Authentication and Authorization Scenarios
Overview
Authentication is the process of obtaining identification credentials such as the name and password from a user and validating those credentials against some authority. If the credentials are valid, the entity that has submitted the credentials is considered an authenticated identity.
Authentication in Matrix42 Enterprise Service Management is divided into three steps:
- Attempt to authenticate the user by using Windows credentials (single sign-on process).
- Authentication of the user by using a configured membership provider and credentials supplied on the login form.
- Synchronization of user roles with Active Directory.
The diagram shows the authentication process at the top level.
Single Sign-On
The single sign-on functionality allows registered users to access Matrix42 without specifying user credentials. When a user accesses any page of Matrix42 Enterprise Service Management, the system tries to authenticate this user automatically. To provide the single sign-on, the system relies on Integrated Windows authentication. The IIS web site that hosts Matrix42 Enterprise Service Management is configured to use forms authentication, but there is one page (SPS/Logon/CredentialsScreeningRequiresAuthentication.aspx) that is configured to use Integrated Authentication. Internally, this page is used to emulate the single sign-on functionality. The single sign-on is best suited for an intranet environment, where both user and Web server computers are in the same domain. The diagram shows how the single sign-on works.

Configuration
By default, the single sign-on functionality is enabled. To disable it, use the update4u.SPS.Console-disableWindowAuthentication setting in the sps.config file or, starting from ESMP v.12.1.1 in PDRDwpConfigurationClass (see also Advanced System Settings).
Limitations
The single sign-on functionality has the following limitations:
- The Integrated Windows authentication does not work over HTTP proxy connections, and therefore, the single sign-on does not work as well.
- The user should be logged on to the local computer as a domain user of the same Windows domain in which the Web Server is located.
The Integrated Windows authentication does not initially prompt for a user name and password. The current Windows user information on the client is used for the Integrated Windows authentication. If the initial authentication exchange fails to authorize the user, the web browser prompts the user for a Windows account user name and password which are then processed using the Integrated Windows authentication. If, however, the user has logged on to the local computer as a domain user, then no authentication is required to access a network computer in that domain.
- The user should access the system using Local Intranet or Trusted Sites zones in IE. By default, IE allows automatic logon in the Intranet zone only.
Login
Matrix42 Enterprise Service Management uses standard ASP.NET forms authentication based on membership providers. The system provides two custom membership providers:
- M42MembershipProvider is used for both Windows authentication (trusted domains only) and authentication against internal domains.
- NDSMembershipProvider is used for authentication against LDAP servers, such as Active Directory, Novell eDirectory or Lotus Domino.
By default, the system is configured to use M42MembershipProvider. It means that, by default, it supports authentication against Windows domains (trusted domains only) and internal domains. In addition, standard ASP.NET ActiveDirectoryMembershipProvider could be used to authenticate users against Active Directory.

Supported Scenarios
Windows Domains
The system supports authentication against Windows domains for users registered in the Matrix42 Enterprise Service Management database using the M42MembershipProvider custom membership provider. By default, the membership provider is able to authenticate users for the Windows domain where the Web server is located and all Windows domains that have a trust relationship with this domain. The configuration file is located in svc\Config\Membership.config
Internal Domains
An internal domain is a virtual domain that exists in Matrix42 Enterprise Service Management. The system supports authentication against internal domains using the M42MembershipProvider custom membership provider.
Configuration (Default Configuration)
File: svc\Config\Membership.config
<membership defaultProvider="M42Provider" >
<providers>
<clear/>
<add name="M42Provider"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
</providers>
</membership>
Non-Trusted Windows Domains
For Matrix42 Enterprise Service Management to support authentication against non-trusted Windows domains, the additional configuration is required.
Configuration
To support authentication for an additional non-trusted Windows domain (MyDomain), the following configuration should be done in svc\Config\Membership.config:
- Configure standard ASP.NET ActiveDirectoryMembershipProvider for the MyDomain additional domain.
File: svc\Config\Membership.config
<membership defaultProvider="M42Provider" >
<providers>
<clear/>
<add name="M42Provider"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
<add name="MyDomain" type="Matrix42.Services.Security.OLdapMembershipProvider, Matrix42.Services.Security"
domain="MyDomain" server="{Domain Controller IP}:389" templateDN=""/>
</providers>
</membership>
templateDN - the template for the construction of the user AD Distinguished Name. If the parameter is not set the DN is generated automatically like "CN={User Name}, CN=Users, DC={domain}". If the user is not in the catalog "Users" template can be used, like templateDN="CN={0},OU=UsersCatalog,DN=DomainName"
- Switch off UUX login form auto-login
Automatic login with the interactive user Windows Identity in case of the Non-trusted domains does not work and make sense to be disabled. It can be done in the <ApplicationFolder>\WM\config.json, set the property "autologin" to "false"
"authentication": {
...
