Installation
Full Disk Encryption Installation
This section details how to install Matrix42 Full Disk Encryption either manually, or via the Matrix42 Data Protection Console.
Before you start
Please ensure that the following conditions are met before you install Matrix42 Full Disk Encryption:
- Run CHKDSK/f on all the drives you wish to encrypt. This will check the hard disk and the file system for errors and if necessary, correct them.
- Check if the AHCI mode rather than legacy mode is enabled on in BIOS. If you want to use AHCI, Matrix42 recommends using the standard Microsoft default driver.
- Check if the target computer meets the installation requirements.
In addition to the above, the following tasks must be performed:
- If the hard disk has been encrypted by a product other than Matrix42 Full Disk Encryption, decrypt the hard disk and remove the encryption application. This will avoid conflicts between the applications and close any possible security holes that may be opened when using two applications.
Be aware that one reboot is necessary after the installation of the FDE component. This is because the installer creates a small partition on which the PBA component is installed and it is necessary to let Windows check the disk (CHKDSK) BEFORE initializing the PBA component on this small partition. Optionally, further reboot is necessary after the initialization of the PBA component to capture user credentials (this does not apply if you either enter user credentials or certificates directly into the PBA component, or pass credentials onto the PBA component via an initialization policy).
Installation overview
The first installer will place an integrated FDE mechanism to the hard disk as well as a hardened Linux-based PBA system to a specific, new partition on the hard disk. Once running, Matrix42 Full Disk Encryption will boot to this system first and will prompt for authentication. If successful, the computer will automatically boot to Windows and use the SSO method to authenticate the user to Windows with no further need to enter credentials.
Matrix42 Full Disk Encryption is delivered in several languages and you can install any of them on a computer that has a different keyboard layout, i.e. the English version can be installed on a computer with a German keyboard layout.
Caution is needed when either connecting an external keyboard that has a different layout, or when deploying Matrix42 Full Disk Encryption to computers that have a different keyboard layout to that on which the deployment policies have been created.
Bear in mind that when defining passwords, the keyboard layout used to define the password may differ from the keyboard layout used at a later date (special characters have keys/key combinations that differ - for example, a QWERTZ keyboard layout differs greatly from a QWERTY keyboard layout).
Customizing
This section details how to customize the setup in preparation for rollout. There are two main ways to customize the MSI package:
- If you intend to rollout to multiple hardware configurations, we recommend that you test each configuration for compatibility beforehand. This enables you to locate any configuration that Matrix42 does not support using the standard setup and allows you to test alternative setups using ‘Hardware Compatibility Mode’ or an alternative bootloader. For further information, see Installation options for FDE.
- The PBA component can also be customized with an individual background image and company-specific HelpDesk texts. For further information, see PBA customization.
Installation options for FDE
To provide system administrators with methods of installing Matrix42 Full Disk Encryption successfully on the new and legacy hardware several new mechanisms have been implemented. There is no absolute guide as to which mechanism should be used on which computer. The standard mechanism will work on most computers, but there are some computers that need help. The mechanisms available are:
- Hardware compatibility mode (DMI config)
As of Matrix42 Full Disk Encryption ‘Hardware compatibility mode’ is available. This allows a system administrator to use two alternative methods of booting from the PBA to Windows. This means that it is possible to identify computers on which the standard method does not work, test the alternatives, and incorporate the details for such computers into the rollout package for automatic identification.
For further information, see Matrix42 FDE - Administration and Usage Guide.
- Alternative bootloader
An even smaller number of computers may need an alternative bootloader to boot correctly.
PBA customization
This section details how to customize Matrix42 Full Disk Encryption to:
- Incorporate a PBA new background;
- Incorporate new Matrix42 Full Disk Encryption PBA HelpDesk texts.
- Rebranding mechanism for OEM use implemented. The customization detailed in this section is a subset of the rebranding mechanism.
If you are a customer with an interest in rebranding Matrix42 as an OEM version, then please contact your nearest Matrix42 representative for further details. The customizing mechanism is a simple one. The file ‘fsebrand.bin’ must be placed in the same directory as the Matrix42 Full Disk Encryption MSI package before the installation starts.
Failure to place the fsebrand.bin file in the same directory as the Matrix42 Full Disk Encryption msi package will result in the Matrix42 Full Disk Encryption background and standard HelpDesk texts being installed to the end-user computer. It is not possible to enter a remote location for the fsebrand.bin file via the command line!
- Locate and open the file fsebrand.bin located in the Customizing directory. The fsebrand.bin file is actually a ZIP file that has had the extension renamed to *.bin. To open the file either open the file directly using an intelligent ZIP/archiving application or rename the extension from *.bin to *.zip and then open it using your archiving utility of choice.
- Unpack the contents of the file to produce the directory fsebrand.
- The fsebrand directory contains the following files needed to rebrand Matrix42 Full Disk Encryption:
| Directory / File | Details |
|---|---|
|
PBA customization files |
The following file is used to rebrand the default PBA background image: pba_bkgd_image.png(800x600 pixels) NOTE: If the picture size does not match the above mentioned standard size (pixels), FDE will scale down the original size to standard size. |
|
Country-specific directories identified by an RFC 1766 identifier (i.e. en_US) |
Each directory contains the following file: helpdesk_snb.txt HelpDesk text message file for the PBA HelpDesk. |
-
Edit the default message in the HelpDesk file helpdesk_snb.txt in each of the languages you wish to use, as well as the background image.
To display the HelpDesk correctly in the PBA component, the HelpDesk file must be saved using the following formatting information (it is recommended to use a text editor such as UltraEdit for this):
- Unix terminators-LF
- UTF-8 encoding
- Once finished, select all the files and directories in the fsebrand directory and re-zip them. Rename the resulting file to fsebrand.bin. The customization is now complete
Make sure that you re-zip the files and directories directly IN the fsebrand directory and NOT the fsebrand directory itself. This is because the installation mechanism expects to find the rebranded files directly in the fsebrand.bin file and not within another directory inside it.
Manual Installation
This section details how to install the Matrix42 Full Disk Encryption on standard hard disks. No hard disk encryption is started during the initial installation. This enables easy recovery should anything go wrong during the installation. Encrypt the hard disk only when you see that the PBA has installed and initialized correctly, and you have successfully authenticated to the Matrix42 Full Disk Encryption PBA at least once. If everything is all right, then you can encrypt the hard disk. For further information, refer to Matrix42 FDE - Administration and Usage Guide. Be aware that one reboot is necessary after the installation of the FDE component. This is because the installer creates a small partition on which the PBA component is installed and it is necessary to let Windows check the disk (CHKDSK) BEFORE initializing the PBA component on this small partition. An optional further reboot is necessary after the initialization of the PBA component to capture user credentials (this does not apply if you either enter user credentials or certificates directly into the PBA component, or pass credentials onto the PBA component via an initialization policy).
The FDE installation requires a user account with administrator privileges. By default, the security feature “User Account Control (UAC)” is enabled. This means that it will be necessary to confirm any such dialogs throughout the installation..
Installation of Full Disk Encryption components
- Double-click the executable file Matrix42 FDE by Matrix42 Setup.exe.
- The GUI language will be automatically selected by the installer to fit that of the operating system. If you have an operating system other than English, German, the default language – English – will be installed.
- A warning message appears if standby is enabled on the computer.
- Read the warning carefully and click OK to continue.

