Creating the service connection for the Intune data provider
Overview
A service connection allows you to establish access to Microsoft Azure portal and obtain data from it without sharing the credentials. A service connection is configured once and then can automatically use a service for obtaining data.
The Intune add-on contains an Intune Integration capability for the Microsoft 365 service. This capability is needed for creating a service connection to Microsoft Azure portal.
To create a service connection, take the following steps:
- Configure the authentication and authorization settings for integration in Microsoft Azure portal.
- Create a Tenant in Enterprise Service Management.
- Create a Service Connection in Enterprise Service Management.
Configuring the authentication and authorization on Microsoft Azure Portal
To configure the integration settings in Microsoft Azure portal, you will need to register your Enterprise Service Management application on the portal.
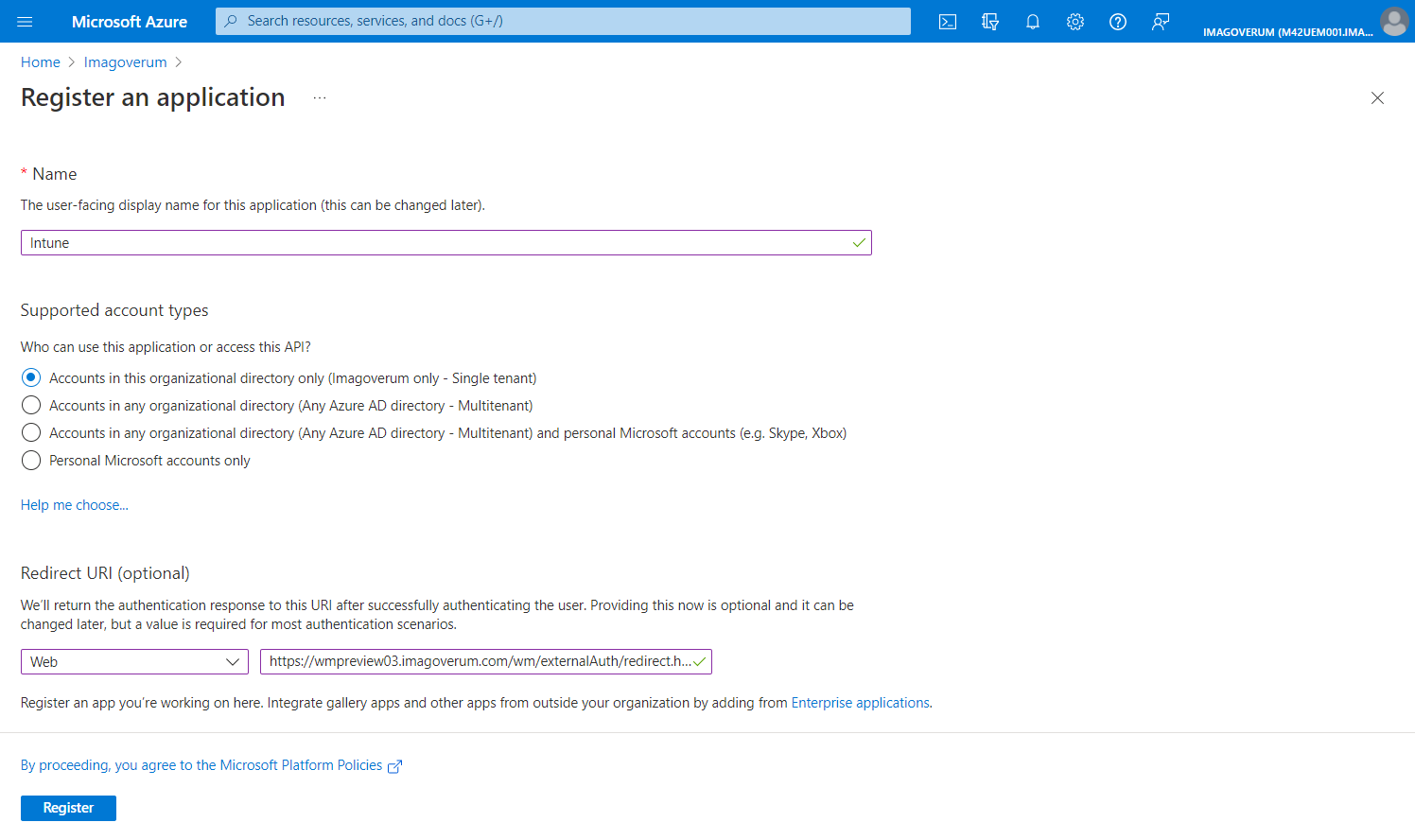
Registering an application
Information about required permissions to create and manage a Registered App in Azure is available here (external link).
