Entra ID Integration VI: App Protection Policies
App Protection Policies
App protection policies are rules which will help to increase the security for your organization's data, even when the devices are not managed with Silverback. The app protection policies are part of the Microsoft Framework integrated within the Graph API and can be configured through Silverback to extend your current and existing device configuration policies with app level security policies and apply the policies on unmanaged devices. These policies or app rules ensures that the organizations' data remains safe or contained in managed applications. As an example, these policies will help to add additional protections on a per-app level like enforcing an additional password, preventing from copy & paste to unmanaged applications or prevent access to corporate on devices depending on the operating system version.
What is the benefit
- You can add app level protection policies to prevent intentional and unintentional data loss
- Protect corporate data that is accessed from unmanaged devices
- Add data loss prevention controls, like cut, copy, paste, and save-as restrictions. These settings determine how users interact with data in the apps.
- Define access policies like PIN and credential requirements that users must meet to access apps in a work context.
- Set sign-in security requirements like minimum App conditions and device conditions
How it works
- By adding an application to Microsoft Entra ID with API permissions Silverback will gain access to the Graph API
- The application information will be added into Silverback and the App Protection Policy feature will be activated
- You configure App Protection Policies and assign them to your Microsoft Entra ID Groups
- App Protection Policies will be applied through Silverback to Microsoft Intune and will be synchronized regularly
- Whenever a user logs into any protected application (unmanaged or managed devices) with a work or school account, the configuration will be applied
- The configuration will be only take affect to the work or school account. If a personal account is signed into the app, the data is untouched.
Android and Samsung devices requires the Company Portal app installed on the device without any further actions. Please ensure that the users are capable to install the app.
What you need
- Successful accomplished Microsott Entra ID Integration Guide I and II
- Access to Microsoft Entra ID
- A license model from Microsoft that include Microsoft Intune
How to configure it
- Login to your Azure Portal
- Navigate to Microsoft Entra > Managed > Mobility (MDM and WIP)
- Select your Silverback application and click Custom MDM application settings
- Navigate to API Permissions
- Click +Add a permission
- Select Microsoft Graph
- Select Application permissions
- Expand DeviceManagementApps and enable DeviceManagementApps.ReadWrite.All
- Expand Group and enable Group.Read.All
- Click Add permissions
- Click Grant admin consent for your organization
- Select Application permissions
- Open your Silverback Management Console
- Navigate to Admin
- Select Microsoft Entra ID
- Enable App Protection by enabling the checkbox
- Define a period for how often Silverback performs a sync with the Graph API
- Press Save
- Confirm with OK
- Confirm again the the settings saved successfully
- Navigate to App Portal
- Select MAM
- Click New App Protection Policy
- Enter a Display Name, e.g. Microsoft Outlook on iOS/iPadOS
- Select a Platform e.g. Android
- Enter a description (optional)
- Click Save and Process
- Under Apps, select Assign Apps
- Select e.g. Microsoft Outlook
- Click Attach Select Apps
- Confirm with OK
- Click Save and Proceed
- Under Data
- Change Restrict cut, copy, and paste between other apps to Blocked
- Click Save and Proceed
- Under Access
- Enable PIN for access
- Click Save and Proceed
- Under Conditions
- Enter as Min OS version (warning) e.g. 13.0
- Click Save and Proceed
- Under Assignments
- Click Assign Group
- Select your desired Group
- Click Attach Selected Groups
- Confirm with OK
- Click Save and Close
Review your configuration
- Open your Microsoft Endpoint Manager admin center
- Select Apps
- Select App protection policies
- Your previously created Polices should be listed here
- Select your policy and check the properties
User Experience
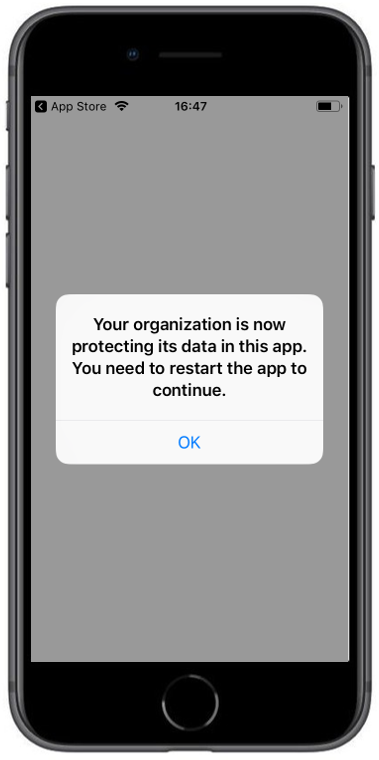
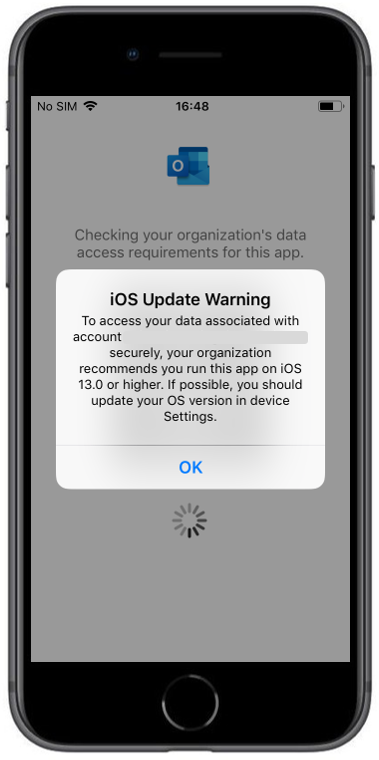
The following screenshots demonstrates the behavior of the previously created App Protection Policy.