"params": {
"autoLogin": false
}
...
}
To perform authentication, the MyDomain\ServiceAccount account should have read access for all required objects in Active Directory.
For more information about configuring ActiveDirectoryMembershipProvider, see the following:
How To: Use Membership in ASP.NET 2.0
How To: Use Forms Authentication with Active Directory in Multiple Domains
Non-Windows Domains
For Matrix42 Enterprise Service Management to support authentication against non-Windows domains, such as Novell eDirectory, an additional configuration is required. These domains should be defined explicitly in the web.config file.
Configuration
To support authentication for an additional non-Windows domain (MyDomain), the following configuration should be done in web.config:
- Add an LDAP connection string: MyDomainService.
File: svc\Config\connectionStrings.config
<connectionStrings>
<add name="MyDomainService" connectionString="server:port" />
</connectionStrings>
- Configure NDSMembershipProvider for the MyDomain additional domain. Please note that the name of the provider must be the same as the target domain name.
File: svc\Config\Membership.config
<membership defaultProvider="M42Provider" >
<providers>
<clear/>
<add
name="M42Provider"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
<add
name="MyDomain" type="update4u.SPS.Security.Authentication.NDSMembershipProvider, update4u.SPS.Security"
connectionStringName="MyDomainServer"
searchFilter="(&(objectClass=Person)(sAMAccountName={0}))"
rootDN="OU=Store Users,DC=MYDOMAIN,DC=COM"
proxyDN="MyDomain\ServiceAccount"
proxyPassword="ServiceAccountPassword"/>
</providers>
</membership>
To perform authentication, the MyDomain\ServiceAccount proxy account should have read access for all required objects in Active Directory.
A search filter is used during authentication, but it is not used by the proxy user to establish connection to the domain. By default, searchFilter is “(&(objectClass=Person)(cn={0}))”. proxyDN could also be equal to the CN (canonical name) of the corresponding account. For example, proxyDN=“Service Account” instead of ServiceAccount.
Multiple Domains
It is possible to configure Matrix42 Enterprise Service Management to support more than one additional domain. It could be useful if several non-trusted Windows domains or several non-Windows domains should be supported.
Configuration
To support authentication for an additional non-Windows domain (MyDomain), the following configuration should be done in web.config:
- Add an LDAP connection string for every directory server.
File: svc\Config\connectionStrings.config
<connectionStrings>
<add name="MyDomainService1" connectionString="server:port" />
<add name="MyDomainService2" connectionString="server:port" />
</connectionStrings>
- Configure several membership providers for additional domains: MyDomain1 and MyDomain2. Please note that the name of the provider must be the same as the target domain name.
File: svc\Config\Membership.config
<membership defaultProvider="M42Provider" >
<providers>
<clear/>
<add
name="M42Provider"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
<add
name="MyDomain1" type="update4u.SPS.Security.Authentication.NDSMembershipProvider, update4u.SPS.Security"
connectionStringName="MyDomainServer1"
searchFilter="(&(objectClass=Person)(sAMAccountName={0}))"
rootDN="OU=Store Users,DC=MYDOMAIN1,DC=COM"
proxyDN="MyDomain1\ServiceAccount"
proxyPassword="ServiceAccountPassword"/>
<add
name="MyDomain2" type="System.Web.Security.ActiveDirectoryMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="MyDomainService2"
enableSearchMethods="true"
attributeMapUsername="sAMAccountName"
connectionUsername="MyDomain2\ServiceAccount"
connectionPassword="ServiceAccountPassword"/>
</providers>
</membership>
Default Domain
A default provider is used for authenticating users when a domain name is not specified (not fully qualified user name: MyAccountinstead of MyDomain\MyAccount). A default membership provider could be set using the defaultProvider attribute of the membership element in the web.config file.

Configuration
It addition to specifying M42MembershipProvider as a default provider, you must also add an entry for every supported domain, including trusted Windows domains and internal domains.