- The Welcome dialog appears.
- Click Next to proceed with the next step.

- The License Agreement dialog appears.
- Select I accept the terms in the License Agreement, and then press Next to continue.

- The Data Backup dialog appears.
- Read the warning carefully, and if you have not already done so, click Cancel, create a backup of your data before restarting the installation. Press Next to continue.

- The Setup Type dialog appears. This dialog allows you to choose which Matrix42 components should be installed.
- Click Complete to install all the features. The easiest way to secure your computer. This also requires the most disk space (approximately 200MB). If you select this option, go directly to the next step.
- Note: The Complete mode will not install “Recovery Tools” of the Matrix42 package.
- Click Custom to select which features will be installed. This is recommended for advanced users only! This dialog allows you to perform the following tasks:

- Context menu for specific component selection:
- If you want to select/re-select a component for installation, click the hard drive icon next to the component and select either Will be installed on local hard drive or Entire feature will be installed on local hard drive from the context menu.
- If you want to prevent the installation of a component, select Entire feature will be unavailable from the context menu.
- The following components can be installed:
- FDE: The Full Disk Encryption components (base components).
- PBA: The PBA component (optional component).
- TPM Support: Support for Trusted Platform Module (optional component).
- Control Panel: This refers only to the Matrix42 Full Disk Encryption Control Center plugin for the Windows control panel.
- Policy Builder: Install the Policy builder components.
- Report API: Install support for status information retrieval via third-party applications (not recommended).
- Recovery Tools: This allows installing the recovery tools (PE ERD, Secure Erase and Secure Wipe).
- To return to the default selection click Reset.
- Once you have made your selection click Next.
- The Select Initialization Type dialog appears. This dialog allows for selecting the following types of initialization:
| Initialization type / Option | Option / details |
|---|---|
|
PBA initialization options |
|
|
FDE initialization options |
|

- If this is an initial installation and you want to manually install, initialize, and configure Matrix42 Full Disk Encryption in one procedure, it is recommended to check the option Use default settings for both FDE and PBA. Locate and open the necessary policy files.
- If you want to install and initialize the FDE and/or the PBA components according to settings in pre-defined policies, check the option Use policy file. Continue with the next step (the dialogs prompting for the location of the policy files will appear after the main components have been installed).
- If you want to initialize and configure Matrix42 Full Disk Encryption at a later date, check the option Do not initialize for both FDE and PBA. Continue with Locate and open the necessary policy files.
- Once you have made a selection, click Next to continue.
- If you have selected the Use policy file option in the previous step, then the following dialog appears in sequence prompting you to locate the respective policy file for the FDE (*.nbs) and PBA (*.pba) components:

- Locate and open the necessary policy files.
- The Complete Installation dialog appears.
- Click Install.
- The Installation Status and Installation Complete dialogs will appear.
- Click Finish.
- The installer finishes here. The FDE initialization starts automatically, and once successfully completed the Operation was successful dialog appears.
When you restart the computer, it will boot to the Windows logon dialog as normal. Log on as normal. The Windows desktop will not appear for a couple of minutes because the PBA component is being initialized. Your computer has not crashed! Please be patient and let the process finish. You will be taken to the desktop as soon as the PBA component has been initialized.
- If you have selected to use policy file-based initialization for just the FDE component, continue with the next step to initialize the PBA component (refer to the dialog and notes above). The setup finishes here.
- If you have selected to use policy file-based initialization for just the PBA component, continue with the next step.
- The Complete Installation dialog appears. Click Install to begin installing files.

- The Installation Status dialog appears. Please wait while Matrix42 is installed. This may take several minutes.