 |
 |
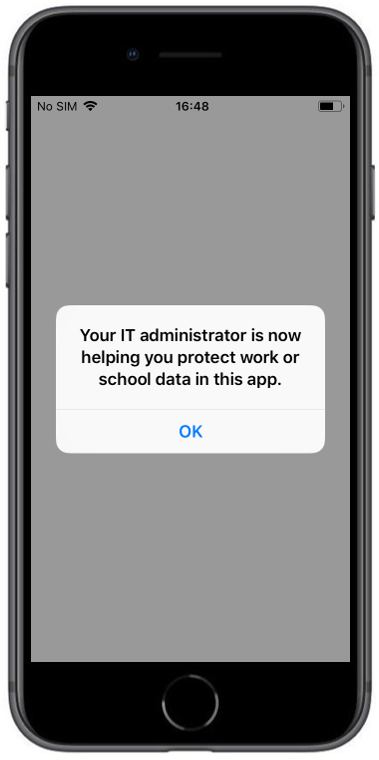 |
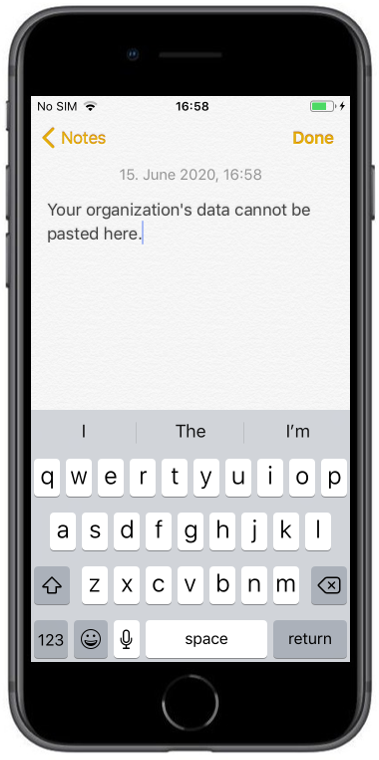
| After login with the corresponding Office365 Account the protection information is shown. You need to restart the application afterwards | When the operating system is lower as the configured one in the App Protection Policy you will see the following warning | After pressing OK you will see the notification that this app is protected |
 |
 |
|
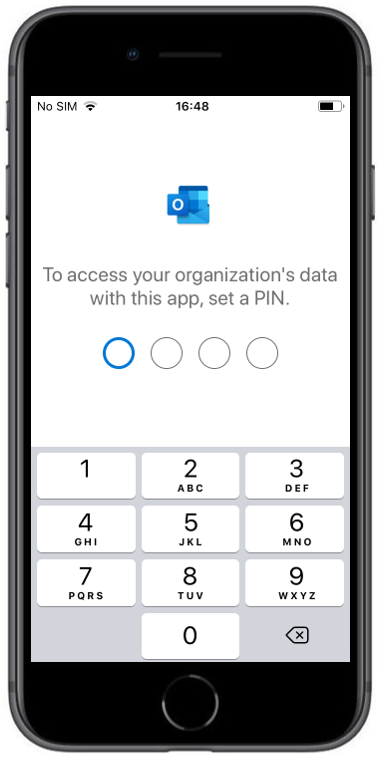
| Due to the enabled PIN access within the configuration, you will get forced to set a PIN for accessing the corporate data | When you try to copy and paste content from an e-mail you will see the following information. |