IntellAct Automation
Overview
IntellAct Automation (IAA) audits and analyzes the audited data to trigger protective measures for critical events. Use rules to define which actions must be executed in response to a critical event on the end device (Agent) or on the Server.
Limited IntellAct Automation functionality without IntellAct Automation license.If there is no license for IntellAct Automation, only the following functionality is available:
- All actions for all events under Product settings | IntellAct | Rules - Server.
- The Mail notification and SNMP notification actions under Product settings | IntellAct | Rules - Client.
You can configure predefined rules for servers and clients, as well as custom rules for specific operations. Depending on the rule type, certain actions can be triggered.
Actions for IntellAct events
When you define rules in IntellAct Automation, you can define certain actions that should be triggered when the corresponding process occurs or the rule is violated. Different actions are available depending on the type of the process.
| Action | Description | Availability |
|---|---|---|
|
Mail notification |
Notification about the rule violation is send to the specified e-mail address. Additional configuration: set up the SMTP server settings. Additional product activation: required products to trigger mail and SNMP (only client rules). See also Grouping mail notifications (only for Rules - Custom and client rules). |
All rules |
|
SNMP notification |
Notification about the rule violation is send to the specified e-mail address. Additional configuration: set up the SNMP server settings. Additional product activation: required products to trigger mail and SNMP (only client rules). |
All rules |
|
Inform tenant admins |
Notification is sent via e-mail to the address specified under Administration | Superadmin | Administrators & scopes. |
Server rules (only Audit data size control and Database size control) |
|
Trigger workflow |
A workflow is triggered in Matrix42 Workspace Management. For details, see: Triggering Matrix42 workspace management workflows via IntellAct Automation |
Client rules |
|
Deny access |
No access status for all devices or for the selected ones is shown on Agent within the defined period of time. <Used device> blocks access only on the devices where the limit is violated. Activate Access Control for a user. |
Client rules (except Access rights requests), Rules - Custom |
|
Send status to Macmon |
The defined status is sent to Macmon. |
Client rules (except Access rights requests), Rules - Custom |
|
Shut down computer |
The computer of a user will be shut down. |
Client rules, Rules - Custom |
|
Show user message |
A message is displayed to the user informing him of the rule violation. |
Rules - Custom |
Grouping mail notifications for events that occur on clients
Manage mail notifications about the violation of custom and client rules so that notifications about an event on one client are grouped and sent as a single message.
- Go to Product settings | IntellAct | Settings.
- Enable the Group mail notifications within option.
- Select within which time period the mail notifications about one event are grouped in a single message.
- Rules - Custom: the event limit that is violated more than once a day (or till restart) is displayed in a message as one limit violation (first violation). For detailed info about all limit violations, go to Product settings | IntellAct | Events | Incidents.
- Click Save.
Configuring IntellAct Automation for Clients
With IntellAct Automation, you can define rules that monitor certain events on the client and undertake actions when they occur.
Defining rules for events on the clients
- Go to Product settings | IntellAct | Rules – Client.
- In the IntellAct Automation – Rules – Client area, click Add and select an event from the list.
- A new entry appears in the list.