-
If the installation is successful, the following dialog appears:

- The initial part of the installation is now complete.
- If you have selected Use default settings for both FDE and PBA components in step 6, the initialization and configuration will now continue. Continue with Installing Boot Security.
- If you have selected Do not initialize for both FDE and PBA in step 6, you can initialize the FDE and PBA components via the Control Center at a later date. The installer finishes here.
Installing Boot Security (initializing FDE)
- If Use default settings for the FDE component was selected in step 6, the following dialog appears. If a disk is encrypted with BitLocker, the dialog displays a warning that BitLocker protection will be disabled till the moment FDE initialization finishes (reboot included).
- Click Next to continue.
- The Administration Password dialog appears:

- Use this dialog to define the administration password for Matrix42 Full Disk Encryption and to define the location for the installation log file. This password will be required for every administrative action after Matrix42 Full Disk Encryption has been configured and running. You will also need this password to install and configure the PBA component after the computer has been restarted (providing you have chosen to install it).
- Click Next to continue.
Keep the administration password in a secure location.
- The step for hiding an encryption tray icon appears.
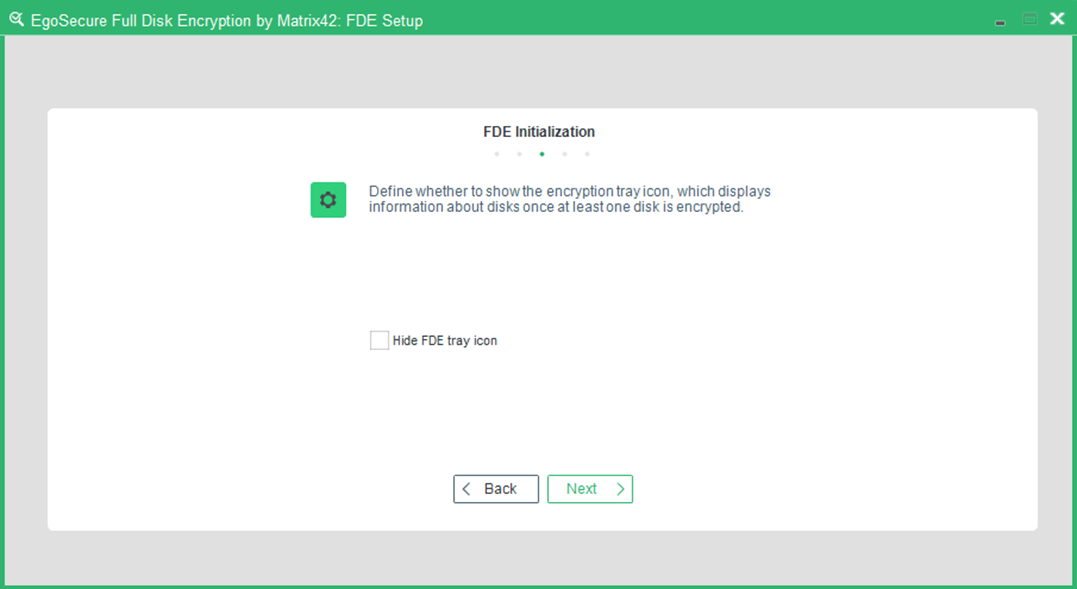
- By default, the encryption tray appears on the Windows taskbar once a disk is encrypted and shows information about the state of all disks on a computer. To hide the icon, check the Hide FDE tray icon box and click Next.
- The step for configuring additional encryption key protection appears.

Enable an additional layer of security to the disk encryption key (DEK). The HKEK option utilizes unique hardware-based information from the client to generate an additional hardware-based key encryption key (HKEK). The TKEK option uses unique TPM information from the client for generating a TPM-based key encryption key (TKEK). Check TPM system requirements before enabling the option. The options protect against moving the encrypted drive into another computer within the same network, where the same KEK is used. You can use both options at a time for the protection.
Before updating BIOS or replacing hardware When updating BIOS or replacing hardware, the information used for key generation changes and disk recovery will no longer be possible. That is why, please, follow the steps below to avoid it:
- Decrypt the disk.
- Update BIOS or replace hardware.
- Encrypt the disk.
System requirements for computers with TKEK
- UEFI systems starting with Windows 10 and later
- TPM devices with specification version 2.0 are supported only
- TPM must implement the following set of commands:
- TPM2_CreatePrimary
- TPM2_Create
- TPM2_Load
- TPM2_EvictControl
- TPM2_FlushContext
- TPM2_GetRandom
- TPM2_RSA_Encrypt
- TPM2_RSA_Decrypt
- TPM2_ObjectChangeAuth
- TPM must support the following set of algorithms:
- TPM_ALG_SHA256
- TPM_ALG_RSA
- TPM_ALG_OAEP
- TPM_ALG_AES
- TPM_ALG_CFB
- TPM device must be in the Ready state.
To proceed with the setup, perform the following:
- Enable the Generate hardware-based key encryption key (HKEK) option and/or Generate TPM-based key encryption key (TKEK), and then click Next.
- The following dialogs appear if Switch to expert mode option was selected in the previous step.
- Check Use alternate loader if PBA loading with current motherboard failed and you are now reinitializing FDE or your motherboard is considered as an old one.

- The dialog, which informs, whether there is enough free disk space to install the PBA partition appears. You cannot use this dialog to select a partition for repartitioning –the free space available will be used to create new PBA Linux partition.
- Select any of the drives, and click Next.
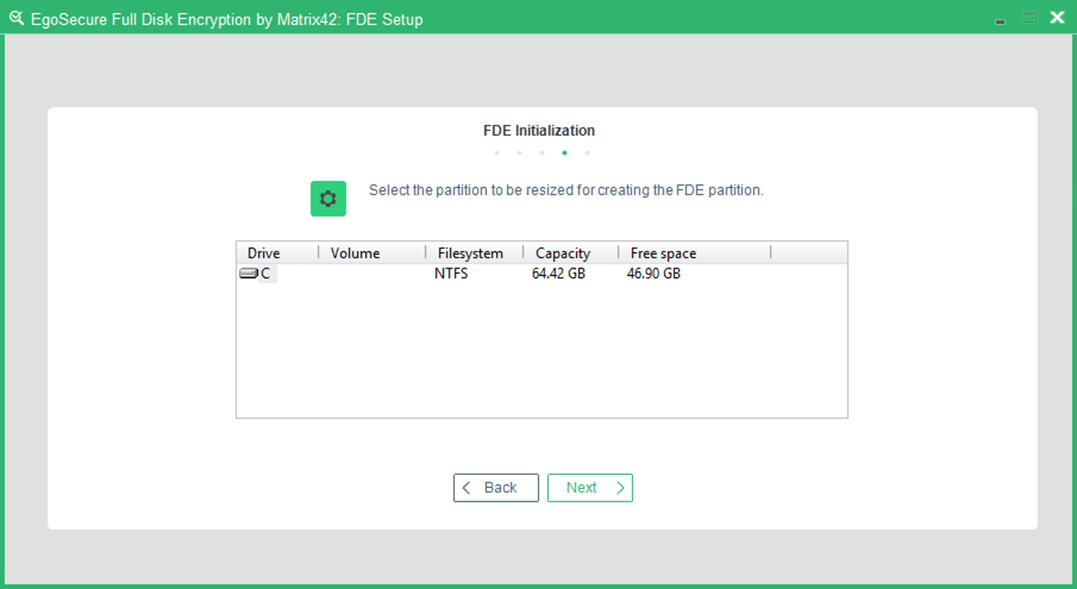
- The selected partition will be cut to 500MB disk space for creating PBA Linux partition.
- The Finish Initialization dialog appears. The configuration parameters for FDE are now set.
- Click Finish to install the FDE component.