- On the Microsoft Azure Portal home page, go to the Azure services and click App registrations.
- On the opened page, run the New registration action.
- Configure your application:
- Provide a name for the application integration.
- Choose Supported account types.
- Add a Redirect URI: select Web and enter Redirect URI (in the following format: https://{your_domain_name}/wm/externalAuth/redirect.html).
- Click Register.
Assigning permissions
Permissions of two types can be granted in Azure for data access:
- Delegated permissions (access on behalf of a user)
- Application permissions (access independent from a user)
Please make sure you understood the impact of each permission type. Specific information provided by Microsoft is available here (external link).
For all "delegated" permissions you have granted to the registered App, it is required that the user who authenticates the created Service Connection in Enterprise Service Management needs to have the corresponding access rights in Azure.
For all "application" permissions you have granted to the registered App, the access rights of the authenticating user are not effective.
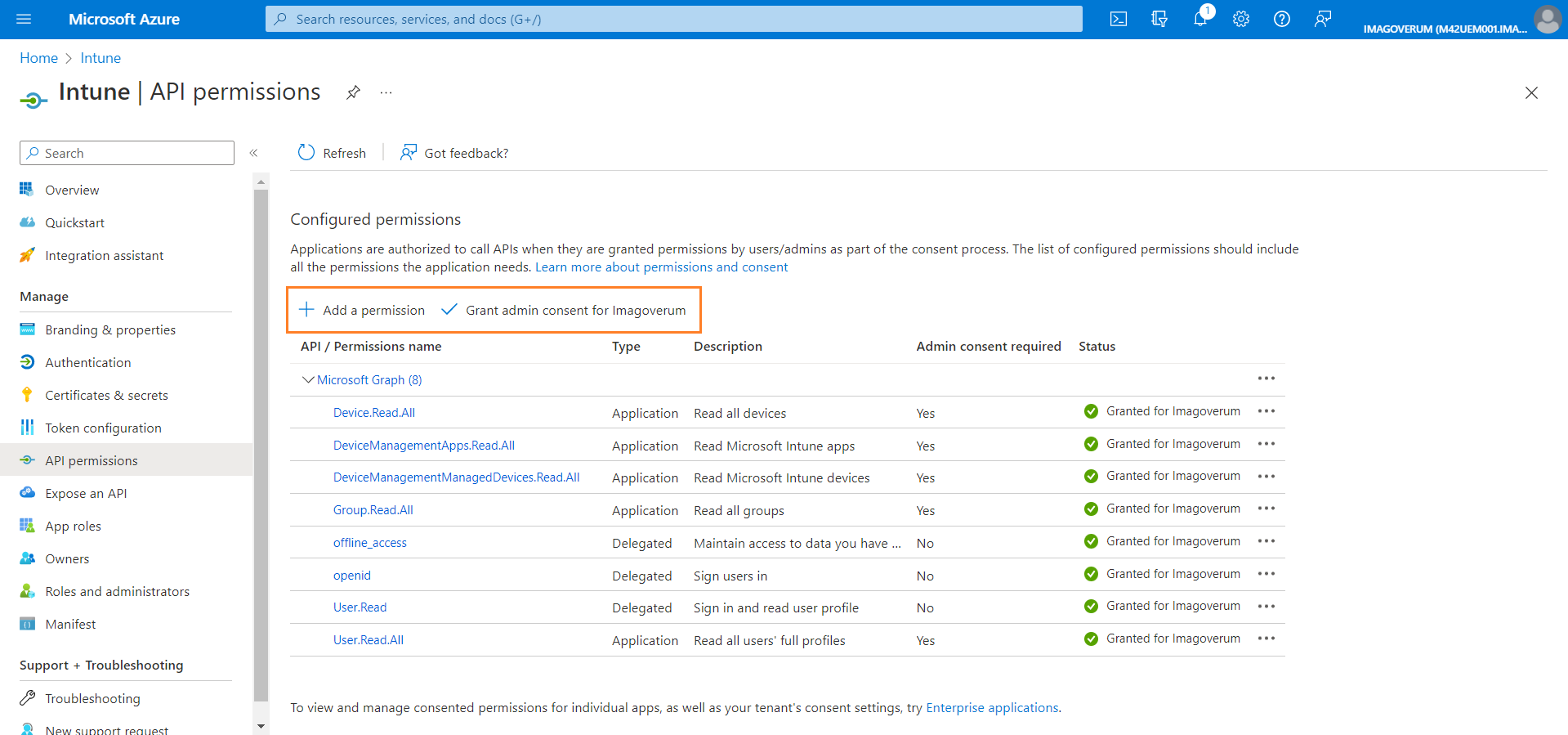
- After the application is created, go to the API permissions section of the new application.