- To assign the rule to a certain user or computer, select a directory object under Selection of objects. If no object is selected, the rule is assigned to all users or all computers. For details, see: Assigning IntellAct rules
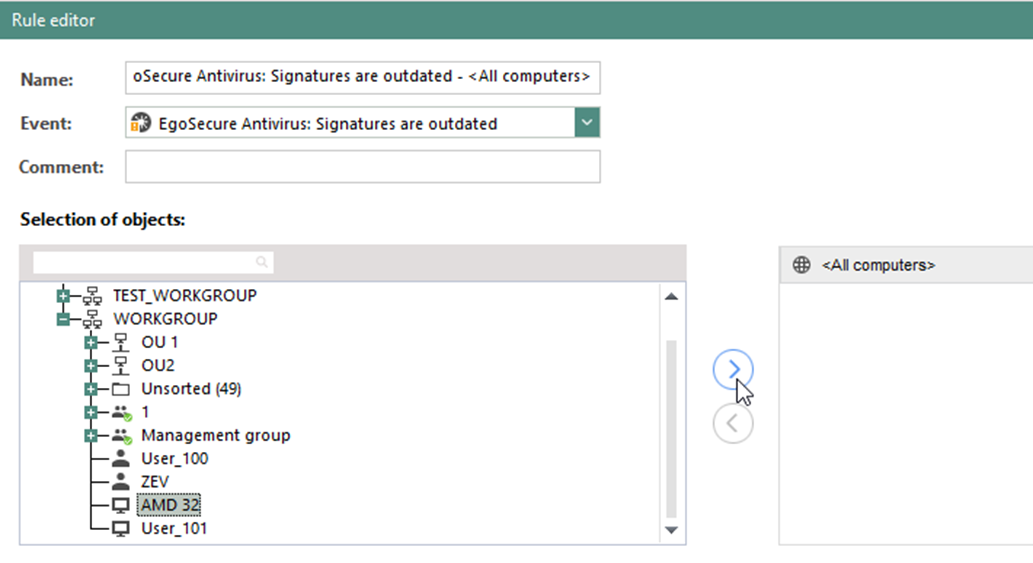
- For Green IT: Suspicious activity as well as for EgoSecure Antivirus: signatures are outdated, define the following settings under Criteria:
- Green IT: Suspicious activity: define the regular working hours. Activities of the client outside of the specified time are considered a rule violation.
- EgoSecure Antivirus: signatures are outdated: set the number of days since the last update after which signatures are considered outdated. The signatures are downloaded from the Internet to the Server and then updated on Agent. For details, see: Update settings for Antivirus
- Under Actions, define what actions IntellAct Automation performs when an event occurs. For details, see: Actions for IntellAct rules

- Click Save.
Product activation for events to trigger Mail notifications and SNMP notifications
For users or computers from which the IntellAct information is collected, make sure to activate the following products to send mail or SNMP notifications:
| Event | Additional product activation required |
|---|---|
|
Access denied (Access Control) |
|
|
Access denied (Application Control) |
|
|
Access requests |
|
|
EgoSecure Antivirus: Signatures are outdated |
|
|
EgoSecure Antivirus: Threat found |
|
|
EgoSecure Antivirus: State changed |
|
|
Green IT: Suspicious activity |
|
Blocked access due to IntellAct Automation
One possible action that can be triggered by IntellAct rules is to block user access to certain devices. A user, for example, has a limit of writing two files a day to external storage. Once the limit is exceeded, further access to external storage media can be blocked, for example, for an hour.
Access rights due to IntellAct vs. Access Control. IntellAct Automation access rights have a priority over user/computer rights. Only permitted devices can overlap IntellAct Automation rights.
Restoring access denied by IntellAct
- Select a user in User management.
- Under User management | Control | Devices and ports tab, right-click a device.
- Select IntellAct Automation - unblocking code... from the context menu.
- The Unblocking code generation – IntellAct Automation dialog appears.
- In the Event drop-down menu, select one of the following:
- A specific event to cancel access restriction due to this event and save access restriction (if any) because of another IntellAct event.
- <All events> to restore access to the device that happened due to several IntellAct events.
- Click Generate.
- Copy the code and send it to a user.
- The client can now enter the code via the EgoSecure Agent and receive granted access rights:

- The access block provided by IntellAct Automation is now cancelled and the previously defined access rights (full, read or write access) for the device are restored.
- New code doesn’t replace the previous one.
Configuring IntellAct Automation for EgoSecure Server
With IntellAct you can create rules for certain events on the Server and define actions when an event occurs.
Defining rules for operations on the Server
- Go to Product settings | IntellAct Automation | Rules – Server.
- In the IntellAct – Rules – Server area, click Add and select a rule from the drop-down list.
- A new entry appears in the list.
- Under Criteria, define the settings for the rule. For details, see the table below.
- Under Actions, select the way of notification. For details, see: IntellAct Automation events
- Click Save.
| Event | Criteria |
|---|---|
|
Scheduled AD synchronization |
Select the type of event you want to be notified of:
|
|
Integrity control |
Select the type of event you want to be notified of:
For details, see: Integrity control |
|
SSL certificates control |
Define the number of days before expiration when notification must appear. |
|
EgoSecure Antivirus: signatured are outdated |
Define the number of days since the last update after which signatures are considered outdated. The signatures are downloaded from the Internet to the Server and then updated on the Agent side. |
|
License notifications |
Define when to notify about expiring licenses and the limited percentage of unused licenses. Also set how often to remind about expired licenses and about reaching a maximum license quantity. |
|
Database size control |
Set when to notify about reaching database size and transaction log size limits. |
|
Audit data size control |
Determine when to inform you about the size of the audit data in the database. Specify what percentage of the maximum size can be reached. |
Configuring IntellAct Automation for users
In addition to the predefined rules for client and server, you can also create IntellAct Automation user rules. For this you create an event with certain parameters. Before creating an event, define which values are used to calculate statistics.
Configuring statistics calculation parameters
- Go to Product settings | IntellAct Automation | Settings.
- Specify the time period (in days) to be used to calculate the average daily rate for custom operations.
- Enter the minimum number of days that must be used to calculate the average daily rate.
- Click Save.
Minimum number of days to calculate the average rate. If statistics are not available for enough days to reach the specified minimum number of days, events do not function, for which the option Limit | Abnormality detection is enabled in rule criteria. Corresponding rules do not apply. Ensure that there are enough statistics to calculate the average daily rate, or select the Limit | Absolute value option for the respective event.
The following custom events are available:
|
Event |
Criteria |
Controlled devices |
Controlled access types |
Additional configuration required |
|---|---|---|---|---|
|
Storage: file access limit |
A limit of reading and/or writing files |
|
|
- |
|
Network: file access limit |
A limit of reading and/or writing files |
|
|
Enable the following options for a computer under Computer management | Settings | Client settings:
|
|
Storage: unencrypted file transfer limit |
A limit of transferring files without encryption |
|
|
|
|
HTTP/HTTPS traffic limit |
A limit of inbound and/or outbound traffic transferred via HTTP and HTTPS protocol |
- |
- |
- |
|
Cloud: file access limit |
A limit of reading and/or writing files |
|
|
|
|
Cloud: unencrypted file transfer limit |
A limit of transferring files without encryption |
|
|
|
|
DLP DIU file access limit |
A limit of the number of files, which match the criteria of DLP DIU filters assigned to a user |
|
|
|
Creating a custom event
- Go to Product settings | IntellAct | Events.
- In the IntellAct Automation – Events area, select an event from the drop-down list.
- A new entry appears in the list.

- In the Parameters tab, select for which device class the event applies.

- Under Access, select whether the event must only be used for read or write access or for both.
- Under Limit, define the settings for the event. For details, see the table below:
| Setting | Description |
|---|---|
|
Statistics calculation |
Define whether the number or the total size of the files that must be used for statistics calculation. This setting is not available for the HTTP/HTTPS traffic limit event. |
|
Limit |
Define the amount of data transfer to which the file transfer or HTTP traffic should be limited. To limit, specify an absolute value for a defined period of time or specify the percentage by which the daily amount of data may differ from the average daily rate. |
- Click Save.
Creating custom rules
- Go to Product settings | IntellAct | Rules - Custom.
- In the IntellAct Automation – Rules – Custom area, click Add and select an event to which to apply the rule.

- A new entry appears in the list.
- To assign the rule to specific users, choose the objects under Selection of users. If no object is selected, the rule applies to all users. For details, see: Assigning IntellAct rules
- Under Actions, specify which actions to perform when an event occurs. For details, see: Actions for IntellAct events

- Click Save.
Assigning IntellAct rules
Depending on the event, client and custom rules can be assigned to certain users or computers. Once a rule is assigned to selected objects, it only applies to the events of these users or on these computers of the directory. By default, no events are assigned; in this case, rules apply to all users or computers of the directory.
Custom rules as well as client rules for the events Access denied (Access Control), Access denied (Application Control) and Access rights requests are assigned to users. Other client rules are assigned to computers.
Assigning IntellAct rule for user
- Go to Product settings | IntellAct | Rules – Custom or Rules – Client.
- Select the rule from the list.
- Under Selection of objects, double-click the directory objects on the left or select the object and click the right arrow.

- The selected directory objects appear in the area on the right.
- Click Save on the toolbar.
Assigning IntellAct rule to computer
- Go to Product settings | IntellAct | Rules – Client.
- Select the rule from the list.
- In the Rule editor area, double-click the directory objects under Selection of users:
- The selected objects appear in the area on the right.
- Click Save on the toolbar.
Setting up IntellAct Automation to trigger Matrix42 Workspace Management workflows
The integration of two systems - the Matrix42 Workspace Management system and the EgoSecure Server - allows to extend the administration options in your company. Via the central management tool of the EgoSecure Server - the EgoSecure Data Protection Console - you can create IntellAct tasks and then select the Trigger workflow option as an action to trigger the previously defined workflow in the Service Desk, once the conditions of an IntellAct client rule are met.
Workflows are triggered only for client rules. In the current EgoSecure Data Protection version, the option for triggering workflows is available only for the predefined client rules. For future versions, the integration of this check box is planned for custom rules.
Connecting the EgoSecure Server and the Matrix42 Server
- In the Matrix42 Workspace Management, navigate to Administration | Integration | Web Services Tokens and then click Generate Api Token.