- If you selected to prepare the hard disk for FDE initialization, repartitioning is a complicated process and may take a few minutes to complete.
- Once the initialization has finished, the following dialog appears:

- The installation and initialization of the Matrix42 Full Disk Encryption component is now complete. You have also activated the configuration procedure for the PBA component – ready to be configured after you reboot the computer.
- Click Yes to automatically reboot the computer and refer to the next step to guide you through the initialization of PBA.
This reboot is absolutely necessary after the initialization of the FDE component. This is because the installer creates a small partition and it is necessary to let Windows check the disk (CHKDSK) BEFORE installing or initializing the PBA component on this small partition.
Windows may prompt you to check the integrity of the hard disk after the computer has been restarted (CHKDSK utility). This is normal! Let Windows perform this check. Once the check is finished, Windows boots as usual.
Configuring PBA components
- Once a computer is rebooted after FDE initialization and log on to Windows is performed as usually, the configuration of the PBA component starts. You will be prompted to enter the Matrix42 Full Disk Encryption administration password defined before.

- Enter the password and click OK. Click Cancel if you do not want to initialize the PBA component at this time. The PBA Setup welcome dialog appears.
- This wizard will guide you through the steps necessary to configure PBA for secure authentication and sign-on. Click Next to continue.

- The Authentication method dialog appears.
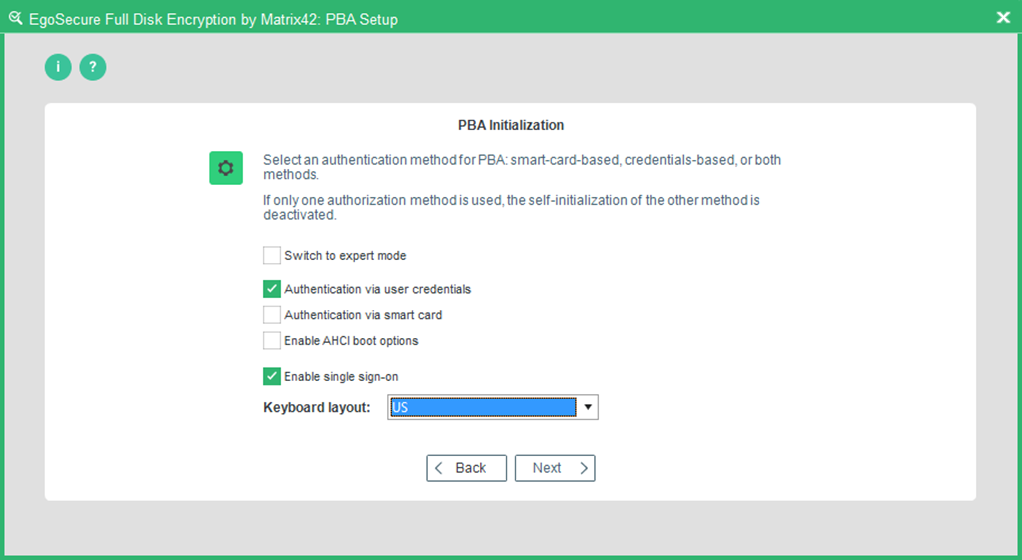
This dialog allows for selecting the authentication method and keyboard layout for PBA. Please select whether you want to use smart card, user ID/password, or both authentication methods. You can also choose to activate SSO for user ID/password authentication.
The following options are available:
| Option | Details |
|---|---|
|
Switch to expert mode |
Check this option if you want to configure further PBA options in this wizard (If you did not select this option, the wizard only displays the Finish button - in this case you will end up at step 13). |
|
Authentication via user credentials |
Check this option if you want to implement the user ID/password (Windows credentials) authentication method. The password for PBA must be no longer than 32 symbols. |
|
Authentication via smart card |
Check this option if you want to implement the smart card authentication method (If this option is not selected, the wizard will redirect you to step 5). |
|
Enable AHCI boot options |
This option will be enabled only if the BIOS is set to AHCI-mode: It gives you the possibility to easily test and use an alternative PBA configuration that could improve hardware compatibility (KICKSTART=KEXEC and Kernel parameter: AHCI-to-legacy). There is no guarantee that this option will resolve all hardware compatibility issues or the PBA boots up after that. The mechanism used here is Dmiconfig (refer to Matrix42 FDE - Administration and Usage Guide). Using this option creates a dmi.ini for the current hardware platform with the configuration stated above. If there is already an existing dmi.ini file, the user may be asked to overwrite it. |
|
Enable single sign-on |
Check this option if you want to activate the SSO method for smart card or user ID/password-based authentication. |
|
Keyboard layout |
Select the keyboard layout of the target computer to be used for PBA. Keyboard layout for text-based and graphical Simple PBA (UEFI): only German and English layouts are supported. Directly in the mode, language switch is available only in graphical Simple PBA. Keyboard layout for text-based Simple PBA (BIOS): only English layout is supported. |
- Once you have made your selection click Next to continue (or Finish if you did not select Switch to expert mode in which case you will end up at step 13).
- In case you did not select Authentication via smart card, then proceed to step 5.
- The Smart card reader/provider dialog appears if Switch to expert mode and Authentication via smart card options have been selected.