- Use the Add a permission action to add a permission. Choose Microsoft Graph and add following permissions, selecting your preferred permission type in each case:
- Device.Read.All
- DeviceManagementApps.Read.All
- DeviceManagementManagedDevices.Read.All
- offline_access
- openid
- User.Read
- User.Read.All
If you are setting permissions for the Matrix42 Intune Provisioning add-on, you should also add the following permissions: Group.ReadWrite.All (either Application or Delegated).
- Then run the Grant admin consent action.
Creating a secret key
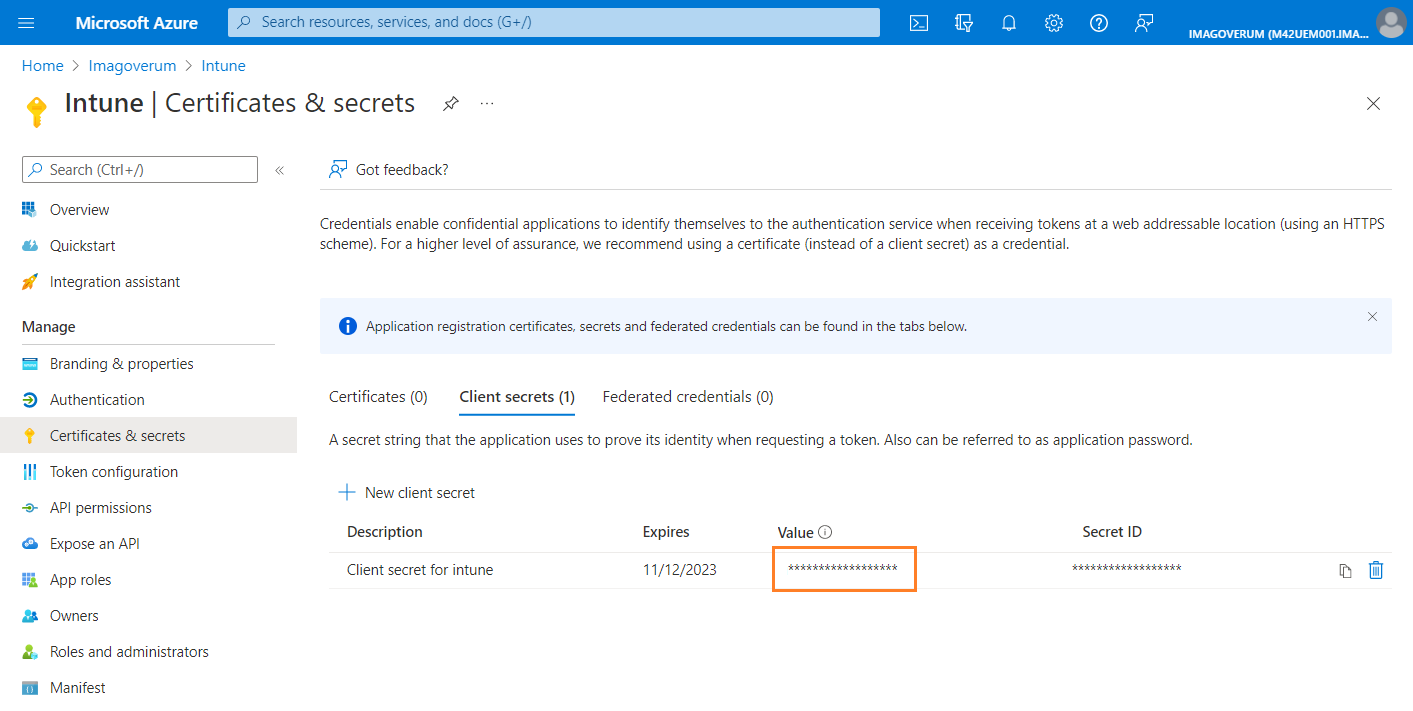
- Go to the Certificates & secrets section of the new application.
- Run the New client secret action to create a secret key.
- Provide the description and expiration date for the key and click Add.
- After a new key is displayed, copy its value immediately. Later it will be hidden.
Save the secret key value. It will be used to create a service connection in Matrix42 Enterprise Service Management.