- In the Name field, define the token name.
- In the Expires on drop-down menu, select Never.
- In the User field, specify a user for whom this token is assigned. With the help of this key the specified user can perform only the actions permitted within his rights in the system.
- Click Generate API token.

- Copy the Api Token value now, as it will not be available later.
Adding token to the Console
- Open the EgoSecure Data Protection Console and navigate to Administration | Servers | Mail, proxy and others.
- Scroll down to the Matrix42 Workspace Management server settings area.
- In the Server field, define the web address of the Matrix42 Workspace Management server.
- In the Token field, enter or paste the Api Token value, created in the steps before.

- Click Save.
Creating and editing workflows for EgoSecure
In the current section you can find details about how to create a simple workflow that is used to get data from the EgoSecure Server and to create a task in the Service Management. You can create this simple workflow manually using the description below or you can skip this part and use the workflow with preconfigured arguments. To use the workflow with preconfigured arguments, all you need to do is to download the Service Management Security Connector from Matrix42 Marketplace (registration required) and install it on the computer with Matrix42 Workspace Management server.
For the advanced usage of workflows, see Matrix42 help files - workflows.
- In the Matrix42 Workflow Studio, create a blank workflow. One workflow is created for one IntellAct event.

- Define the workflow properties and click Save.

- Under Repository, search for Create task and drag it after Start
- In the View menu, click .
- The field for editing arguments appears on the bottom.

- Add all arguments for an IntellAct event manually. One argument is per one string. For details, see the list of arguments for each event below in the table:
| Events | Arguments | |
|---|---|---|
|
Access rights requests |
|
|
|
Access denied (Access Control) |
|
|
|
EgoSecure Antivirus: Threat found |
|
|
|
EgoSecure Antivirus: State changed |
|
|
|
Access denied (Application Control) |
|
|
|
Green IT: Suspicious activity |
|
|
|
EgoSecure Antivirus: Signatures are outdated |
|
|
- Add arguments to display them in a certain field of an incident, once an administrator receives it:
- Select the field and click on


- The dialog for editing appears.
- Enter the text, which describes the argument and then click


- The Select Variable dialog appears.
- Select the argument and click OK to close the dialog.
- The argument appears after a user-defined text in an orange box.
- Click OK to close the dialog and save the changes.
- Publish the workflow:
- In the Release & Publish area, click Validate.
- In the Document area, click Check In.
- In the Release & Publish area, click Release and then Publish.

- As soon as workflows for all IntellAct events are created, get the workflow ID:
- Navigate to Administration | Services & Processes | Workflows | Manage Workflows.
- Select a registered workflow from the list. For details about creating and managing workflows, see: Matrix42 Help - Workflows
- Click Export, select the XML radio button and then click Export.
- The XML file opens in a new tab.
- To find the right place in the workflow XML, search for the tag <PLSLXamlComponentType> and copy the workflow ID below.

Setting up IntellAct rules for triggering workflows
- Skip this step and proceed with step 2 if you have installed the Service Management Security Connector instead of configuring a workflow manually. If you have configured a workflow manually, then in the EgoSecure Data Protection Console, create a workflow under Product settings | IntellAct | Settings:
- In the Matrix42 workflow management area, click Add.
- Define the workflow name in the Name column.
- Paste the ID you copied in the previous steps.
- Click Save.
- Create an IntellAct rule under Product settings | IntellAct | Rules - Client. For details about creating IntellAct rules, see: Configuring IntellAct for computers
- Under Actions, enable the Trigger workflow check box. The Trigger workflow check box is currently available only for Rules – Client. In next releases, we plan to integrate this check box for the Rules - Custom area.

- Select the workflows from the list:
- Select any of the workflows if you configured them manually.
- EgoSecure Create Incident if instead of the manual workflow setup you installed the Service Management Security Connector.
- Click Save.
- Once the conditions are met, the EgoSecure Server sends all information to the Matrix42 server and the task is created in the Service Desk.