send an inquiry to enable the preview to Matrix42 support.