Questionary Summary
System:
-
Pre-Requisites:
Question: Which pre-requisites are necessary to get the environment working
Answer: Following connections / firewall setings and ports are necessary
| Instance | Target | TCP/IP/PORT | Function |
|
Collector/Client
|
Aggregator Core |
8081 555 |
Registration Status, Configuration and Events Compressed OS Metadata |
|
Core |
Aggregator EDR |
8081 443 |
Registration Status and Events Threat Hunting Data |
|
Aggregator
|
Manager Core |
443 HighPort |
Events, Configuration & Licensing Registration Status and Events |
|
Manager
|
Syslog Server SMTP Server EDR FCE/ECS (Cloud Reputation Service) - rbq.cldsrv.ensilo.com - cldsrv.ensilo.com Administration |
6514 587 443 443
443 |
TCP and SSL TLS security necessary Hash and File Search Fortinet/enSilo cloud service
GUI Access |
Console
-
ACCESS
Question: Can the console be accessed remotely?
Answer: Yes, the access to the system/console will be over https://x.x.x:44
-
LDAP ACCESS
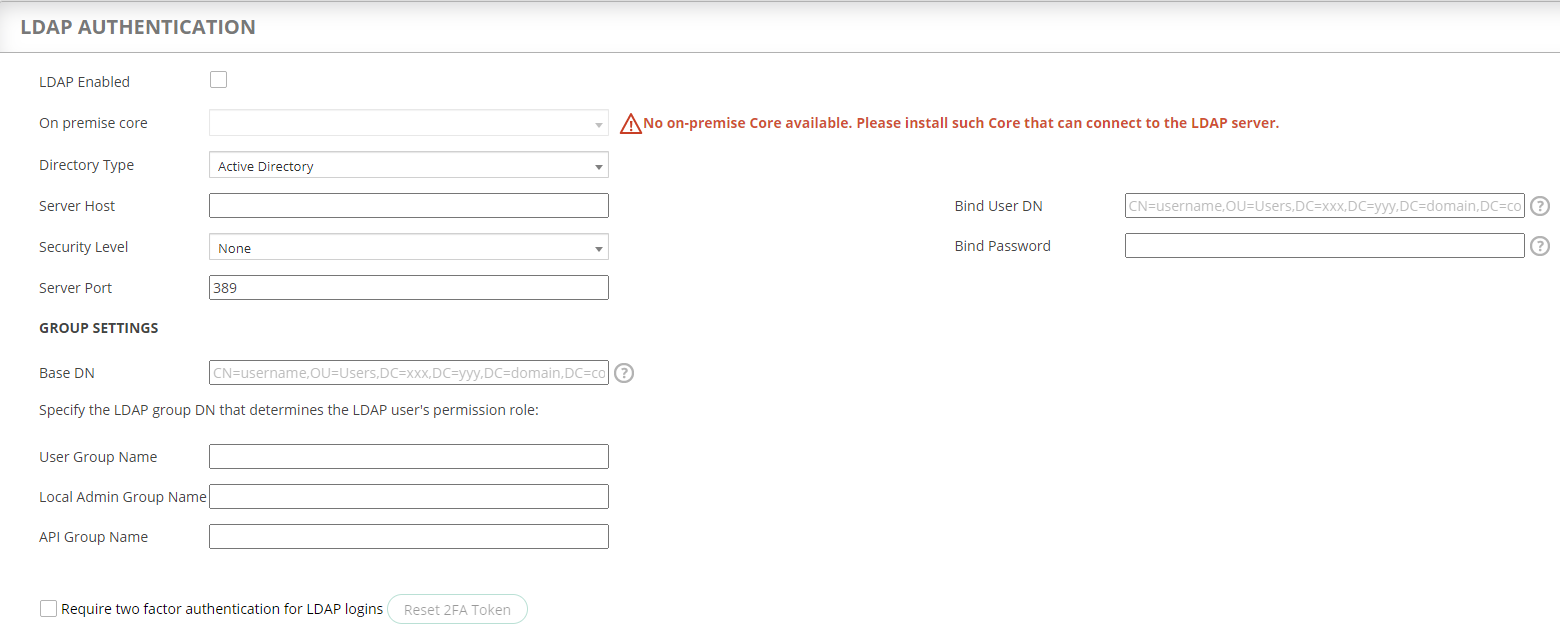
-
SAML ACCESS
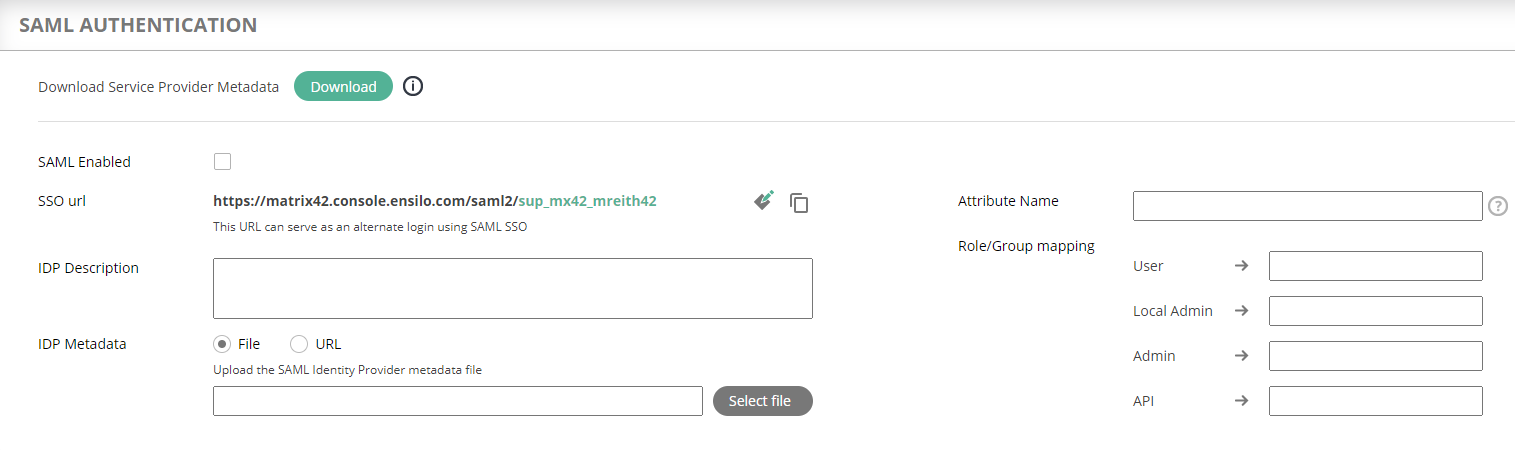
User
-
USER ROLES
Question: Can roles/profiles be created that limit the access and privileges inside the console (In example: Administrators and other profiles)?
Answer: Yes, we distinguish between following roles:
-
User
This user is allowed to view all information and to perform actions for its own organization, such as to mark events as handled, change policies
and define Exceptions. This user is similar to the Local Administrator. However, this user cannot access the ADMINISTRATION tab & settings. -
RestAPI
To perform a request to the enSilo REST API layer, the user performing the calls must have the relevant REST API role defined.
A user attempting to perform API calls without the REST API role gets a 401 Unauthorized Access error code. The Admin role does not provide
access to the REST API layer, and does not contain the Rest API role. Assigning a user the REST API role automatically generates the X-Auth-Token
n the enSilo Central Manager. Although basic authentication generates this token, the token is not required for basic authentication. The X-Auth-Token
is required for API token authorization, as described on page 7. After the REST API role is assigned to a user, that user can perform API calls using basic
authentication by supplying only his/her user name and password. When using basic authentication, the user name and password must be supplied for
each API call. -
Local Admin
Is a super user that can perform all operations in the FortiEDR Central Manager console for a single organization. This role can only access its
own organization’s data, and also includes the same privileges as the User role. More than one Local Administrator role is permitted per organization. -