- Use the following options to determine the smart card reader and provider:
| Option | Details |
|---|---|
|
Select smart card reader
|
Select the card reader you want to use for PBA from the drop-down list. Selecting a specific card reader vendor will decrease the amount of time it takes the computer to start; selecting Automatically detect card reader will increase the startup time because all the CCID-compliant readers contained in the generic CCID bundle delivered with Linux will be scanned until the correct one is found. NOTE: The Linux CCID bundle used in this version of Matrix42 Full Disk Encryption is version 1.3.11. |
|
Select PKCS#11 provider
|
Select the PKCS#11 provider mechanism on the smart card by selecting it from the combo box. Choosing Automatically detect provider will mean that all the providers will be checked upon startup - this setting does not work with several smart cards. For further information, refer to the known issues in the release notes. |
- Once you have made your selection click Next to continue.
- The Certificates dialog appears (only applicable if you selected Authentication via smartcard before):

- This dialog enables you to define the criteria for selecting the certificate used for encryption.
- Certificates can be distinguished by labels or key usage:
| Option | Details |
|
Label |
The term ‘Label’ refers to the filename of the certificate file on the smart card, for example User_Certificate. Follow these steps to add a certificate based on a Label:
If you have mistakenly entered a false label, select it from the list and click the Remove button to remove it from the list. To sort label preference, select a label in the list and click either Up or Down - the certificate that will be used for authentication is the first one in the list that matches the label criteria. |
| Key usage |
Key usage extensions define the purpose of the public key contained in a certificate. You can use them to restrict the public key to as few or as many operations as needed. For example, if you have a key used only for signing, enable the Digital signature and/or Non-repudiation extensions. Alternatively, if a key is used only for key management, enable Key encipherment. Follow these steps to add a certificate based on Key usage:
If you have mistakenly entered a false certificate label, select it from the list and click Remove. The following warning messages appears if there is no certificate key /Label selected:
For further details about the key usages supported by Matrix42 Full Disk Encryption smart card authentication refer to Matrix42 FDE - Administration and Usage Guide. |
|
Match policy |
Select one of the following policies:
|
- The Single sign-on dialog appears. Use the following options to determine an SSO method to Windows:
| Option | Details |
|
Default logon method |
Select the default logon method from the combo box. Choose between Windows credentials (user ID/password based) or smart card-based logon. Both logon methods can be available at boot time. |
|
Default PBA boot mode |
Select the default PBA boot method.
Available only for UEFI systems. For details, see Boot mechanisms |
|
Enable single sign-on for user ID/password authentication |
Check this option if you want PBA to take care of the traditional user name/password/domain logon to Windows (you will be required to enter the password only once at startup, make sure that the password is no longer than 32 symbols.). |
|
Enable single sign-on for smart card authentication |
Check this option if you already use a smart card (with X.509 certificates) to logon to the Windows domain. |

- Once you have made your selection, click Next to proceed to the next step.
- The Configure Locking dialog appears. Use the following options to help you configure how failed authentication attempts are handled:
| Option | Details |
|---|---|
|
Configure locking |
Check this option to activate the locking feature (leaving this option unchecked allows the user to enter their password incorrectly a limitless number of times without penalty). |
|
Maximum number of failed logins |
Enter the number of times a user may attempt to enter the correct password. This number should be greater than that for Failed attempts after which login is delayed. Entering the value 0 means that locking is deactivated! |
|
Failed logins till login is delayed
|
Enter the number of times a user may enter an incorrect password before being penalized with a time penalty the next time they logon. This number should be smaller than that for Maximum number of failed attempts. |

- Once you have made your selection, click Next to continue.
- The first PBA Pre-Boot Options dialog appears.

Use the following options to determine which options should be available to the end user in the PBA component as well as the PBA state (dialog 1 of 2):
| Option | Details |
|---|---|
|
Disable login method change |
Check this option to disable switching between authentication methods in the PBA component. NOTE: This means that once a specific authentication method has been selected together with this option, there is NO CHANCE to select the other authentication method in the PBA. |
|
Disable PBA advanced options |
Check this option to disable access to the PBA advanced options. NOTE: Enabling this option means that there is NO CHANCE to enter the advanced PBA options in the PBA. |
|
Allow only numeric PIN entries |
Check this option to allow only numeric smart card PIN entries. |
|
Disable PIN change |
Check this option to prevent smart card users from changing their PIN during the PBA-HelpDesk procedure. |
|
Disable PIN reset |
Check this option to prevent smart card users from resetting their PIN during the PBA-HelpDesk procedure. |
|
If a screen resolution is not specified, the default value take effect. It means that Matrix42 specifies screen resolution automatically, but in some cases this resolution doesn’t fit. E.g. 800x600 is a good selection for laptop devices. Limitations for BIOS systems: the option for changing the screen resolution works only with ACPI kernel where DRM is enabled. |
|
|
“Without DRM” mode |
Enable this boot mode option if there are problems with graphic card and PBA loading. |
|
Disable Adaptive Boot mode |
Adaptive Boot mode is used to automatically select the PBA boot mode that is needed for correct operating system boot. If the problem phase is identified, a user is informed. By default, Adaptive boot mode is enabled. For details about available boot modes, see boot mechanisms in the Matrix42 FDE - Administration and Usage Guide. |
|
Power off PBA after ‘n’ seconds |
Check this option to allow the PBA to shutdown the computer if the PBA remains unattended. Also enter the number of seconds the PBA should wait before shutting down the computer. |
- The second PBA Pre-Boot Options dialog appears:

- Configure the following options (dialog 2 of 2):
| Option | Details |
|---|---|
|
Background image |
Use this option to select an optional background for the PBA screen. Click ‘…’ to open the file browser and to select an image of your choice (the image will be automatically resized to the correct resolution and color depth for the PBA screen - 800x600 pixels, 24-bit).
|
|
Custom image path |
If you selected Custom in the field above, click Search in the Custom image path field to define a path for a background image. |
|
Keyboard layout |
Use the combo box to select which keyboard layout to be used for PBA. Keyboard layout for text-based and graphical Simple PBA (UEFI): only German and English layouts are supported. Directly in the mode, language switch is available only in graphical Simple PBA. Keyboard layout for text-based Simple PBA (BIOS): only English layout is supported. |
|
PBA integrity checking |
‘Integrity checking’ is the guarantee that the Linux PBA components are protected against tampering by third parties. The following levels are available: High Level (highly recommended) will check first and second-level hashes and offers the most security, but is slower than the other two. This is the default parameter. Middle level will check first-level hashes only and offers a compromise between speed and security. Low level (not recommended) -No integrity checking is performed which means the PBA will boot quicker, but there is no security against tampering by third parties. |
- Once you have made your selection click Next to continue.
- The following dialog may appear:

This dialog informs you that the selected keyboard layout does not match that of the operating system and may cause problems (different character positions) when used in the PBA (the installer assumes that the keyboard layout matches the language of the operating system). If you are sure about your selection click OK and continue with the next step. If you are not sure, click OK and then Back to review your selection.
The background image in this step is solely for an installation on the local hard disk. If you intend to deploy the same background image to several target computers in an unattended installation (click the link for details), then make sure you either copy the image to each target computer per software distribution first or create a branding file to be placed together with the installer.
Matrix42 recommends that you copy the image to the C:\WINDOWS\NAC directory, create a policy, and then deploy (see Matrix42 FDE - Administration and Usage Guide for details).
- The HelpDesk Keys and Friendly Network dialog appears.

This dialog for configuring the HelpDesk keys for use in an emergency. The HelpDesk is a central point of contact (in-house or third party) that can be contacted when you have forgotten a password, misplaced or broken the smart card, or if the smart card reader is defective. If you do not have an enterprise-wide HelpDesk, then ignore this feature. The HelpDesk uses a challenge–response process to unlock your hard disk. Once you configure HelpDesk, you can activate Friendly Network.
Matrix42 Full Disk Encryption HelpDesk (via HelpDesk Key)
This HelpDesk is used when a user has mislaid or lost smart card, or forgotten the Windows credentials. Furthermore, the PBA HelpDesk can also place PBA in ‘user capture’ mode. This means either the user can register a new smart card, or after a successful Windows logon, the user’s credentials are newly embedded in the PBA component. The HelpDesk key is provided as a file by the respective Matrix42 Full Disk Encryption HelpDesk administrator to be imported into PBA for such an event.
Friendly Network
Friendly network simplifies the process of booting if the network is known. If computer is outside the known network, the PBA asks for authentication. PBA authentication phase is skipped with the help of Helpdesk. When PBA is booted, helpdesk request is generated and sent to the Server. An attempt to sign in to the system on the basis of a server response is made. If the attempt is successful, the computer is restarted followed by Windows boot. If the attempt is unsuccessful (incorrect network configuration, no connection to the Server etc.), PBA authentication is needed as usually.
Restrictions:
- Not compatible with BIOS Simple PBA (text-based mode).
- The ACPI boot mode is not supported.
- Not compatible with Linux-based PBA if SSL is enabled.
Recommended (only BIOS): disable Quick Boot (Fast Boot) in BIOS settings as it skips the network drivers necessary for Friendly Network.
The following options are available:
| Option | Details |
|---|---|
|
Add Helpdesk key |
Import a HelpDesk key from a password-protected HelpDesk file. The helpdesk file is exported from a PBA HelpDesk application or from the Matrix42 Data Protection Console (Product settings | FDE | Helpdesk). NOTE: The HelpDesk feature has two different types of HelpDesk communication: Comfort - quick with good security, and Strong – very secure. It is important that you choose a method BEFORE you import the HelpDesk key file. The Import HelpDesk Key dialog will appear. Click the ‘…’ button to open the file explorer. Select the HelpDesk file and click Open. Enter the password for the file into the Key password field and click Import. |
|
Delete Helpdesk key |
Delete a HelpDesk key that has been imported into PBA. |
|
Enable self-initialization via helpdesk |
Check this option if you want the HelpDesk administrator to ‘allow’ the user to capture their Windows credentials/smart card details in an emergency. This means that the user is allowed to re-authorize himself/herself (smart card or Windows credentials) when the computer is next booted. |
|
Activate Friendly Network |
Activate Friendly Network so that if connection to the Server can be established during PBA, the authentication is skipped and boot into Windows occurs. |
|
IP |
Enter the IP address of the management server. This can be the Matrix42 Server or your own one. |
|
Port |
Enter the IP address of the management server. |
- Once you have made your selection, click Next to continue.
- The Windows Credentials dialog appears.

This dialog helps you to define the users to be authenticated to the system via their Windows user account details. The following options are available:
| Option | Details |
|
User capturing enabled |
Check this option to allow the next user who logs on to the computer to be initialized as a valid user (this means that it is not necessary to add a user to the list). |
|
New user has admin rights |
Check this option to allow the next new user who logs on to the computer to have Admin rights. |
|
Show last user name |
Check this option to always display the user name of the last known logged-on user in the PBA logon dialog. |
|
User entry [area] |
If you do not check User capturing enabled, then you must enter your Windows account details in this area to be able to log on to the computer. Follow these steps to add a user to the list: 1. Enter the User name, Account Password, and Domain in the respective fields. 2. Click New user has admin rights to enable the user to have administrator rights. Admin has the right to capture new user and delete user from the PBA user management list. 3. Click Add to complete the entry. The user will be added to the PBA management list. 4. Click Confirm to confirm the user’s account password. You can remove any user who has already been added to the list by selecting the user and clicking Remove. You can promote any user already added to the list as a User Admin by selecting the user and clicking Promote. |
- Once you have made your selection (and optionally added users), click Next to continue.
- The Smart Card user dialog appears. This dialog helps you to define the smart card users to be authenticated to the system.

