Entra ID Integration I: Configure Microsoft Entra ID
Configure Microsoft Entra ID
The first part of the Microsoft Entra Integration is to create a specific Mobility (MDM and WIP) application in your Microsoft Entra ID. For Cloud Customers, the process starts already one step before as they are required first to validate their Silverback SaaS URL as a verified or trusted domain in their Microsoft Entra ID. The Mobility (MDM and WIP) applications defines as an example, which users are allowed to enroll via Autopilot or Microsoft Entra join and where or to which Silverback instance the devices should be enrolled. During the process, we will note down two identifiers and one access key, that will be added later into Silverback to link the application with their specific permissions. Depending on the granted application permissions, you can integrate additionally and next to Autopilot or Microsoft Entra join, the App Protection policy feature, which has a dedicated part in the Entra ID Integration Guide.
Prerequisites
- Administrative Account for the Microsoft Entra ID to configure the integration with Silverback
- Administrative Account for the Silverback Management Console
- Microsoft Entra ID Premium P1 or greater, or any Bundle which includes this license.
Preparation for Cloud Customers
Microsoft requires for single tenant applications and their AppID URI the usage of verified domains. Requests to add/update AppID URI (identifierUris) will validate that the domain in the value of URI is part of the verified domain list in your Azure Tenant. With this, Microsoft prevents to add an AppID URI containing a domain name that isn't in your verified domain list. As the AppID URI for cloud customers logically are not verified by default in your Azure Tenant (as your SaaS URL is part of the m42cloud.com domain), you will need to verify the domain first. This means that cloud customers are required to perform the domain verification upfront for your Silverback SaaS instance. To perform this validation, cloud customers are required to perform the following steps:
- Open Azure Portal and login as an Administrator
- Navigate to Microsoft Entra ID
- Expand Manage
- Select Custom Domains
- Click +Add custom domain
- Enter your Silverback SaaS instance URL, e.g. silverback001.m42cloud.com
- Press Add domain
- Copy the Destination or point to address to your Clipboard
- Create a support incident and provide inside the description your Silverback SaaS Instance URL and the TXT Record
- Wait until Matrix42 will add the TXT Record and provide you the information to Verify the domain
- Proceed with Create Application
Add your Mobility (MDM and MAM) application
Create Application
- Open Azure Portal and login as an Administrator
- Navigate to Microsoft Entra ID
- Expand Manage
- Navigate to Mobility (MDM and WIP)
- Click + Create your own application
- Set a given name to the application (e.g. Silverback)
- Click Create
- Wait until Silverback application is added successfully
- Proceed with Configure Application
Your application will be added as App Registration and you can find it under Microsoft Entra ID > Managed > App Registrations.
Configure Application
The MDM User Scope settings are dedicated for the usage of Autopilot or Microsoft Entra join. When you select All, all users that performing an enrollment with Autopilot or with Microsoft Entra join will be automatically routed to your Silverback instance, defined in the Terms of Use and Discovery. In case you want to allow the enrollment only for some users or some groups, ensure to select Some and enter the group name.
- Set MDM User scope:
- Choose “All” or
- Choose “Some” and select “groups”
- Change MDM terms of use URL to e.g. https://silverback.imagoverum.com/EnrollmentServer/TermsOfUse
- Change MDM discovery URL to e.g. https://silverback.imagoverum.com/EnrollmentServer/Discovery.svc
- Press Save
- Wait until the changes are saved
- Now, press the link in the information Manage permission for this custom MDM application in App Registrations
Grant Permissions
- Click Add a permission
- Select Microsoft Graph
- Select Application permissions
- Select the following permissions depending of your purpose
| Group | Permission | Purpose |
|---|---|---|
| Devices | Device.ReadWrite.All | Windows Autopilot & Microsoft Entra join. |
| User | User.Read.All | Windows Autopilot & Microsoft Entra join |
| Group | Group.Read.All | App Protection Policies |
| DeviceManagementApps | DeviceManagementApps.ReadWrite.All | App Protection Policies |
- Press Add permissions
- Click Grant admin consent for your organization, e.g. Imagoverum
- Confirm with Yes
Copy Identifiers
- Navigate to Overview
- Copy the following values to any Text Editor (e.g. Notepad++)
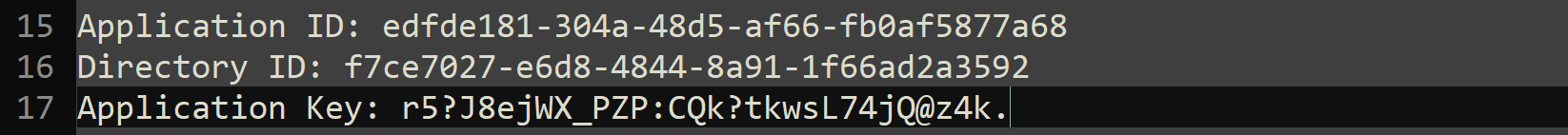
- Application (client) ID: e.g. edfde181-304a-48d5-af66-fb0af5877a68
- Directory (tenant) ID: e.g. f7ce7027-e6d8-4844-8a91-1f66ad2a3592
Create Application Key
- Expand Manage
- Select Certificates & secrets
- Click New client secret
- Enter as description e.g. application_key
- Configure your expiration date for the key, e.g. 24 months
- Click Add
- Copy the new client secret value to your Text Editor (e.g Notepad++)
You won't be able to retrieve it after you leave this blade
Add a reminder into your calendar for the key expiration date. You will need to create a new key before the key will expire.
Change Application ID URI
- Navigate to Expose an API
- Click Edit next to Application ID URI
- Change the URI to the URL of your Silverback Server, e.g. https://silverback.imagoverum.com
- Press Save
- Your Microsoft Entra ID Configuration is now finished
Review IDs and Application Key
- During the process you should have noted down 3 values
- Application ID
- Directory ID
- Key Value
Next Steps
- Move forward to import these values into Silverback: Entra ID Integration II: Configure Silverback