Secure Token Service configuration
Overview
When a client requests access to an application, the application does not authenticate the client directly, for instance, by validating the client's login credentials against an internal database. Instead, the application uses a Secure Token Service (STS) mechanism that authenticates the client and grants it a security token.
The metadata and authentication settings of the application relying on STS uses the tokens for validating the users and controlling their access to the specific areas of the application.
The token consists of a set of encrypted JSON data records that include multiple elements, to name a few:
- the identity and group membership of the client (user name, user ID, user role, and granted application access);
- information regarding the lifetime of the token;
- the issuer of the token;
- etc.
The token issuing mechanism requires end-user interaction, i.e. the user provides credentials for the login.
Each time the user submits valid login credentials on the application login page, the authentication server presents the token to the user to gain access to the resources provided by the application. Once the user is logged in, each subsequent request will include the token, allowing the user to access routes, services, and resources that are permitted with that token:
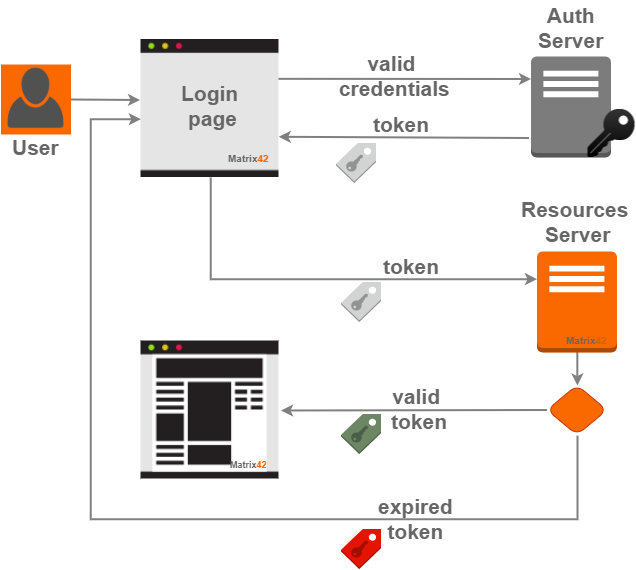
Additionally, such an approach enhances data transfer security by limiting the token lifetime to a specific period. When the token expires, the user has to re-login and a new security token is issued automatically.
The token is protected from manipulation with a strong encryption algorithm that uses a unique secret string generated during the Matrix42 installation process.
STS settings during system install
The Secure Token Service is enabled by default during the system installation process on the Security Configuration step.
Starting from DWP v.12.1.1 the configuration can be checked as follows:
- To verify if the STS is enabled, check the value of the update4u.SPS.Console-enableSts Key in PDRDwpConfigurationClass table in the database.
- Encryption strings are moved from the STS configuration file to SPSGlobalConfigurationClassSecurity database table.
Managing token lifetime
User session
Automatically issued for the end-user session token has an expiration date. Each time the token expires user is redirected to the application's login page.
The Administrator can edit the secure token lifetime in the Global System Settings: Security section by adjusting the Session lifetime in hours.
The default token lifetime is applied for the end-users session only.
Public API requests
Although the encryption mechanism is common both for the end-user sessions and the public API requests, the token issuing and lifetime for the latter is managed manually in the dedicated area of the Administration application → Integration → Web Services Tokens page.