The following options are available:
| Option | Details |
|---|---|
|
Self-initialization of first user enabled |
Check this option to allow the user that logs onto the computer at the next start with a valid smart card (correct PKCS#11 provider and credentials – key or certificate label), to be automatically initialized as a valid user (this means that it is not necessary to enter a user into the list via the User entry area). |
|
New user has admin rights |
Check this option to allow the next new user who logs on to the computer to have Admin rights. |
|
User entry |
If you did not check Self initialization of first user enabled, then you must manually enter the user certificate details in this area to be able to log on to the computer. Follow these steps to add a user to the list: 1. Check New user has admin rights to enable the user to have administrator rights. Admin has the right to capture new user and delete user from the PBA user management list. 2. Now you can: a. enter the certificate information manually, -OR- b. import a certificate. a. Entering the certificate information manually: Enter (or copy and paste) the values into the fields Distinguished name and Value of public key and click Apply to complete the entry. To fill in the Distinguished name and Value of public key fields: 1. Right-click a certificate and select Properties from the context menu. 2. In the Certificate dialog, navigate to the Details tab. 3. Copy the data from the Value column of the Subject entry to the Distinguished name field. 4. Copy the data of the Public key entry to the Value of public key field. Special characters and order.
b. Importing a certificate: Click Import, select the X.509 certificate (*.cer; der-encoded) from the file explorer [Open], then click Add. The user details are now in the list, but not yet in the system. Click Apply to complete the entry.
|
- Press Next to continue.
- As an alternative to importing each certificate separately, you can import all of them in a single step via the Batch Import function as follows:
- Make sure all the certificate files are in a single directory.
- Click Batchimport to open the file explorer.
- Select the certificates directory and click OK. A dialog will appear informing you about how many certificates have been found in the directory:

- Click OK.
- An import success dialog will appear:

- Click OK. The user entry list now contains the users:
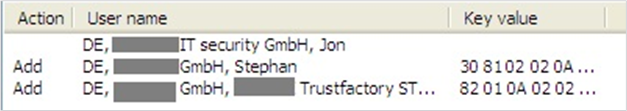
- Click Apply to confirm the entries.
- The ERI settings dialog appears. The following options are available:
| Option | Details |
|---|---|
|
Configure emergency recovery files settings |
Check the option to allow the use of ERI files (recommended). |
|
Allow using no password for saving emergency recovery information |
Allow user to save unprotected ERI files (not recommended). |
|
Minimum required password length |
Length of ERI password. Use the up/down arrows in the number field to set a minimum password length for the ERI file (at least 8 characters are recommended). |
|
Private emergency recovery information |
Check this option if you want ERI files generated on this computer to be able to recover this computer only (recommended for a strict security policy). If you leave this option unchecked, an administrator can access this computer using an ERI file generated on a similar system. |

- The Pre-Boot Authentication message dialog appears.
- Click OK to initialize Pre-Boot Authentication.

- The Initialization dialog appears. The initialization should start automatically. If not, click Finish to start the initialization procedure. It may take a while to complete - please be patient.

- The initialization of the PBA component is now complete. The new PBA settings will become active after the shutdown or restart of the computer. If you have selected Enable smart card user capturing or Enable user ID/password capturing options during the initialization, there is no need for authentication upon the initial PBA start (Matrix42 Full Disk Encryption will capture the user credentials of the first user who logs-on to the computer).
Shutdown and then restart the computer after the initialization of the PBA component to, optionally, capture user credentials (this does not apply to if user credentials or certificates have been passed onto the PBA component via an initialization policy).
Please uninstall FDE immediately if PBA initialization fails for any reason. Do not shutdown the system unless an ERI file was successfully generated.
Unattended installation
To start an unattended installation of FDE, you may need an initialization policy generated by the Matrix42 Full Disk Encryption Policy Builder – this means that you must install (but not initialize) Matrix42 Full Disk Encryption once to access each of the Policy Builder. For details about deploying policies, see the Matrix42 FDE - Administration and Usage Guide, chapter 1.14 “Remote administration”.
Be aware that the computer will reboot after the initialization of the FDE component. This is because the installer needs to create a small partition outside of the Windows runtime (this is also used for the PBA and is needed even if the PBA is not installed), as well as letting Windows register the encryption driver correctly. An optional, further reboot is necessary after the initialization of the PBA component to capture user credentials (this does not apply if user credentials or certificates have been passed onto the PBA component via an initialization policy).
Follow these steps below to perform an unattended installation:
- Customizing (optional): You can customize your setup through the following steps:
- If you have created a dmi.ini file for computers set for ‘Hardware Compatibility Mode’ then place it in the same directory as the Matrix42 Full Disk Encryption [version].msi package so that computers that need specific installation setting will be automatically recognized by the installer. For further information about how to create alternative installation parameters (also known as ‘Hardware Compatibility Mode’) refer to Matrix42 FDE - Administration and Usage Guide.
- If you have a specific background image for the PBA or HelpDesk text files that must be deployed, then place the EHDDbrand.bin file in the same directory as the MSI package.
- Prepare the Matrix42 Full Disk Encryption installation file.
- Open a Command window (select Start>Run). The following dialog appears. Enter cmd in the Open field, and click OK.