Admin
Is the highest-level super user that can perform all operations in the FortiEDR Central Manager console for all organizations. This role can access all
organizations in the system, and also includes the same privileges as the Local Administrator and User roles. In a FortiEDR multi-organization system,
the system comes with one predefined Administrator user. More than one Administrator role is permitted.
-
USER ACCESS ABILITIES
Question: Can user access all sections of the console
Answer: No users are restricted to the above given "User Roles" informations.
-
USER ACCESS ABILITIES
Question: Avoid possibility of unwanted changes in general/wide configurations
Answer: Yes. administrative general/wide configurations will be made in the administration tab only local admins or administrators
have access to.
Agent/Collector
Legacy System Support
-
Collectors:
Question: Microsoft installer for Windows XP SP2 and earlier
Answer: Each new version of the collector is usable to support legacy systems.
We are "not" supporting legacy systems prior WinXP.
KB Overview
-
KB necessary at legacy Systems:
- KB2921916
This hotfix has been discontinued. This KB is only available for customers with a paid support contract with Microsoft
If you need this HF please open a Ticket at
helpdesk@matrix42.com [TOPIC: KB2921916 - FortiEDR Request]
- KB3033929
Microsoft has released a security advisory for IT professionals about SHA-2 code signing support. The security advisory
announces the availability of a security update and contains additional security-related information. To view the security
advisory, go to the following Microsoft website:https://technet.microsoft.com/en-us/library/security/3033929
- KB4474419
https://www.catalog.update.microsoft.com/search.aspx?q=kb4474419%22
This security update was released on March 12, 2019 for Windows 7 SP1 and Windows Server 2008 R2 SP1.
This security update was updated on May 14, 2019 to add support for Windows Server 2008 SP2.
This security update was updated on June 11, 2019 for Windows Server 2008 SP2 to resolve an issue with SHA-2 support for MSI files.
This security update was updated on August 13, 2019 to include the bootmgfw.efi file to prevent startup errors on IA64-based versions of Windows 7 SP1 and Windows Server 2008 R2 SP1.
This security update was updated on September 10, 2019 to include Start Manager files to prevent startup failures on x64-based versions of Windows 7 SP1, Windows Server 2008 R2 SP1, and Windows Server 2008 SP2.
This security update was updated on September 23, 2019 to correct a problem with the Windows Update Agent with the ZH-HK Language Pack installed.