File: svc\Config\Membership.config
<membership defaultProvider="MyDomain" >
<providers>
<clear/>
<add
name="MyLocalDomain"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
<add
name="MyWinDomain"
type="update4u.SPS.WebUI.Components.Security.M42MembershipProvider, update4u.SPS.WebUI.Components"/>
<add
name="MyDomain" type="update4u.SPS.Security.Authentication.NDSMembershipProvider, update4u.SPS.Security"
connectionStringName="MyDomainServer"
searchFilter="(&(objectClass=Person)(sAMAccountName={0}))"
rootDN="OU=Store Users,DC=MYDOMAIN,DC=COM"
proxyDN="MyDomain\ServiceAccount"
proxyPassword="ServiceAccountPassword"/>
</providers>
</membership>
Membership Providers
M42Membership Provider
M42MembershipProvider is used to authenticate users registered in the Matrix42 Enterprise Service Management database against both Windows and internal domains.

Matching Criteria
- Windows Domain
(SPSAccountClassBase.AccountName = @username OR SPSAccountClassAD.NBAccountName = @username) AND (SPSAccountClassBase.DomainName = @domain OR SPSAccountClassAD.NBDomainName = @domain) AND SPSAccountClassAD.DenySuiteLogon = false
- Internal Domain
SPSADDomainClassBase.IsInternal = true AND SPSAccountClassBase.AccountName = @username AND SPSAccountClassAD.InitialPassword = @password AND SPSADDomainClassBase.DomainName = @domain AND SPSAccountClassAD.DenySuiteLogon = false
NDSMembershipProvider
NDSMembershipProvider is used for authentication against LDAP servers, such as Active Directory, Novell eDirectory and Lotus Domino, by using LDAP protocol.
Matching Criteria
The default LDAP search filter is (&(objectClass=Person)(cn={0})),but it is possible to change it using the searchFilter attribute. For example, for Active Directory the following search filter could be used (&(objectClass=Person)(sAMAccountName={0})).
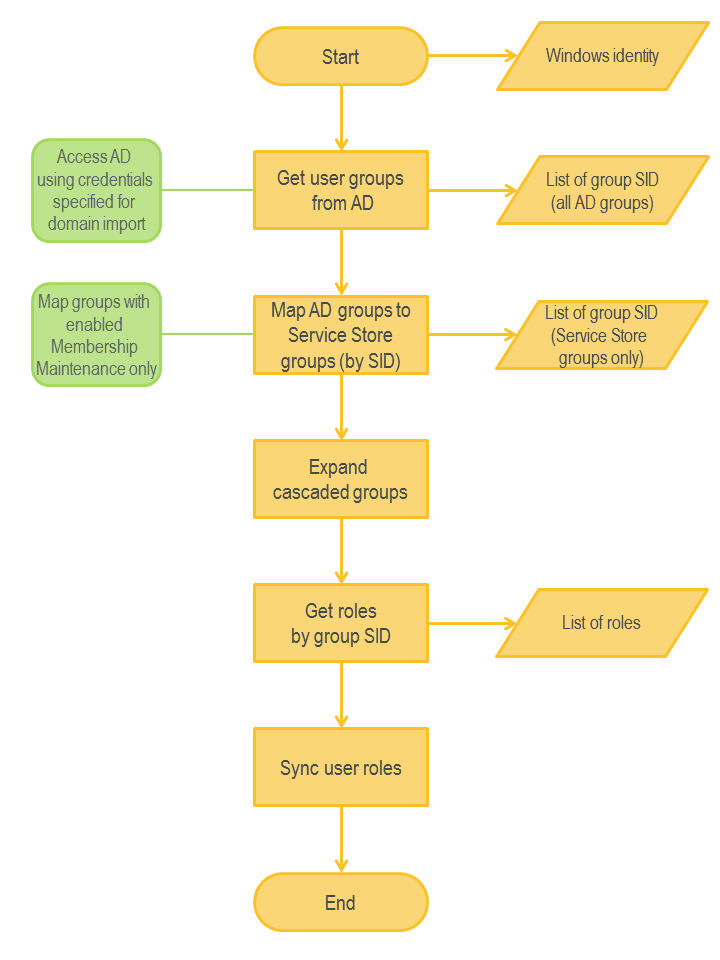
User Role Synchronization
The system provides functionality for synchronizing user role membership with Active Directory. A role could be associated with Active Directory group by using SID. If group membership has been changed in AD, the system changes role membership accordingly. To support user role synchronization, domains should be properly configured in Matrix42 Enterprise Service Management. By default, user role synchronization is done using import credentials of the corresponding domain. If import credentials are not defined, this operation is done under service account credentials. Please note that this account should have read access for all required objects in Active Directory. User role synchronization is done only for groups registered in the Matrix42 Enterprise Service Management database.