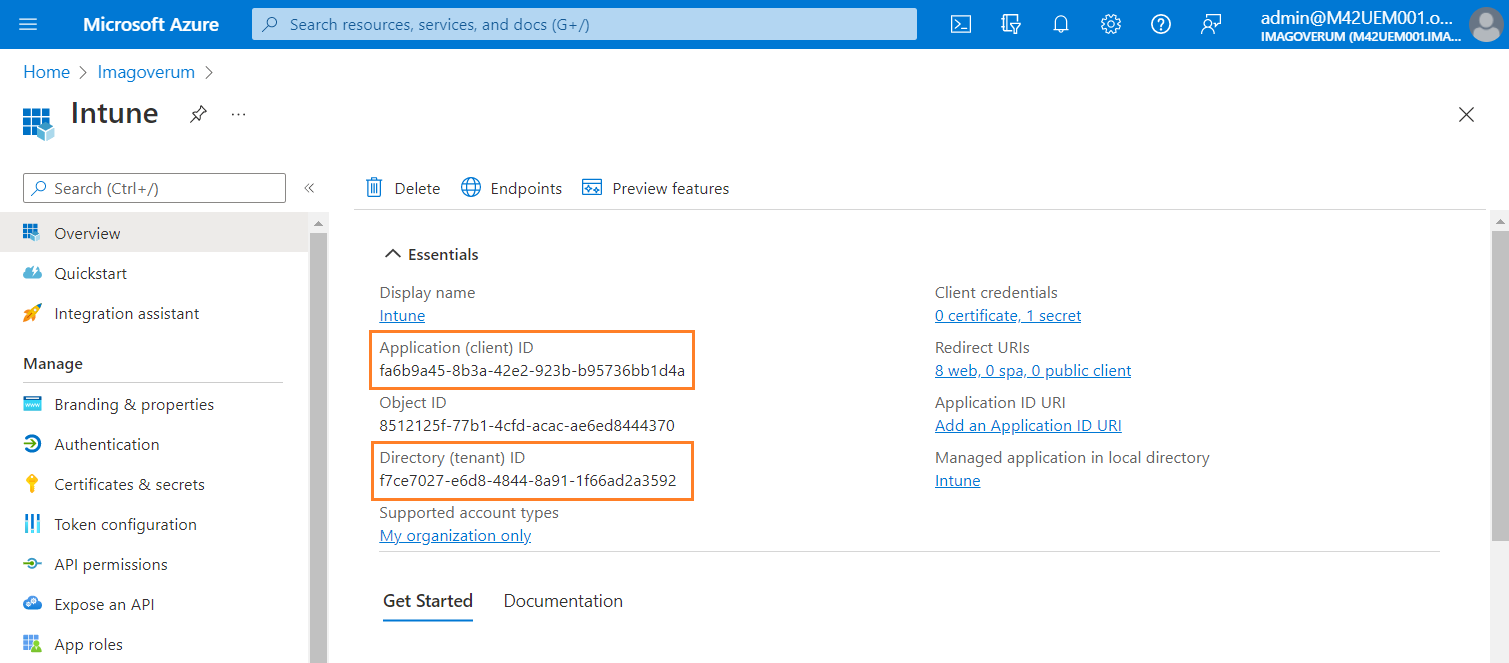
Retrieving the client ID and tenant ID
Client ID and tenant ID of your registered application are required for creating a service connection. You can find these values in the Overview section of the registered application.
Creating a tenant
In Matrix42 Enterprise Service Management, you need to create a tenant for the service connection.
- Go to the Administration application and open the Integration > Service Connections > Tenants navigation item.
- Run the Add Tenant action. A new tenant dialog opens.
- Provide an appropriate name for your tenant from the Microsoft Azure portal.
- Select Microsoft Entra ID in the Service field.
- Fill in the Client ID, Tenant and Client Secret fields with the data from Microsoft Azure.
- Save the dialog.
Creating a service connection
Next, create a service connection to your company's Microsoft Azure portal.
- In the Administration application, go to Integration > Service Connections > Connections.
- Run the Add Service Connection action. A new connection dialog opens.
- In the Service field, select Microsoft Entra ID - Intune for delegated access or Microsoft Entra ID - Intune (Application) for application access.
- In the Tenant field, select the tenant record that you have created earlier.
- Click Setup authentication.
- Provide the credentials for your company's Microsoft Azure portal and save the dialog in case of delegated access. The application based access will be authenticated immediately.
Now you can use this service connection in the configuration of the Intune data provider.