- The Command window appears. Navigate to the directory, where the Matrix42 Full Disk Encryption installation package is located. Two installer packages are available: for 32-bit systems use Full Disk Encryption.msi, and for 64-bit systems use Full Disk Encryption x64.msi.
- Use the following syntax to call the setup:
- msiexec /i "<full path to the msi package, file name, file extension>" /qn [<PROPERTY>=<value>] /l*vx "<full path to log file>"
- For example, enter the following:
- msiexec /i "C:\FDE versions\Matrix42 Full Disk Encryption by Matrix42 [version].msi" /qn ADDLOCAL=FeatureFde,FeaturePba INITFDEQ=1 /l*vx "C:\log files\log.txt"
The following Microsoft installer-related options are available:
| Command line option | Details |
|---|---|
|
/i, /qn, /qf |
Microsoft installer parameters:
|
|
Full Disk Encryption by [version].msi, Full Disk Encryption [version]x64.msi |
The file name of the Matrix42 Full Disk Encryption installer package according to system (32-bit/64-bit). |
|
/l*vx log.txt |
Create a very detailed log file of the unattended installation under the file name log.txt. vx stands for a detailed log file. If you do not want to have a detailed log file, remove this parameter. |
The following Matrix42 Full Disk Encryption related options are available:
| Command line option | Details |
|---|---|
|
ADDLOCAL
|
To install only FDE or both FDE and PBA for standard hard disks use the following (!the commands are case-sensitive):
NOTE: If this property is not entered the FDE/PBA components will not be installed. HINT: If those combinations don’t fit your needs it might help to use the MSI-switch ‘REMOVE=’ in combination with ‘ADDLOCAL=All’ |
|
ADMINPWD
|
This option allows you to provide the administration password for FDE initialization/de-initialization. For example: ADMINPWD=12345678 This property can only be used without property FDEPOLICY. |
|
FDEPOLICY
|
Provide the file name and path of an FDE initialization policy, for example: FDEPOLICY="c:\fdeinit.nbs". NOTE: This property must be used together with INITFDEQ. |
|
INITFDEQ
|
Initialize FDE after installation. Enter:
This property can only be used in combination with ADDLOCAL. If this property is not entered FDE will not be initialized. |
|
INITPBAQ
|
Initialize PBA after installation. Enter:
This property can only be used in combination with ADDLOCAL. If this property is not entered PBA will not be initialized. |
|
PBAPOLICY
|
Provide the file name and path to PBA initialization policy, for example: PBAPOLICY="c:\pba.pba". NOTE: This property can only be used if the property INITPBAQ=1 is also used. |
|
LANG
|
The property is used to select the language. Enter:
If you do not set this property the default language (en_US-English) will be used. |
|
WMIQUERY (Advanced users only!)
|
Enable/Disable WMI queries made by the installer. Under certain rollout scenarios in which no remote administrator permissions have been granted, you can disable WMI querying made by the installer.
NOTE: Turning-off WMI querying will only work with certain hardware! |
|
DMIINIPATH
|
The path to the dmi.ini file used to specify computers targeted for hardware compatibility mode. This is only necessary if the .ini file is not in the same directory as the MSI package. For information about hardware compatibility modes refer to Matrix42 FDE - Administration and Usage Guide. |
|
SYS420A=1 |
Alternative boot loader to specific (or problem) configurations. |
The only way to completely install Matrix42 Full Disk Encryption without the need for user interaction for dialogs is to use policies for the FDE and PBA components. Refer to Matrix42 FDE - Administration and Usage Guide. See below for examples of the command line syntax for such installations.
Example syntax for installation
- For Standard hard disks
- Install FDE only, initialize FDE, do not display GUI, and log the whole procedure to a log file on the local hard disk:
msiexec /i "<full MSI file path, name, and extension>" /qn ADDLOCAL=FeatureFde INITFDEQ=1 FDEPOLICY="c:\fdeinit.nbs" /l* "<full log file path, name, and extension>"
- To install FDE and PBA, initialize FDE and PBA according to policies, do not display a GUI, and log the whole procedure to a log file on the local hard disk, you must deploy two policies:
msiexec /i "<full MSI file path, name, and extension>" /qn /l* "<full log file path, name, and extension>" ADDLOCAL=FeatureFde,FeaturePba INITFDEQ=1 FDEPOLICY="c:\fdeinit.nbs" INITPBAQ=1 PBAPOLICY="c:\pbainit.pba" /forcerestart
NOTE: A third [configuration] policy must be deployed to perform encryption.
- To install all features of Full Disk Encryption and initialize both FDE and PBA
msiexec.exe /i "<full MSI path, name, and extension>" /qn /l* "<full og file path, name, and extension>" ADDLOCAL=All INITFDEQ=1 INITPBAQ=1 ADMINPWD=12345678
- To uninstall and update FDE and PBA use the following command line options:
fdeinit [-uninstall|-update] -silent <admin password> fdeinit @<fdeinit policy>|<fdedeinit policy> fdeinit @<upgradepolicy> Pbainit [-uninstall|-update] -silent <admin password> Pbainit @<PBA init policy>|<PBA deinit policy> Pbainit @<upgradepolicy> update: performs an update of the PBA/FDE. uninstall: Matrix42 Full Disk Encryption PBA/FDE will be deinitialized with this version.
If the above two options are omitted then the mode will be automatically selected based on the current state of initialization as given below.
- For PBAInit, if PBA is already initialized deinitialization will be performed, else initialization will be performed.
- For FDEInit, if FDE is already initialized update will be performed, else initialization will be performed.
Full Disk Encryption must be installed before running fdeinit and pbainit command. To run fdeinit, a current directory must be changed to C:\Windows\NAC. To run pbainit, a current directory must be changed to C:\Windows\NAC\SBS
If you have a custom dmi.ini file you wish to deploy with the Matrix42 Full Disk Encryption MSI package, then make sure that it resides in the same installation directory as the MSI package. This will ensure that the file is recognized and Matrix42 Full Disk Encryption will use the correct boot parameters for those computer models defined in the dmi.ini file.
Collecting FDE installer logs
- Run cmd an administrator.
- Execute the following command:
msiexec.exe /i "e:\files\Matrix42 Full Disk Encryption by Matrix42 [version].msi" /l*vx "c:\fde-install-log.txt"
- Collect the logs in the specified path.
Before contacting support
Before you contact the Support team, please check the following article about how to get help for technical issues:
Getting help for technical issues

